Disclaimer: This information is provided as-is for the benefit of the Community. Please contact Sophos Professional Services if you require assistance with your specific environment.
Table of Contents
Overview
With the SFOS v19 update, there are some significant changes concerning the configuration of selecting a gateway. These changes are quite different then what we had in previous versions, i.e. SFOS v17 & SFOS v18, which you can refer to here: https://community.sophos.com/sophos-xg-firewall/f/recommended-reads/118888/sophos-xg-firewall-v18-how-to-choose-the-gateway-for-a-firewall-rule
Traditional Settings For Primary and Backup Gateway:
Step 1: For the part mentioned in the screenshot, we will specify the name of the firewall rule and other details regarding rule grouping and Action. Then we specify the Source zones, Source networks, and devices, During the Scheduled time, Destination zones, Destination networks, and Services. Please click the help button if unsure what each option means.
Path: Rules and Policies > Firewall rules > Add firewall rule > New firewall rule: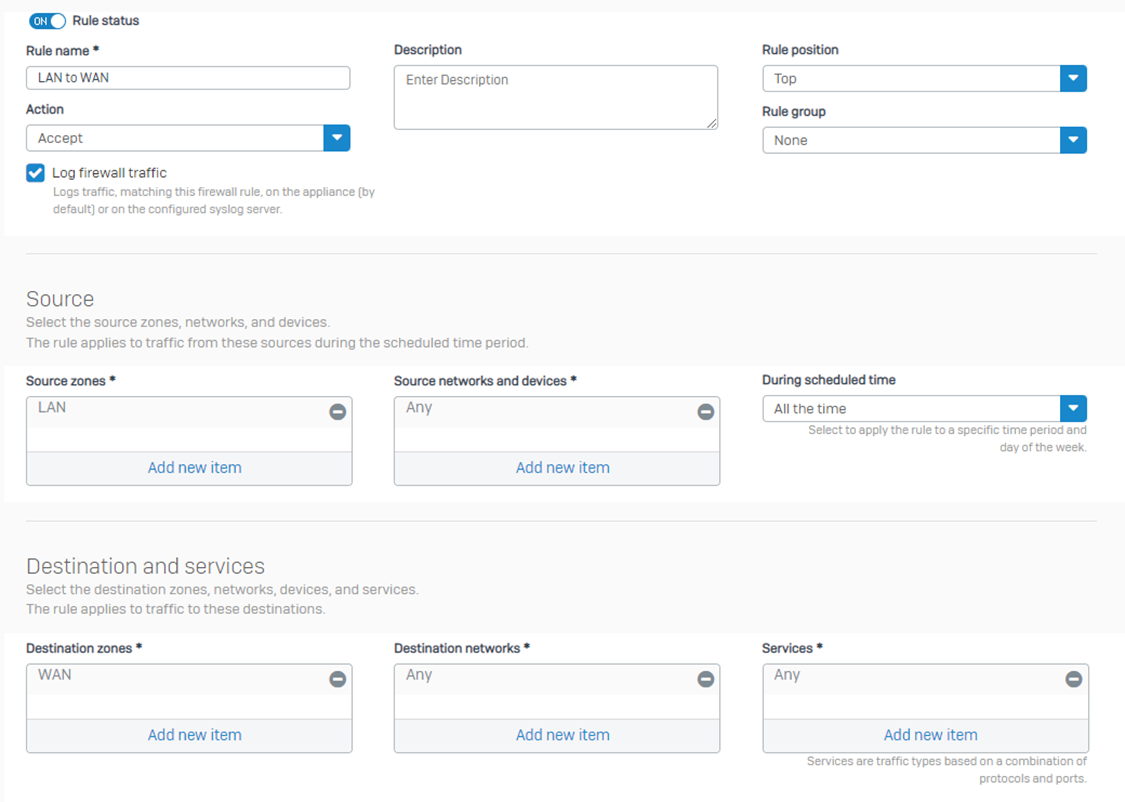
Step 2: Now, the next portion of the configuration is Add exclusion. You can use it to specify the criteria that you don't want to match for this rule. The firewall traverses the rule table further for the excluded criteria.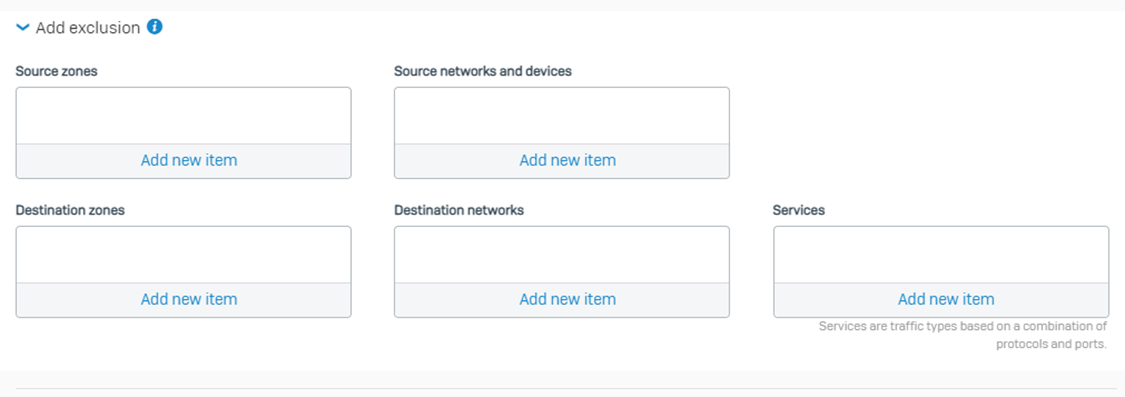
