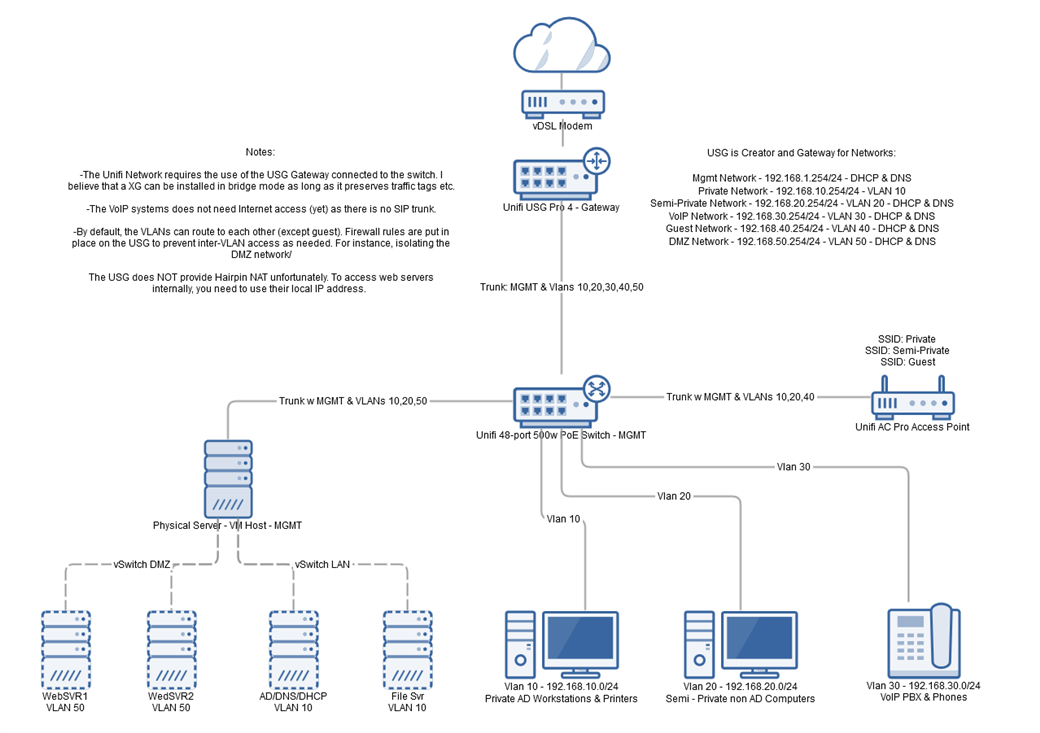
I am trying to integrate an XG210 into an existing network. The network is a full Ubiquiti Unifi setup and has multiple VLANs set up between the gateway and the switch. I would think I could place the XG in line on a trunk connection between the switch and the gateway. The end goal is to be able to filter the individual networks separately in regards to web filtering and scanning etc.
I have asked this question before and got a lead: "You would have to set up virtual interfaces for all the VLANs and bridge them accordingly." But was unsuccessful in making this work.
I am new to the XGs having come from sonicwall, so I am still a bit green when it comes to using the XG software. Can anyone give me a bit more detailed instructions, or at least a link or two to something to help me figure this out? Any help will be appreciated.
This thread was automatically locked due to age.