Overview
We are excited to announce early access program availability for our new ZTNA 2.0 product offering along with macOS client support.
ZTNA 2.0
ZTNA 2.0 enables ZTNA as a Service (ZTNAaaS), a new cloud-based ZTNA service offering that makes ZTNA deployments even easier. Instead of virtual gateways, it uses lightweight ZTNA connectors on the application side that establish connections to Sophos Cloud on port 443 to eliminate the need for firewall NAT configuration. This also enhances security by eliminating open firewall ports to the internet providing a further abstraction of the application services that ZTNA is providing access to. Sophos Cloud now brokers the secure connections between agents (or zero trust endpoints) and the ZTNA connectors. The new ZTNA connectors support the same platform support as our gateways: VMware, Hyper-V, and AWS.
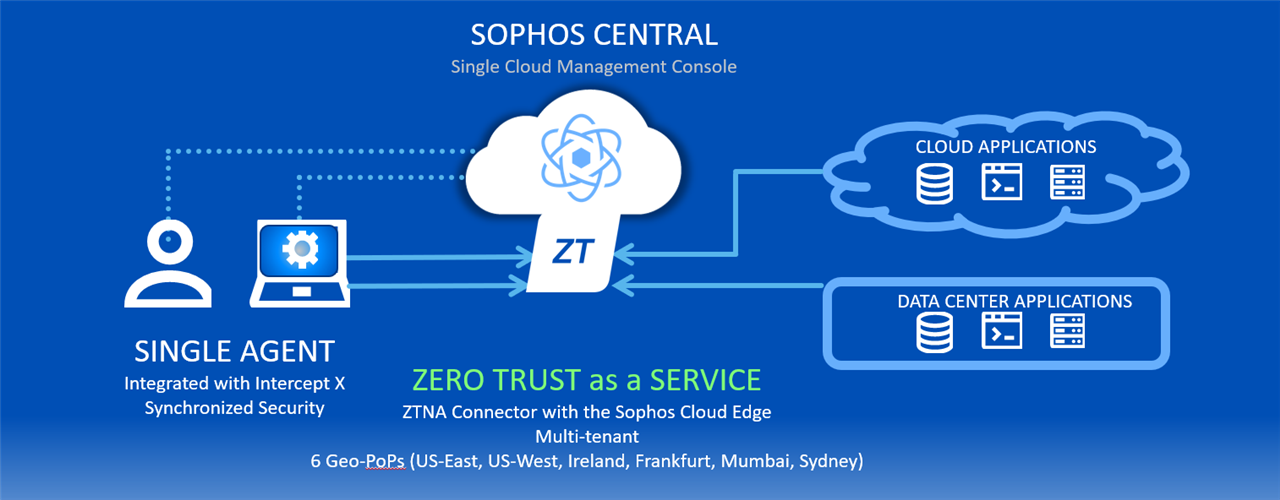
ZTNA 2.0 now offers Zero Trust Network Access as a Service through the Sophos Cloud
With ZTNA 2.0, you now have a choice of deployment models:
- ZTNA Gateway – works just as before, with your own data plane using virtual gateways on VMware, Hyper-V, or AWS platforms. This solution will be best for those customers who want to own the data plane and/or have concerns about latency via the ZTNAaaS points of presence (see below).
- ZTNA as a Service – with a Sophos Cloud data plane utilizing new lightweight ZTNA connectors that automatically connect to the Sophos Cloud on VMware, Hyper-V, or AWS platforms through regional Sophos cloud points of presence. This solution offers a more streamlined deployment without requiring any firewall configuration and makes the applications more invisible and secure as a result.
ZTNAaaS cloud points of presence (PoPs) are available in:
- Europe (Ireland and Frankfurt)
- North America (Ohio and Oregon)
- Asia Pacific (Mumbai and Sydney)
You can define your preferred cloud point of presence when setting up your connectors.
The new Sophos ZTNA cloud service is a HUGE milestone for us, and we couldn’t be more excited to share it with you. While Sophos ZTNA is the first to take advantage of this new cloud environment, it paves the way for additional SASE products that will be coming your way in the future.
See below for how to get started with early access to ZTNA as a Service.
macOS Support
We are also pleased to offer early access for Apple macOS agent support. Mac users can now get the same single-agent health-based secure access with Intercept X and Synchronized Security as Windows users. The ZTNA agent is supported on macOS Big Sur or later.

