Important note about SSL VPN compatibility for 20.0 MR1 with EoL SFOS versions and UTM9 OS. Learn more in the release notes.
Important note about SSL VPN compatibility for 20.0 MR1 with EoL SFOS versions and UTM9 OS. Learn more in the release notes.
Disclaimer: This information is provided as-is for the benefit of the Community. Please contact Sophos Professional Services if you require assistance with your specific environment.
This Recommended read describes a certain user situation and troubleshooting suggestions if the SSL VPN Client download from the User Portal is incorrectly presented as a 0-byte download.
If using the default self-signed certificate resolves the issue, verify the custom CA is properly assembled (proper signing CA, and so on.)
To regenerate an individual user's SSL VPN certificate, you’ll have to go to the Sophos Firewall GUI and delete their user certificate (Certificates > Certificates)
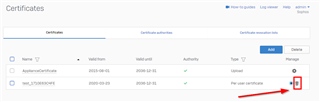
If you’re still experiencing issues, you can regenerate the Default CA by navigating to Certificates > Certificate Authorities.
This will force the regeneration of all SSL VPN user certificates and restart the SSL VPN service.
If these actions are performed, affected users must re-download their SSL VPN installation file to utilize the new certificate.
# cd tmp# cd /content/sslvpn# ls
rw-rr- 1 1000 100 413 Apr 24 2015 client-config-template.ovpnrw-rr- 1 1000 100 111.1K Jun 17 19:35 ssl-vpn-config-installer.exerw-rr- 1 1000 100 1.4M Jun 17 19:35 ssl-vpn-client-installer.exerw-rr- 1 1000 100 72 Jun 17 19:49 U2DVERSIONIf files aren’t present, try to manually update patterns for the SSL VPN Module
df –h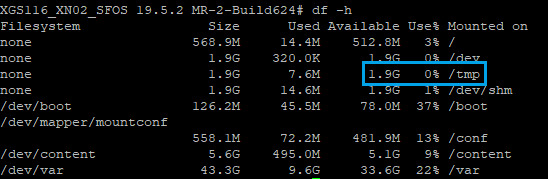
Hello,
the /content/sslvpn is not at /tmp you can find it at / (/content/sslvpn).
On one of our Sophos XG the symlink was pointing to /content/sslvpn_1.01/0 and the directory "0" was not present"
Hello,
Thank you for the guide. It pointed me good direction. In my case, the problem was, that the symbolic link /content/sslvpn was broken. It was pointing to not existing directory /content/sslvpn_1.01/0 and it was supposed to point to /content/sslvpn_1.01/1.0.008/
Commands to check the symbolic link and fix the issue in Advanced shell:
Directories with installed Patterns:
SG310_WP01_SFOS 17.5.14 MR-14-1# ls -ald /content/sslvpn_*/* drwxr-xr-x 2 root 0 1024 Jan 2 2020 /content/sslvpn_1.00/1.0.007 drwxr-xr-x 2 root 0 1024 Nov 26 10:27 /content/sslvpn_1.01/1.0.008
Get where symbolic is pointing if it exists. It should point to one of the directories with installed Patterns, so:
SG310_WP01_SFOS 17.5.14 MR-14-1# ls -altr /content/sslvpn lrwxrwxrwx 1 root 0 29 Nov 26 10:27 /content/sslvpn -> /content/sslvpn_1.01/1.0.008/
In my case, the symbolic link existed, but was not correct:
SG310_WP01_SFOS 17.5.14 MR-14-1# ls -altr /content/sslvpn lrwxrwxrwx 1 root 0 22 Sep 10 20:48 sslvpn -> /content/sslvpn_1.01/0
To fix this situation, I deleted old symbolic link and created new one:
SG310_WP01_SFOS 17.5.14 MR-14-1# cd /content/ SG310_WP01_SFOS 17.5.14 MR-14-1# rm sslvpn SG310_WP01_SFOS 17.5.14 MR-14-1# ln -s /content/sslvpn_1.01/1.0.008/ sslvpn
BTW: The problem with 0Byte SSL VPN File was noticed after switching Cluster from Primary to Auxiliary appliance. The symbolic link was broken just on the appliance that was Auxiliary during Pattern update.
