Since this week me and my colleagues cannot upload files to ftp.sophos.com:990 over explicit TLS
happens to 195.171.192.29 and 195.171.192.30
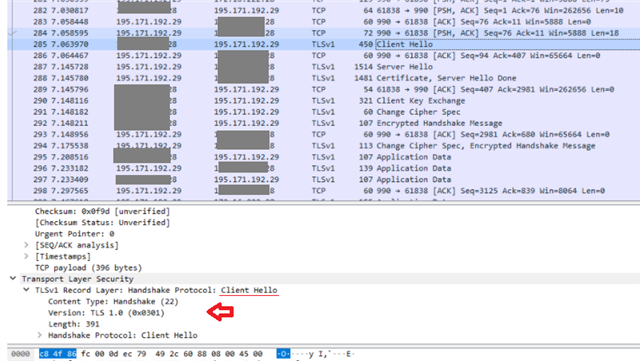
Probably caused by Sophos Servers only offering TLS 1.0
Using filezilla latest version 3.56.0 with GNUTLS 3.7.2
Error:
Fehler: Verbindungsversuch durch Benutzer unterbrochen Status: Warnung: Der gewählte Port wird üblicherweise von einem anderen Protokoll verwendet. Status: Auflösen der IP-Adresse für ftp.sophos.com Status: Verbinde mit 195.171.192.29:990... Status: Verbindung hergestellt, warte auf Willkommensnachricht... Status: Initialisiere TLS... Fehler: GnuTLS-Fehler -8: A packet with illegal or unsupported version was received. Status: Verbindungsversuch fehlgeschlagen mit "ECONNABORTED - Verbindung abgebrochen". Fehler: Herstellen der Verbindung zum Server fehlgeschlagen
129 14:16:39,544877 my.ipaddress 195.171.192.29 TCP 52402 990 66 52402 → 990 [SYN] Seq=0 Win=64240 Len=0 MSS=1460 WS=256 SACK_PERM=1
134 14:16:39,606162 195.171.192.29 my.ipaddress TCP 990 52402 66 990 → 52402 [SYN, ACK] Seq=0 Ack=1 Win=5840 Len=0 MSS=1420 SACK_PERM=1 WS=128
135 14:16:39,606467 my.ipaddress 195.171.192.29 TCP 52402 990 54 52402 → 990 [ACK] Seq=1 Ack=1 Win=262656 Len=0
136 14:16:39,653103 195.171.192.29 my.ipaddress TCP 990 52402 129 990 → 52402 [PSH, ACK] Seq=1 Ack=1 Win=5888 Len=75
137 14:16:39,653285 my.ipaddress 195.171.192.29 TCP 52402 990 64 52402 → 990 [PSH, ACK] Seq=1 Ack=76 Win=262400 Len=10
139 14:16:39,687157 195.171.192.29 my.ipaddress TCP 990 52402 60 990 → 52402 [ACK] Seq=76 Ack=11 Win=5888 Len=0
140 14:16:39,687333 195.171.192.29 my.ipaddress TCP 990 52402 72 990 → 52402 [PSH, ACK] Seq=76 Ack=11 Win=5888 Len=18
141 14:16:39,689429 my.ipaddress 195.171.192.29 TLSv1 52402 990 488 Client Hello
142 14:16:39,734847 195.171.192.29 my.ipaddress TLSv1 990 52402 1474 Server Hello
143 14:16:39,734982 195.171.192.29 my.ipaddress TCP 990 52402 1474 990 → 52402 [ACK] Seq=1514 Ack=445 Win=6912 Len=1420 [TCP segment of a reassembled PDU]
144 14:16:39,735032 my.ipaddress 195.171.192.29 TCP 52402 990 54 52402 → 990 [ACK] Seq=445 Ack=2934 Win=262656 Len=0
145 14:16:39,735074 195.171.192.29 my.ipaddress TLSv1 990 52402 101 Certificate, Server Hello Done
146 14:16:39,735404 my.ipaddress 195.171.192.29 TCP 52402 990 54 52402 → 990 [RST, ACK] Seq=445 Ack=2981 Win=0 Len=0
Client Hello is TLS 1.2
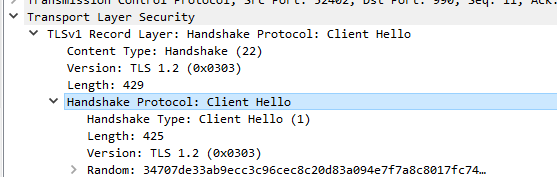
Server Hello is only offering TLS 1.0
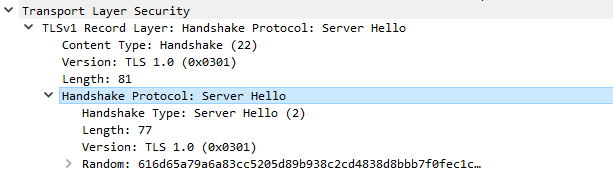
Can you please put this security level up again?
This thread was automatically locked due to age.