Step 3: Now, Scroll down to the same firewall rule and see the option “Create linked NAT rule.” Click on the option. It isn’t a major significant change if we compare it to v18.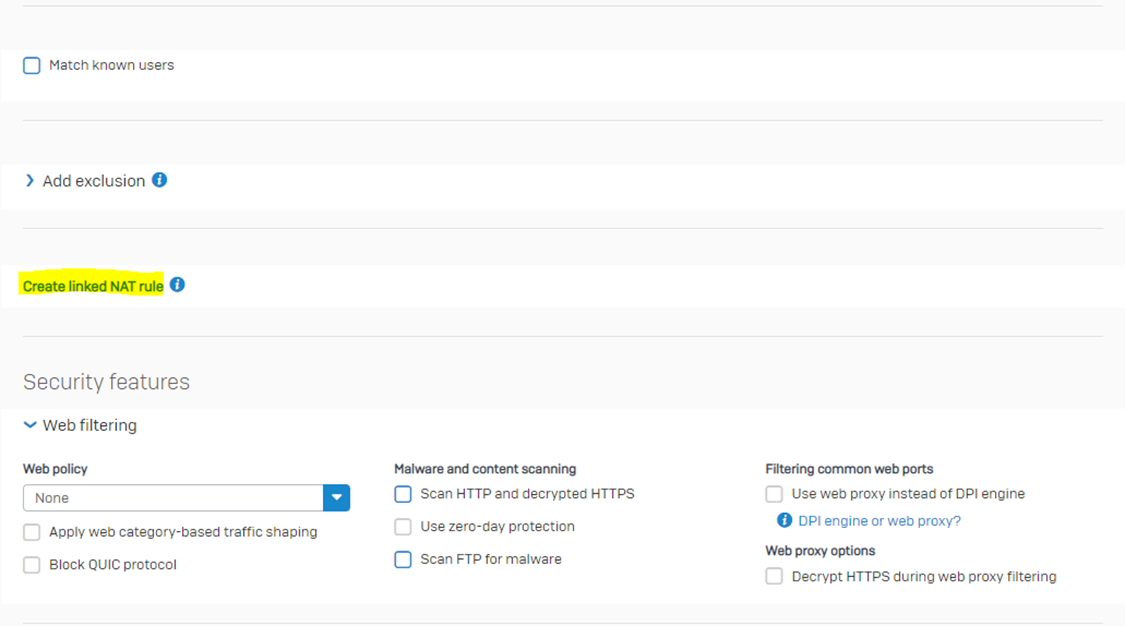
Step 4: If you create a NAT rule from this option, it will only apply to the traffic matching that specific firewall rule, and there will be some options that are greyed out, and you will not be able to change them. You’ll not be able to edit it in the NAT rule table where it is listed along with all Source NAT rules. Further, it’s okay to NOT configure any NAT rule here. The only reason you should configure a NAT rule from here is to link that NAT rule only to this firewall rule.
Please note that Sophos Firewall applies firewall rules before it applies source NAT rules. If a NAT rule meets the matching criteria and is listed in the NAT rule table above the linked NAT rule, Sophos Firewall applies that rule and doesn’t look further for the linked rule. Meaning that regardless of linked or unlinked NAT rules, Sophos Firewall will always follow the top to bottom approach and select the NAT rule just as it does for the Firewall rule for the matching criteria.