I hope this will help to someone.
Thank you! Almost had Support getting us to regen CA and purge files etc ..
Thank very much, its worked fine for me.
I did have same problem, in upgrade XG 17.5 MR5 to 17.5 MR15.
Regards;
helped me too here. Thank you!
In my case the machine was in an isolated test environment with no internet access and could not download any pattern updates.
By linking the ipsec folder to the correct location after copying the file from an other XG machine, I could help myself.
Doesnt work. We have this error while generating Config:
2021-09-19 15:25:49,927:ERROR:CSC - Exception in getStatusFromResponse() :java.lang.NumberFormatException: For input string: ""java.lang.NumberFormatException: For input string: ""
at java.lang.NumberFormatException.forInputString(NumberFormatException.java:65)
at java.lang.Integer.parseInt(Integer.java:592)
at java.lang.Integer.parseInt(Integer.java:615)
at cyberoam.corporate.csc.client.CSCClient.getStatusFromResponse(CSCClient.java:623)
at cyberoam.corporate.csc.client.CSCClient.sendUDP(CSCClient.java:459)
at cyberoam.corporate.csc.client.CSCClient._send(CSCClient.java:402)
at cyberoam.corporate.csc.client.CSCClient.send(CSCClient.java:147)
at cyberoam.corporate.csc.client.CSCClient.sendWizardEvent(CSCClient.java:1097)
at cyberoam.corporate.csc.client.CSCClient.sendWizardEvent(CSCClient.java:949)
at org.apache.jsp.webpages.sslvpnuserportal.clientdownload_jsp._jspService(clientdownload_jsp.java:301)
at org.apache.jasper.runtime.HttpJspBase.service(HttpJspBase.java:70)
at javax.servlet.http.HttpServlet.service(HttpServlet.java:790)
at org.eclipse.jetty.servlet.ServletHolder.handle(ServletHolder.java:873)
at org.eclipse.jetty.servlet.ServletHandler$CachedChain.doFilter(ServletHandler.java:1623)
at org.eclipse.jetty.websocket.server.WebSocketUpgradeFilter.doFilter(WebSocketUpgradeFilter.java:214)
at org.eclipse.jetty.servlet.ServletHandler$CachedChain.doFilter(ServletHandler.java:1610)
at cyberoam.utilities.csrf.CSRFCheckFilter.doFilter(CSRFCheckFilter.java:171)
at org.eclipse.jetty.servlet.ServletHandler$CachedChain.doFilter(ServletHandler.java:1610)
at cyberoam.sessionmanagement.SessionCheckHelper.filter(SessionCheckHelper.java:109)
at cyberoam.sessionmanagement.SessionCheckFilter.doFilter(SessionCheckFilter.java:64)
at org.eclipse.jetty.servlet.ServletHandler$CachedChain.doFilter(ServletHandler.java:1602)
at org.eclipse.jetty.servlet.ServletHandler.doHandle(ServletHandler.java:540)
at org.eclipse.jetty.server.handler.ScopedHandler.handle(ScopedHandler.java:146)
at org.eclipse.jetty.security.SecurityHandler.handle(SecurityHandler.java:548)
at org.eclipse.jetty.server.handler.HandlerWrapper.handle(HandlerWrapper.java:132)
at org.eclipse.jetty.server.handler.ScopedHandler.nextHandle(ScopedHandler.java:257)
at org.eclipse.jetty.server.session.SessionHandler.doHandle(SessionHandler.java:1701)
at org.eclipse.jetty.server.handler.ScopedHandler.nextHandle(ScopedHandler.java:255)
at org.eclipse.jetty.server.handler.ContextHandler.doHandle(ContextHandler.java:1345)
at org.eclipse.jetty.server.handler.ScopedHandler.nextScope(ScopedHandler.java:203)
at org.eclipse.jetty.servlet.ServletHandler.doScope(ServletHandler.java:480)
