Disclaimer: This information is provided as-is for the benefit of the Community. Please contact Sophos Professional Services if you require assistance with your specific environment.
Table of Contents
Overview
This Recommended Read goes over how to TCPdump on the Sophos Firewall
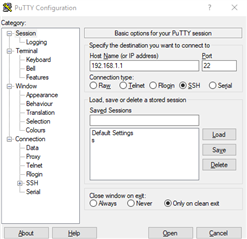
SSH to Sophos Firewall
First of all, get an SSH Session to your Sophos Firewall.
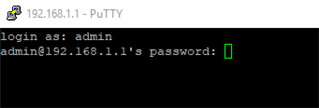
You'll have to use the "admin" to log in.
Switch to Advanced Shell and click 5.Device Management
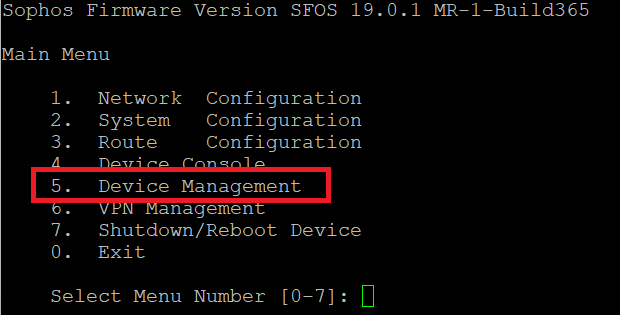
Then click 3.Advanced Shell
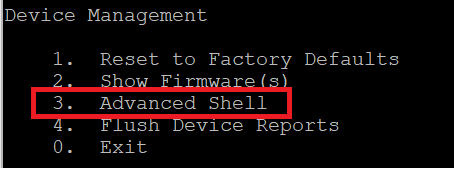
Perform TCPdump
We can now perform a tcpdump.
Refer to the man page of tcpdump for all kinds of filters.
https://www.tcpdump.org/manpages/tcpdump.1.html
But here are my "most used":
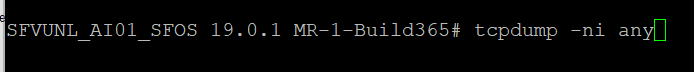
- tcpdump -ni any
You’ll see all the traffic on all Interfaces with all IPs.
I can't recommend this because you’ll see the SSH Traffic as well.
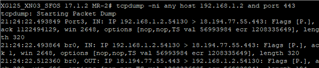
Filter the traffic with port PORTNUMBER and/or host IP_Address. Basically, you can use all kinds of logical connectives like and, or, nor and so on.
https://en.wikipedia.org/wiki/Logical_connective
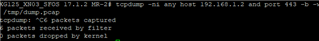
- tcpdump -ni any host 192.168.1.2 and port 443
![]()
You can also specify the port by replacing any with the wanted interface (Port3).
- tcpdump -ni Port3 host 192.168.1.2 and port 443
For better understanding, you can write the dump into a file with -b -w /tmp/dump.pcap
![]()
Download dump
Use PSCP to download this file.
https://community.sophos.com/kb/en-us/127647
And you can open this file with Wireshark for troubleshooting.
Filter to see all Pings
Let's get back to the Shell version.
If you want to see all pings, just use:
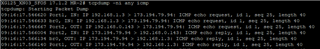
- tcpdump -ni any icmp
In my case, using a bridge, I will see the packets 3 times.
The packet arrives on Port1, will be transferred to br0, and leaves the appliance on Port2 with my MASQ ip.
Keep in mind, Sophos Firewall has to NAT the traffic, etc. pp. So basically 192.168.1.1 won’t be displayed on the WAN port and so on. Feel free to play with those filters in tcpdump and you’ll find nearly everything.
Updated doc guide Links
[edited by: Raphael Alganes at 2:46 PM (GMT -7) on 17 Oct 2024]