Create a firewall rule with a linked NAT rule KBA: https://docs.sophos.com/nsg/sophos-firewall/19.0/Help/en-us/webhelp/onlinehelp/AdministratorHelp/RulesAndPolicies/NATRules/RulesPoliciesCreateFirewalRuleWithLinkedNATRule/index.html
Enable the MASQ option under the NAT rule LAN to WAN > Translated source (SNAT)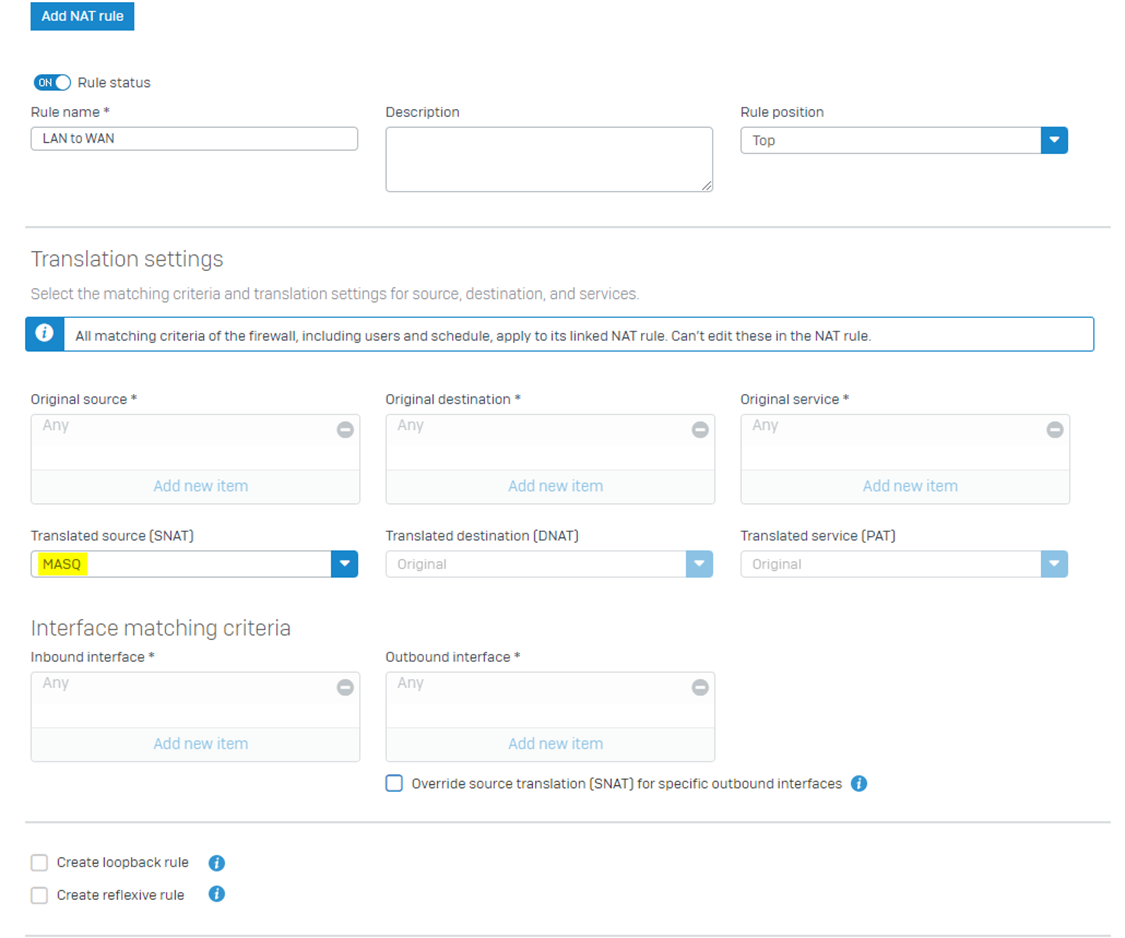
Step 5: The remaining part is as shown in the screenshot below. You should select the options according to your requirements.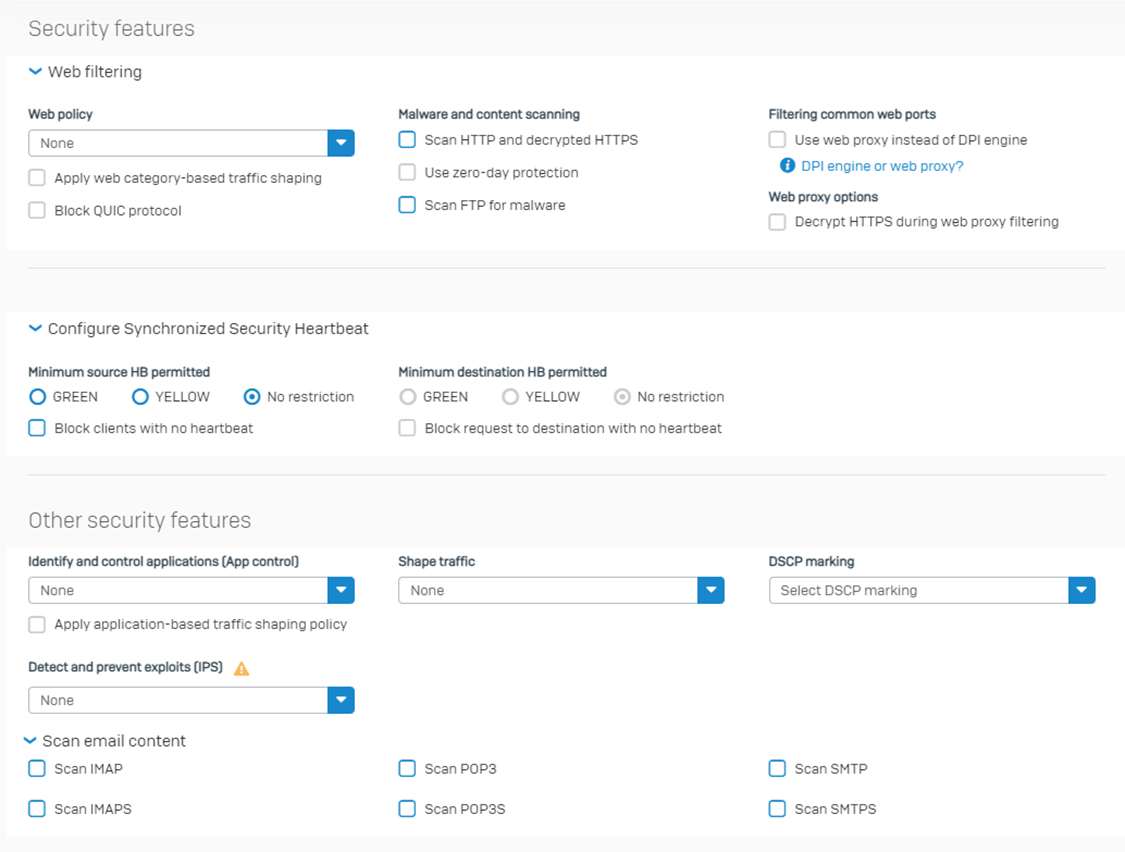