at org.eclipse.jetty.server.session.SessionHandler.doScope(SessionHandler.java:1668)
at org.eclipse.jetty.server.handler.ScopedHandler.nextScope(ScopedHandler.java:201)
at org.eclipse.jetty.server.handler.ContextHandler.doScope(ContextHandler.java:1247)
at org.eclipse.jetty.server.handler.ScopedHandler.handle(ScopedHandler.java:144)
at org.eclipse.jetty.server.handler.ContextHandlerCollection.handle(ContextHandlerCollection.java:220)
at org.eclipse.jetty.server.handler.HandlerCollection.handle(HandlerCollection.java:126)
at org.eclipse.jetty.server.handler.HandlerWrapper.handle(HandlerWrapper.java:132)
at org.eclipse.jetty.server.Server.handle(Server.java:502)
at org.eclipse.jetty.server.HttpChannel.handle(HttpChannel.java:370)
at org.eclipse.jetty.server.HttpConnection.onFillable(HttpConnection.java:267)
at org.eclipse.jetty.io.AbstractConnection$ReadCallback.succeeded(AbstractConnection.java:305)
at org.eclipse.jetty.io.FillInterest.fillable(FillInterest.java:103)
at org.eclipse.jetty.io.ChannelEndPoint$2.run(ChannelEndPoint.java:117)
at org.eclipse.jetty.util.thread.strategy.EatWhatYouKill.runTask(EatWhatYouKill.java:333)
at org.eclipse.jetty.util.thread.strategy.EatWhatYouKill.doProduce(EatWhatYouKill.java:310)
at org.eclipse.jetty.util.thread.strategy.EatWhatYouKill.tryProduce(EatWhatYouKill.java:168)
at org.eclipse.jetty.util.thread.strategy.EatWhatYouKill.run(EatWhatYouKill.java:126)
at org.eclipse.jetty.util.thread.ReservedThreadExecutor$ReservedThread.run(ReservedThreadExecutor.java:366)
at org.eclipse.jetty.util.thread.QueuedThreadPool.runJob(QueuedThreadPool.java:765)
at org.eclipse.jetty.util.thread.QueuedThreadPool$2.run(QueuedThreadPool.java:683)
at java.lang.Thread.run(Thread.java:748)
2021-09-19 15:25:49,928:ERROR:SSL VPN - Exception while preparing download of SSLVPN/auth clients: java.lang.StringIndexOutOfBoundsException: String index out of range: -1
at java.lang.String.substring(String.java:1960)
at org.apache.jsp.webpages.sslvpnuserportal.clientdownload_jsp._jspService(clientdownload_jsp.java:307)
at org.apache.jasper.runtime.HttpJspBase.service(HttpJspBase.java:70)
at javax.servlet.http.HttpServlet.service(HttpServlet.java:790)
at org.eclipse.jetty.servlet.ServletHolder.handle(ServletHolder.java:873)
at org.eclipse.jetty.servlet.ServletHandler$CachedChain.doFilter(ServletHandler.java:1623)
at org.eclipse.jetty.websocket.server.WebSocketUpgradeFilter.doFilter(WebSocketUpgradeFilter.java:214)
at org.eclipse.jetty.servlet.ServletHandler$CachedChain.doFilter(ServletHandler.java:1610)
at cyberoam.utilities.csrf.CSRFCheckFilter.doFilter(CSRFCheckFilter.java:171)
at org.eclipse.jetty.servlet.ServletHandler$CachedChain.doFilter(ServletHandler.java:1610)
at cyberoam.sessionmanagement.SessionCheckHelper.filter(SessionCheckHelper.java:109)
at cyberoam.sessionmanagement.SessionCheckFilter.doFilter(SessionCheckFilter.java:64)
at org.eclipse.jetty.servlet.ServletHandler$CachedChain.doFilter(ServletHandler.java:1602)
at org.eclipse.jetty.servlet.ServletHandler.doHandle(ServletHandler.java:540)
at org.eclipse.jetty.server.handler.ScopedHandler.handle(ScopedHandler.java:146)
at org.eclipse.jetty.security.SecurityHandler.handle(SecurityHandler.java:548)
at org.eclipse.jetty.server.handler.HandlerWrapper.handle(HandlerWrapper.java:132)