Getting Started
Getting started with these early access programs couldn’t be easier. In Sophos Central, join the Early Access Programs for both ZTNA as a Service and the macOS agent from the drop-down menu under your account name in the upper right of the console…

If you were a previous EAP member, that’s great, simply re-enrol to get access to this latest early access program. Your existing configuration will not be affected.
Then for ZTNAaaS, as highlighted below, from the Settings screen under ZTNA, make sure you Turn On ZTNAaaS and use the Feedback option within Sophos Central to leave your feedback or report any issues.
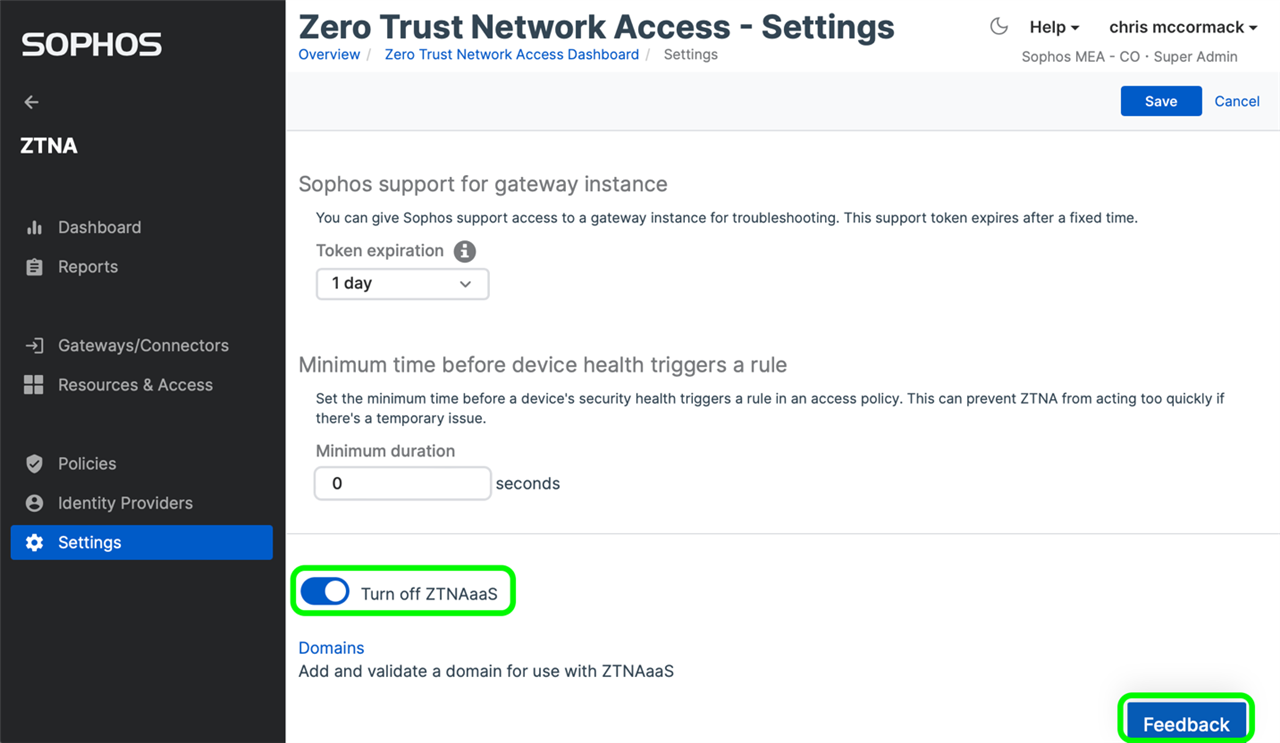
Review the documentation and be sure to drop by the community forums.
Known Issues
| Issue Key | Summary |
| NZT-4651 | After enrolling for the ZTNAaaS EAP, a page refresh is needed to view the ZTNA section in the left navigation panel. |
| NZT-4239 | ZTNA connector count is not displayed in the domain validation section. |
| NZT-4202 | A pop-up with alias domain details is not displayed after mapping an agentless resource with a connector. Alias domain details are displayed on the connector summary page |
| NZA-972 | macOS machine with ZTNA agent installed and running Monterey when upgraded to Ventura could encounter a situation where ZTNA agent status shows "Not Configured". The workaround is to reboot the machine once. |
| NZA-978 | On macOS Ventura, if ZTNA applications are not accessed for seven days, the secure tunnel with the ZTNA gateway gets reset. The workaround is to reset the session information from the troubleshooting section on the agent. |

