Good morning folks.
I have a sophos xg 135 firewall, and anti-virus endpoint also from sophos, we are all working in home office, via ssl VPN with client installed on all computers,
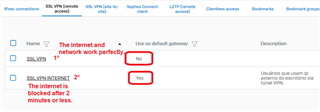
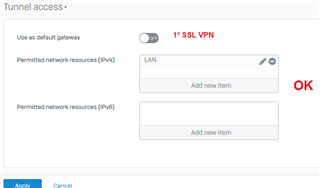
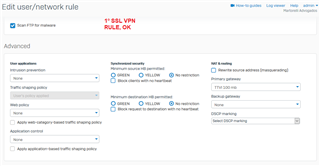
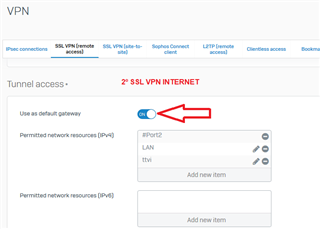
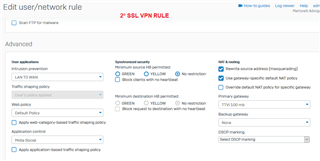
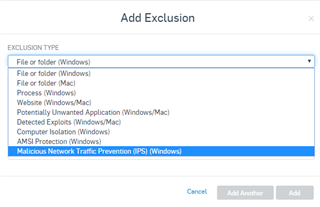
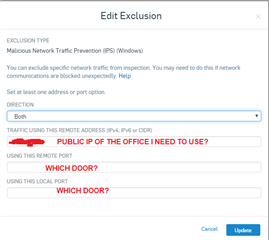
there was a need for a user to access a third party system with our public ip being in your home, I created a specific rule on the firewall and group on the VPN to
use our public ip as a gateway, so far everything is perfect, everything works, and even on any computer it works with any antivirus, but when I install the sophos
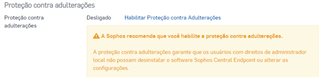
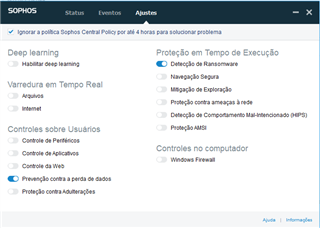
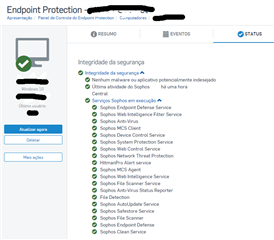
endpoint antivirus all internet traffic for , only the network continues, I already tried to disable all policies on the endpoint for 4 hours, but I still have access
to the internet blocked, I tried everything including searches in the forums, and I didn't get anything, I would like help to solve this problem.
Thank you
This thread was automatically locked due to age.