Step 6: Now, we’ll investigate how we will send out the traffic from Sophos Firewall. There are a lot of granular controls available to route traffic out from a specific interface if it matches certain criteria. Here is where the major significant changes are introduced in v19:
Path: Routing > SD-WAN routes > Add:
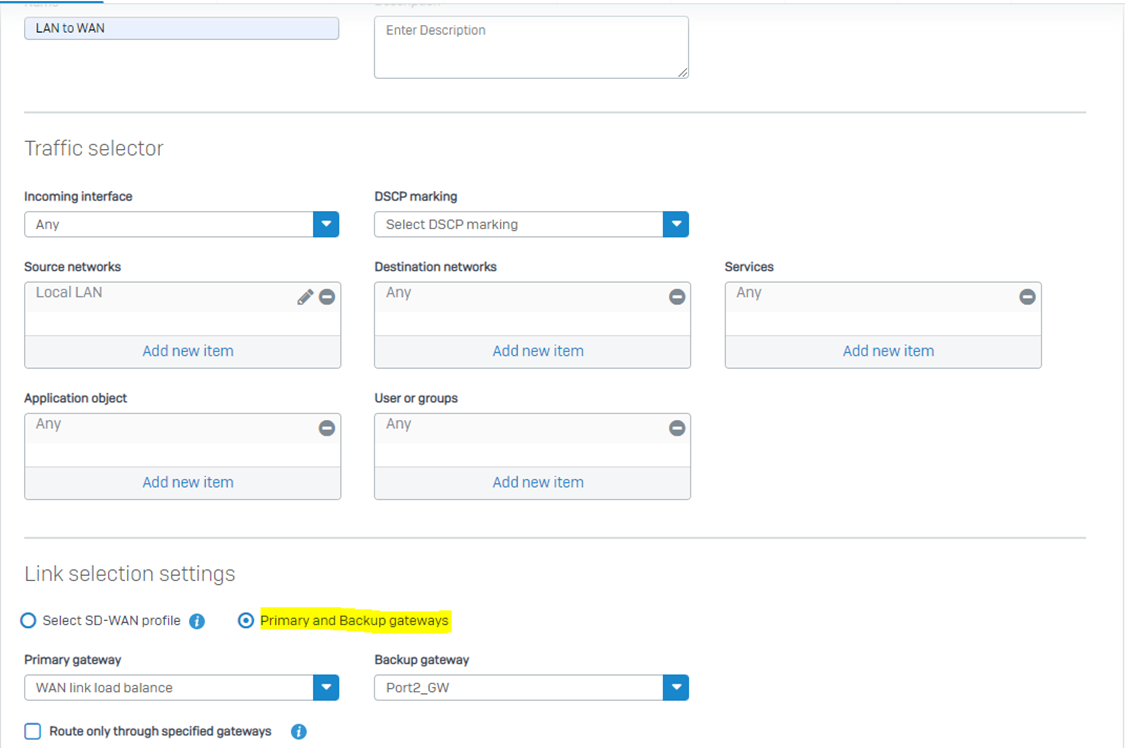
New SD-WAN Profile Settings From v19 Onwards:
Step 1: Now, the next-gen feature introduced is via SD-WAN profile, for which you would require to create a profile under the following path:
Routing > SD-WAN profiles > Add
You select the gateway based on your required precedence of the available gateways:
SD-WAN can support up to 8 gateways.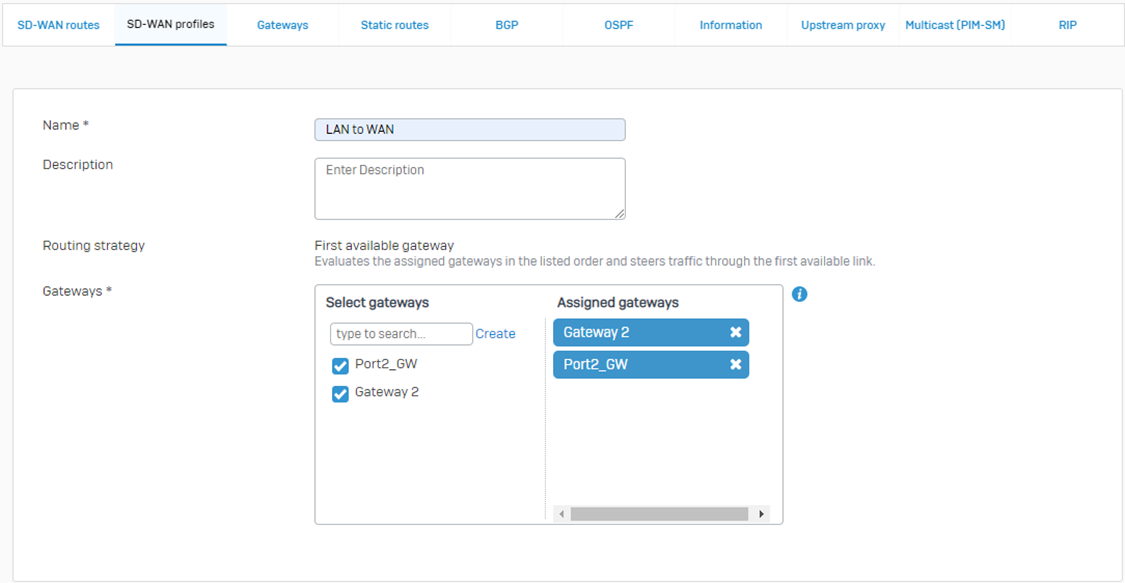
Step 2: Then comes the Service Level Agreement (SLA). For more details, please see: https://doc.sophos.com/nsg/sophos-firewall/19.5/help/en-us/webhelp/onlinehelp/AdministratorHelp/Routing/SDWANRoutes/SDWANProfiles/index.html
Note: Here, the Health check option remains on by default because we have the SLA turned on.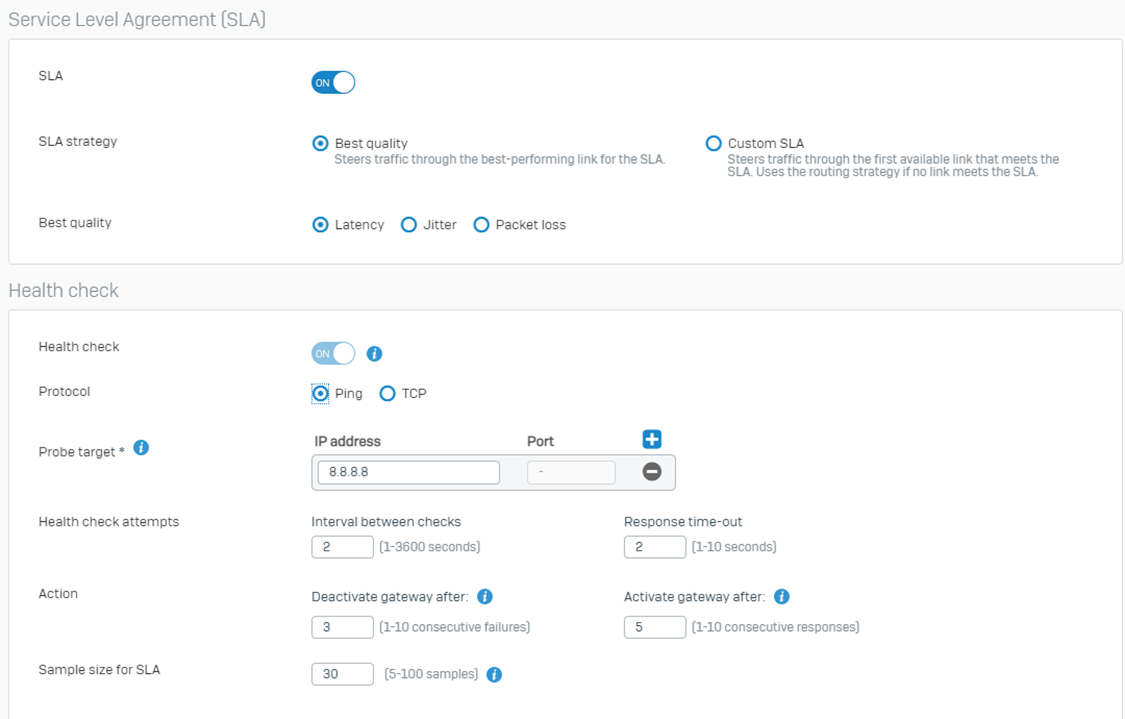
Once you save the SD-WAN profile, it will look similar to the screenshot below: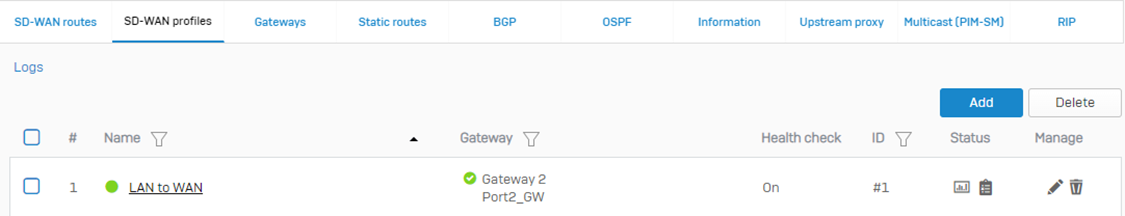
Step 3: Now, let’s apply this profile in our SD-WAN routes instead of using the traditional gateway settings we enabled in step6.
