Referring to this thread discussion. MFA on web authentication
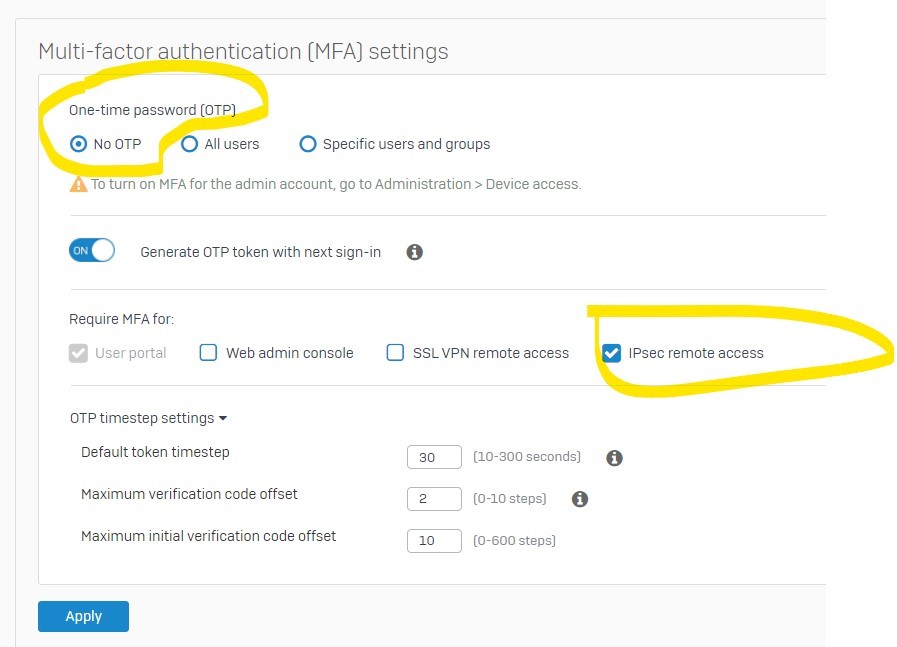
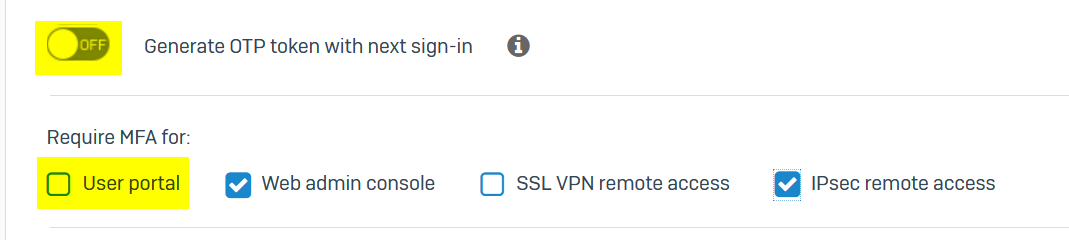
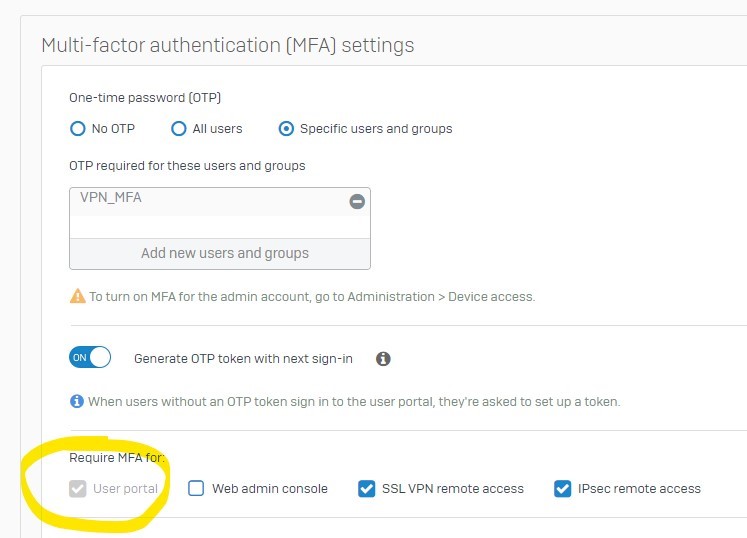
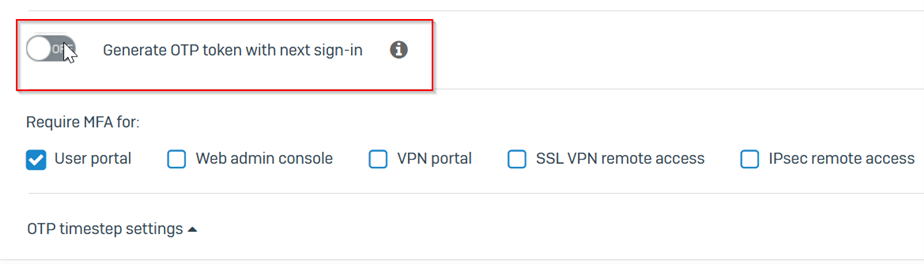
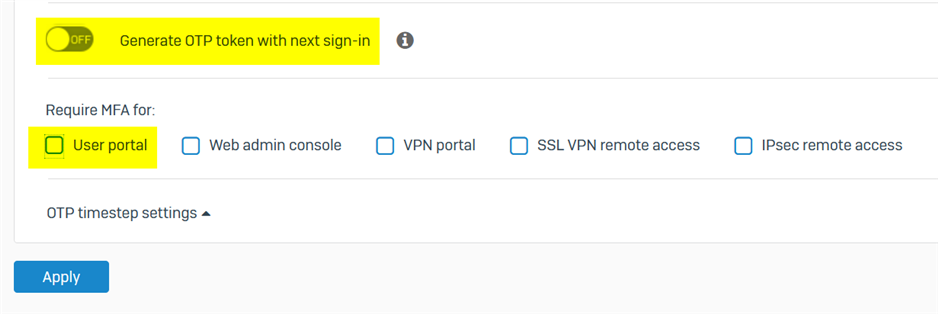
When this setting is used, MFA is not prompted for client VPN users. VPN users can login with username and password only. No MFA required.
When "No OTP" is changed to "Specific Groups" MFA is asked for both captive portal and VPN users.
How to enable MFA for VPN users alone, not for captive portal users.
This thread was automatically locked due to age.