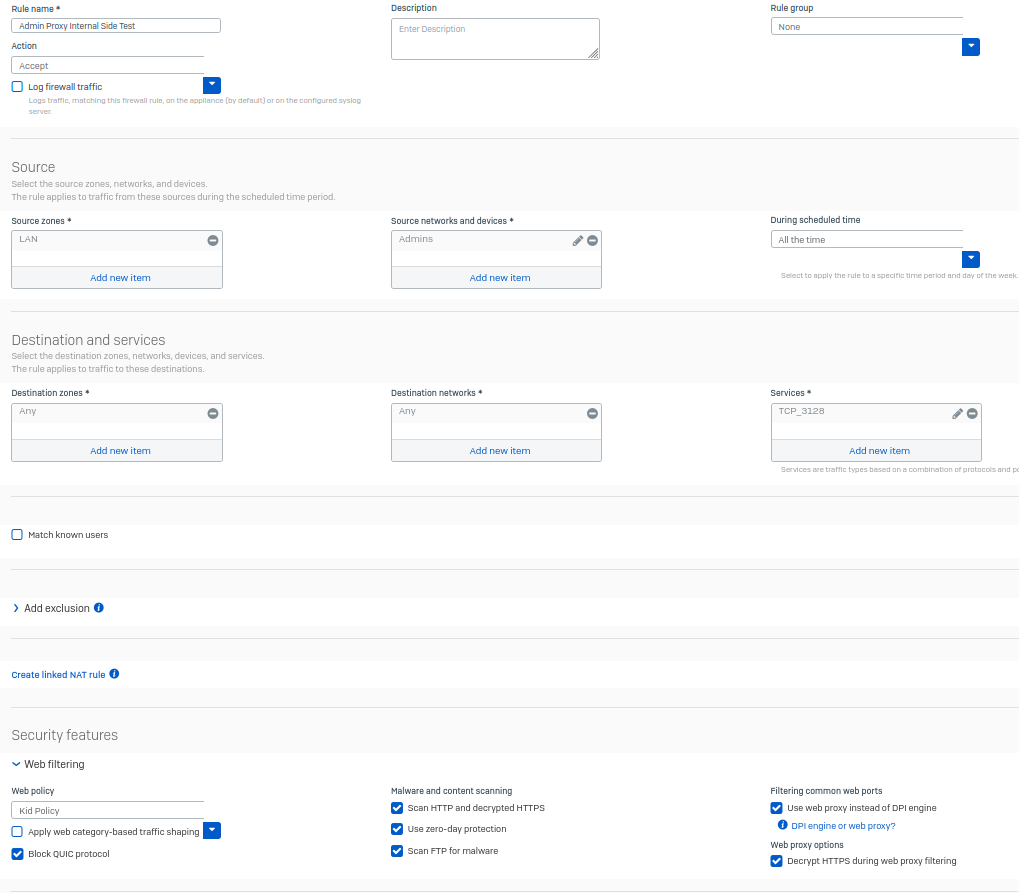
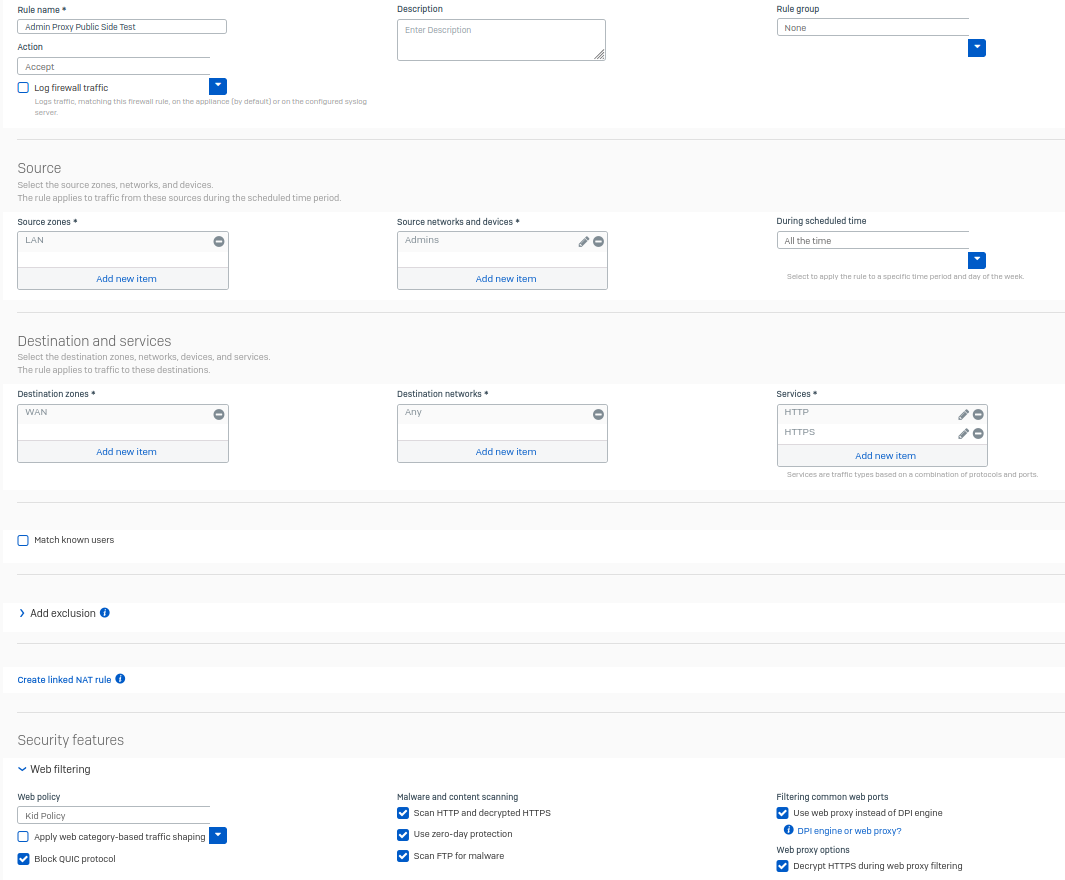
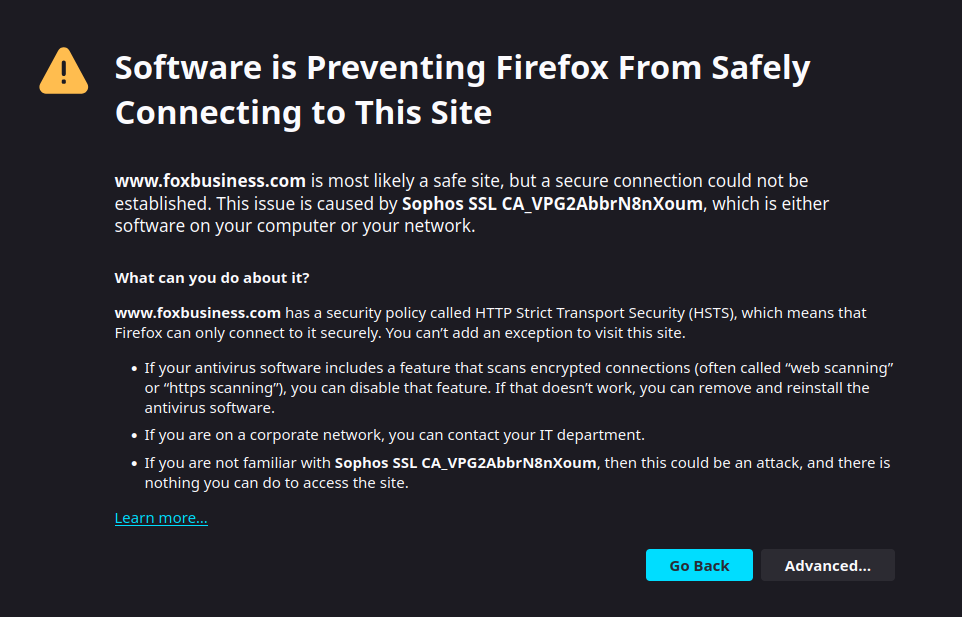
I want to configure my Sophos Firewall so that only Firefox can access the internet from a PC, and all traffic must go through the Sophos explicit web proxy (configured on port 3128). Direct HTTP/HTTPS traffic from the PC should be blocked entirely.
When I configure Firefox to use the proxy, web pages are blocked unless direct HTTP/HTTPS traffic (ports 80/443) from the PC to the WAN is allowed. This defeats the purpose of forcing traffic through the proxy. If I block ports 80 and 443, the proxy stops working even though traffic to port 3128 is explicitly allowed.
What am i missing?
Thanks
Added TAGs
[edited by: Erick Jan at 3:15 AM (GMT -8) on 25 Nov 2024]