Disclaimer: This information is provided as-is for the benefit of the Community. Please contact Sophos Professional Services if you require assistance with your specific environment.
Table of Contents
Overview
With the new SD-WAN introduction, we can prioritize the traffic for applications such as Teams, Zoom,
Google meet. etc. You can follow the KBA - How to Choose the Gateway for A Firewall Rule. Here we’ll learn how to configure an SD-WAN rule for the applications.
SD-WAN Application Object configurations
Step1: Add new Application Object
Go to CONFIGURE > Routing > SD-WAN policy routes > IPv4 SD-WAN policy route > Add
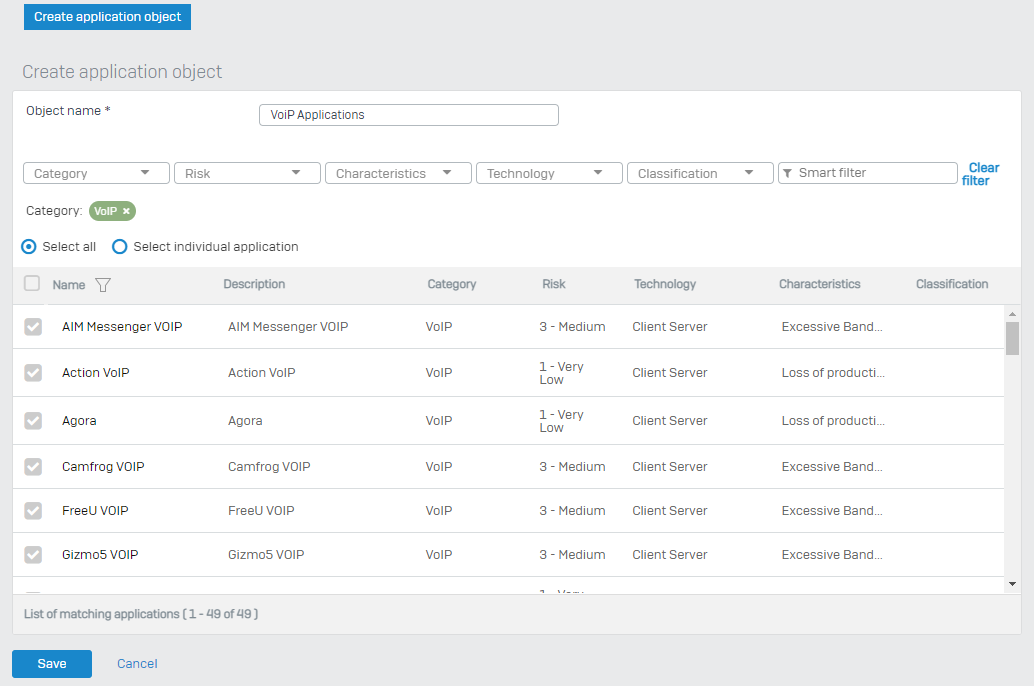
Under PROTECT > Applications>Application Object > Add > Input Object Name
Here, you either filter with the category you want to allow or by selecting specific Application with the help of a smart filter. Kindly refer to the screenshot below:
Category
Smart Filter

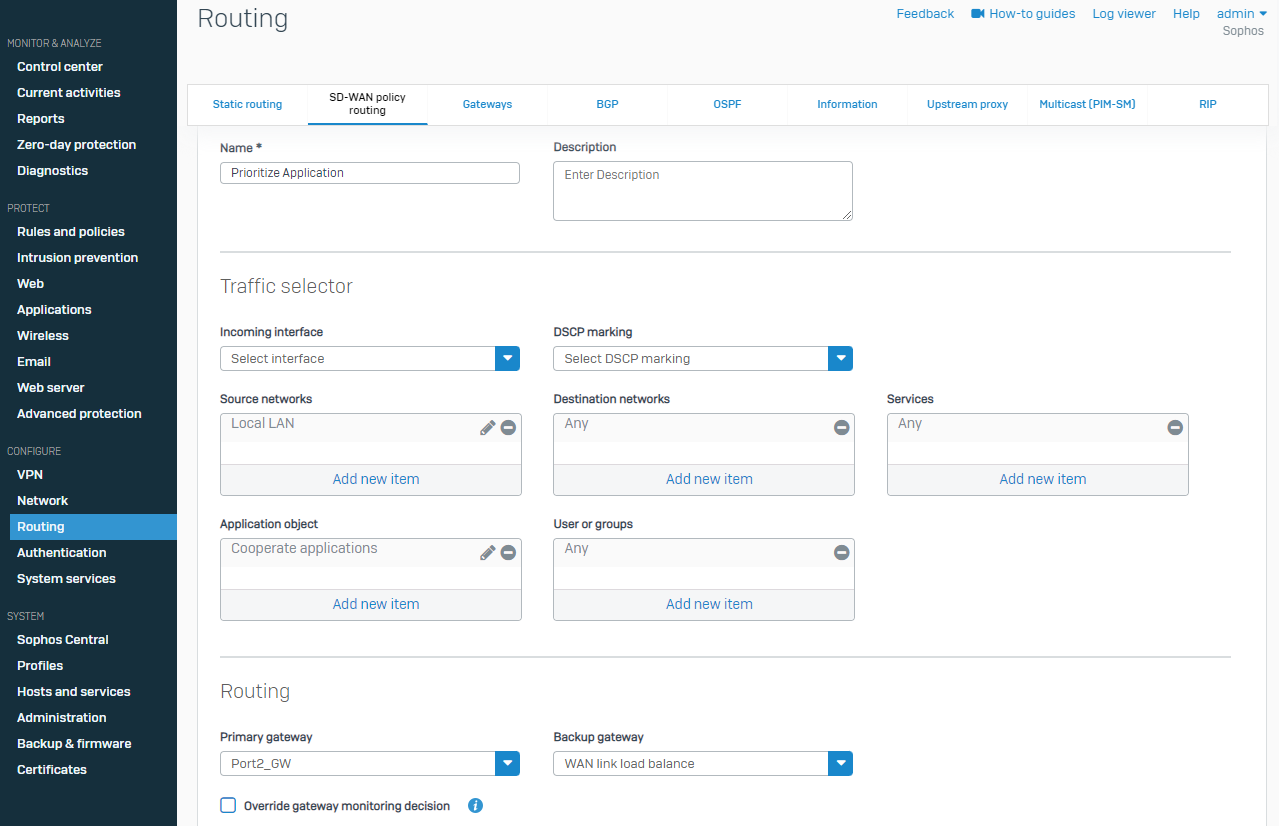
Step2: Choosing a Gateway
You can mention the desired local network under the source network. You can also mention explicit services under the services section. Under the Routing section, you can set the desired gateway from the available WAN links. Kindly see KB on How to Choose Gateway.
Step3: SD-WAN Policy Routing
CONFIGURE > Routing > SD-WAN policy routing; you’ll be able to see the precedence
By default, the precedence is set to - static, SD-WAN, and then VPN routes.
Step4: Show Route Precedence
On the CLI, select option 4. Device Console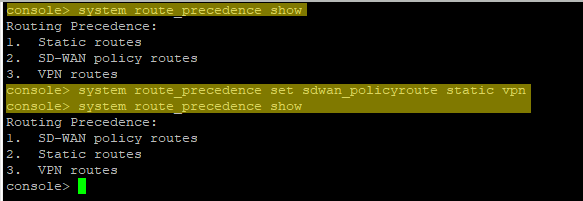
- To check the route precedence
#system route_precedence show - To change the precedence and have sd-wan as first
#system route_precedence set sdwan_policyroute static vpn
How to Choose the Gateway for A Firewall Rule
I hope this article has helped you achieve your requirements!
Edited TAGs
[edited by: Raphael Alganes at 7:49 AM (GMT -7) on 17 Sep 2024]