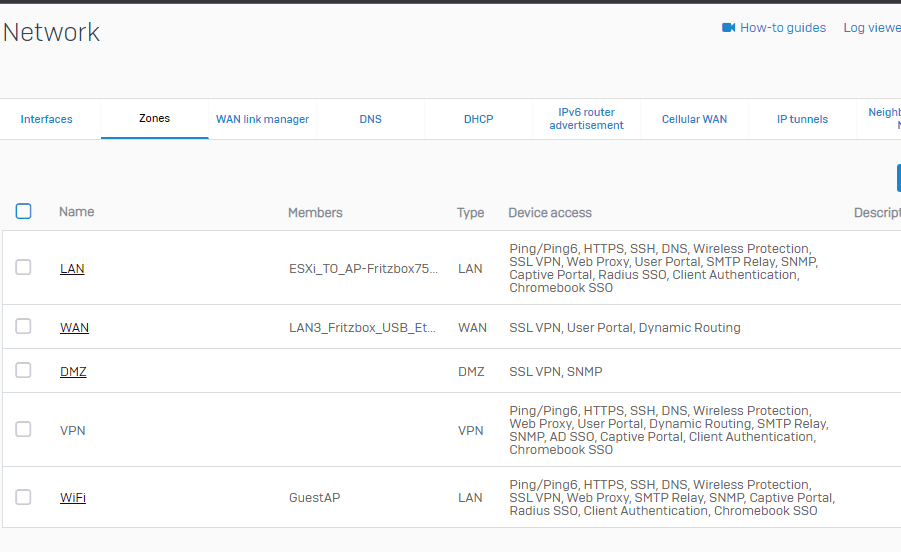
XG firmware: SFOS 19.0.1 MR-1-Build365
Hello,
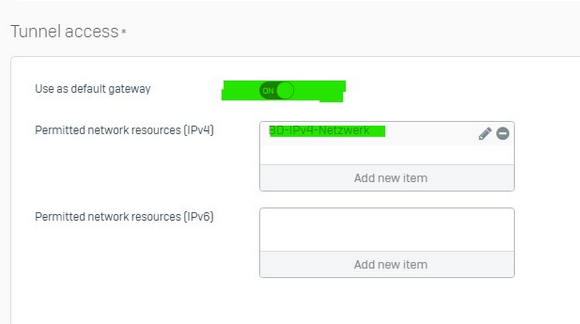
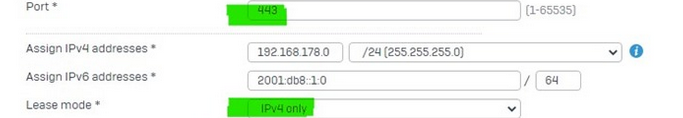
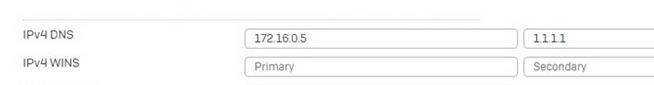
Internet access in the SSL VPN full tunnel breaks off after about 15 minutes during use. Only the firewall management page can be accessed. Internal servers or IPs cannot be reached!
Nothing can be seen in the log (firewall, web protection)!