at org.eclipse.jetty.server.handler.ScopedHandler.nextHandle(ScopedHandler.java:257)
at org.eclipse.jetty.server.session.SessionHandler.doHandle(SessionHandler.java:1701)
at org.eclipse.jetty.server.handler.ScopedHandler.nextHandle(ScopedHandler.java:255)
at org.eclipse.jetty.server.handler.ContextHandler.doHandle(ContextHandler.java:1345)
at org.eclipse.jetty.server.handler.ScopedHandler.nextScope(ScopedHandler.java:203)
at org.eclipse.jetty.servlet.ServletHandler.doScope(ServletHandler.java:480)
at org.eclipse.jetty.server.session.SessionHandler.doScope(SessionHandler.java:1668)
at org.eclipse.jetty.server.handler.ScopedHandler.nextScope(ScopedHandler.java:201)
at org.eclipse.jetty.server.handler.ContextHandler.doScope(ContextHandler.java:1247)
at org.eclipse.jetty.server.handler.ScopedHandler.handle(ScopedHandler.java:144)
at org.eclipse.jetty.server.handler.ContextHandlerCollection.handle(ContextHandlerCollection.java:220)
at org.eclipse.jetty.server.handler.HandlerCollection.handle(HandlerCollection.java:126)
at org.eclipse.jetty.server.handler.HandlerWrapper.handle(HandlerWrapper.java:132)
at org.eclipse.jetty.server.Server.handle(Server.java:502)
at org.eclipse.jetty.server.HttpChannel.handle(HttpChannel.java:370)
at org.eclipse.jetty.server.HttpConnection.onFillable(HttpConnection.java:267)
at org.eclipse.jetty.io.AbstractConnection$ReadCallback.succeeded(AbstractConnection.java:305)
at org.eclipse.jetty.io.FillInterest.fillable(FillInterest.java:103)
at org.eclipse.jetty.io.ChannelEndPoint$2.run(ChannelEndPoint.java:117)
at org.eclipse.jetty.util.thread.strategy.EatWhatYouKill.runTask(EatWhatYouKill.java:333)
at org.eclipse.jetty.util.thread.strategy.EatWhatYouKill.doProduce(EatWhatYouKill.java:310)
at org.eclipse.jetty.util.thread.strategy.EatWhatYouKill.tryProduce(EatWhatYouKill.java:168)
at org.eclipse.jetty.util.thread.strategy.EatWhatYouKill.run(EatWhatYouKill.java:126)
at org.eclipse.jetty.util.thread.ReservedThreadExecutor$ReservedThread.run(ReservedThreadExecutor.java:366)
at org.eclipse.jetty.util.thread.QueuedThreadPool.runJob(QueuedThreadPool.java:765)
at org.eclipse.jetty.util.thread.QueuedThreadPool$2.run(QueuedThreadPool.java:683)
at java.lang.Thread.run(Thread.java:748)
Hello Yunus Tuncer,
Thank you for reaching out to the Sophos Community.
Is it possible for you to confirm which version of XG device you are using, as well as the firmware?
Thank you,
Kushal Lakhan
Global Community Support Engineer | Global Community Team
Sophos Support Videos | Product Documentation | @SophosSupport | Sign up for SMS Alerts
If a post solves your question use the 'Verify Answer' link.

Another more common fix for this issue is found here https://community.sophos.com/sophos-xg-firewall/f/discussions/119343/ssl-vpn-client-downloads-are-not-being-generated check out Paul Warriner's post. We have had to apply this now at multiple sites to get it to download the missing files. Note that it will symlink initially to /content/sslvpn_1.0.x/0 then once the pattern finishes downloading it corrects to the appropriate subfolder. This also avoids messing with any of the SSL certificates which in our cases were not the issue, as they were generating the user certs without any problems.