SD-WAN routing behavior: https://doc.sophos.com/nsg/sophos-firewall/19.5/help/en-us/webhelp/onlinehelp/AdministratorHelp/Routing/SDWANRoutes/RoutingSDWANRoutesBehavior/index.html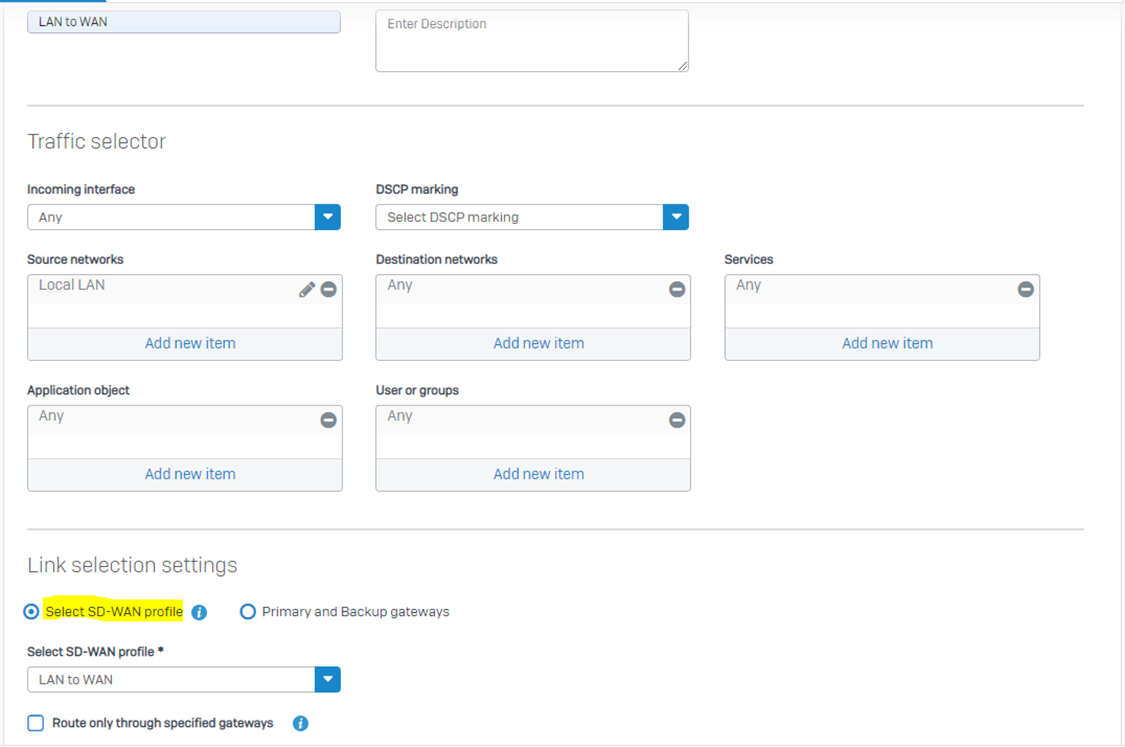
Once you save it looks like the screenshot below: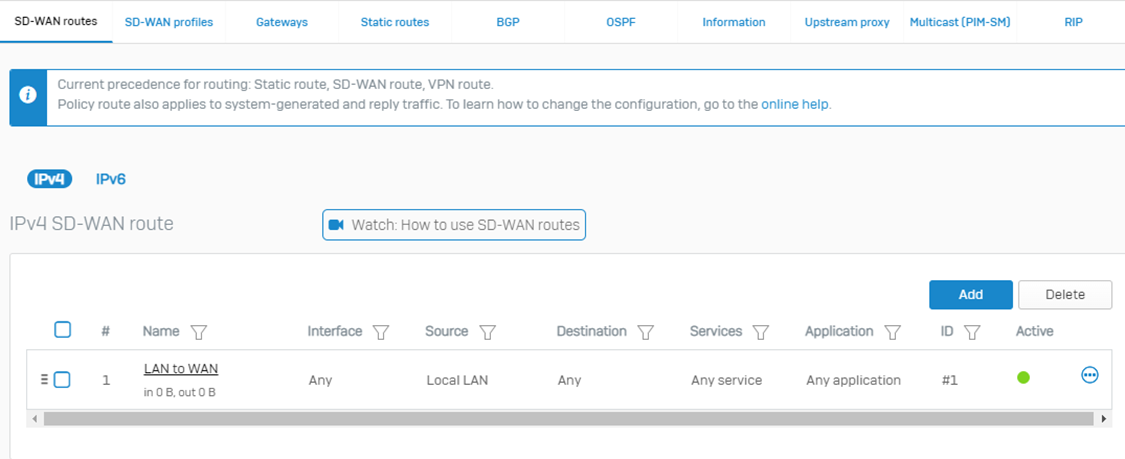
I hope this article helps you understand the difference between previous firmware, i.e., SFOS v17, SFOS v18, and SFOS v19.
Added TAGs
[edited by: Raphael Alganes at 5:49 AM (GMT -7) on 17 Sep 2024]