So the tunnel is not separated, only the Internet access is terminated after 15 minutes without logging anything!
The whole thing was tested with Android 12, 13, OPENVPN version 2.5.036 and Sophos Connect version 2.2.75.0506!
can you please suggest what i could try to fix the problem?
Many Thanks
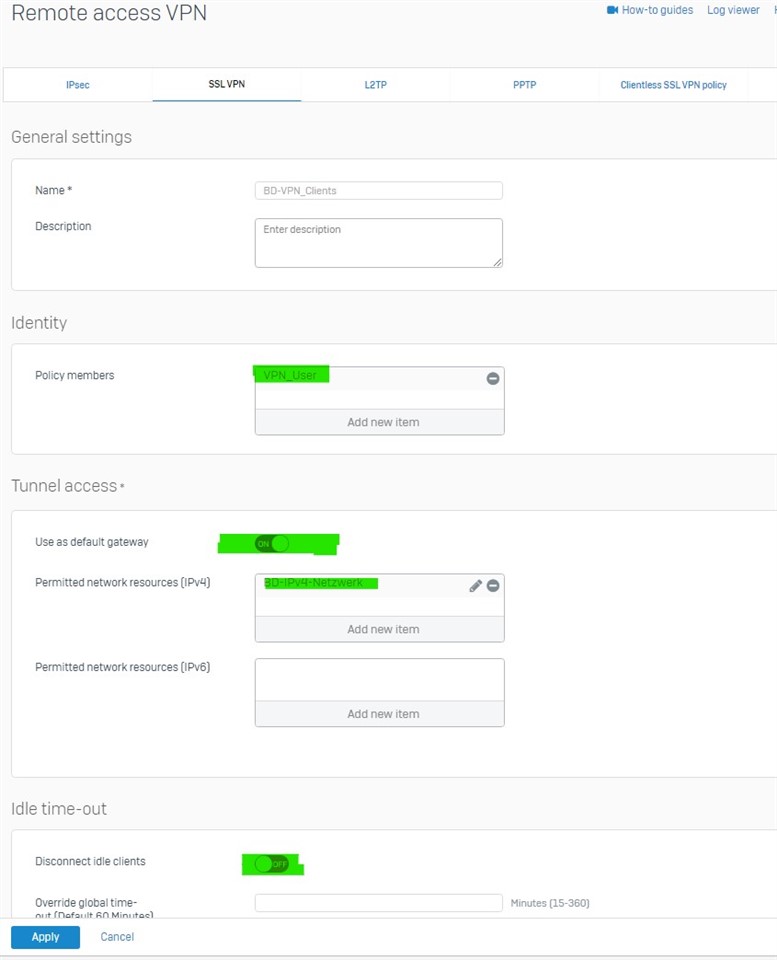
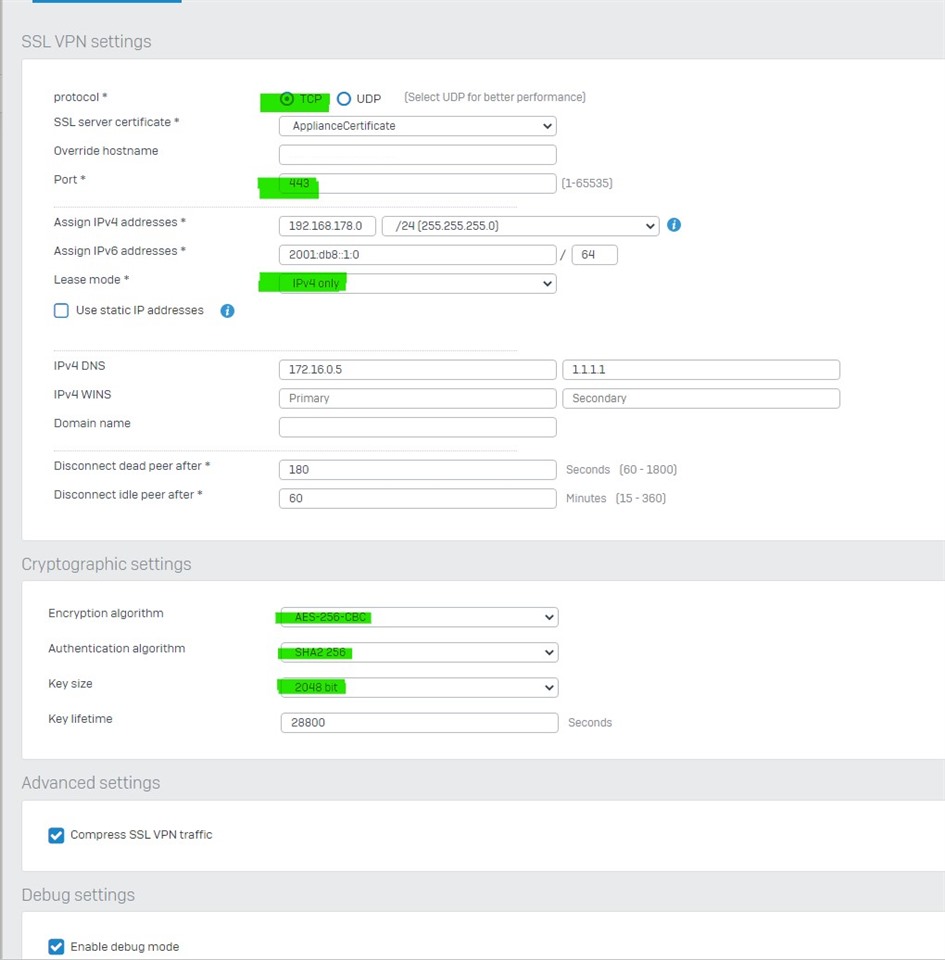
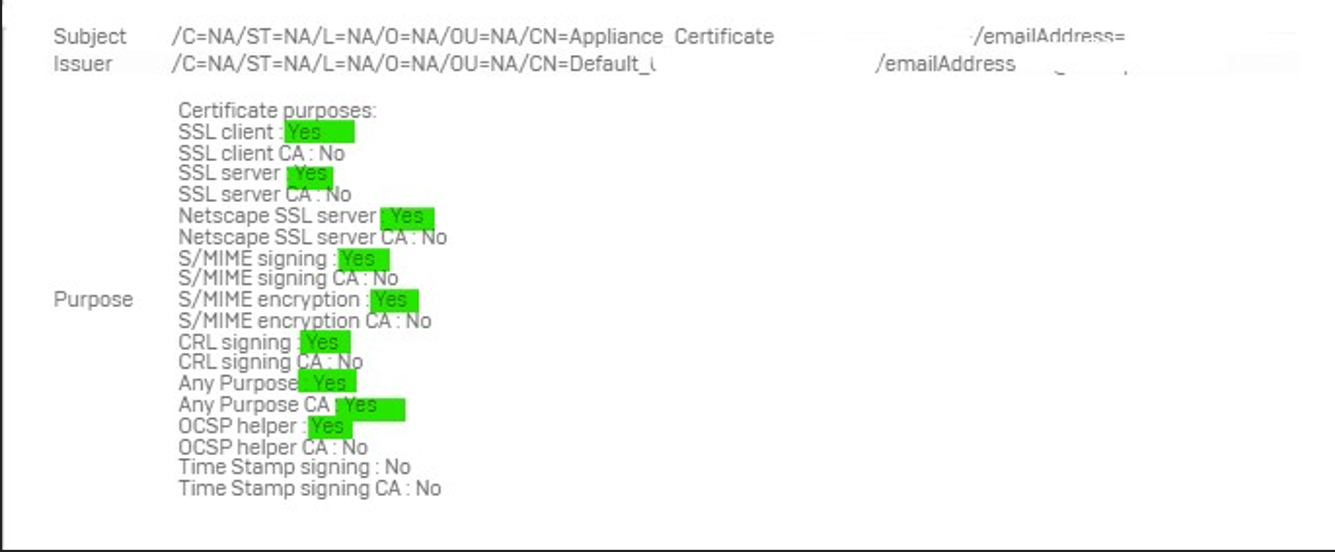
Certificate
This thread was automatically locked due to age.