I want to configure my Sophos Firewall so that only Firefox can access the internet from a PC, and all traffic must go through the Sophos explicit web proxy (configured on port 3128). Direct HTTP/HTTPS traffic from the PC should be blocked entirely.
When I configure Firefox to use the proxy, web pages are blocked unless direct HTTP/HTTPS traffic (ports 80/443) from the PC to the WAN is allowed. This defeats the purpose of forcing traffic through the proxy. If I block ports 80 and 443, the proxy stops working even though traffic to port 3128 is explicitly allowed.
What am i missing?
Thanks
Hi Jason,
Thank you for reaching out to Sophos Community.
Kindly try to create a firewall rule to only allow traffic via 3128, then make another firewall rule to block all (https/http) incoming traffic via port 80/443.
Upon applying to Firefox. Kindly check the logs viewer/monitor traffic via packet capture.
Erick Jan
Global Community Engineer, Support & Services
Are you a Sophos Partner? | Product Documentation | @SophosSupport | Sign up for SMS Alerts
If a post solves your question, please use the 'Verify Answer' button.
The award-winning home for Sophos Support videos! - Visit Sophos Techvids
It is actually slightly more complicated. There still needs to be a rule for HTTP/HTTPS for the proxy to talk externally - otherwise you will get the page attempting to load and then timeout with a sophos generated error page.
In effect you have two connections
PC <--> SFOS <--> website
The PC to SFOS is 3128 and needs a firewall rule.
The SFOS to website is 80/443 and needs a firewall rule. Web policy is not applied to traffic generated from the web proxy.
The firewall rules are re-evaluated on the external connection. Otherwise web proxy can be used to bypass some firewall rules (such as GeoIP counry blocks).
Recommendation is
Rule 1 - Service 3128. Web policy what you want.
Rule 2 - Service HTTP/HTTPS. Web policy Block All.
Note: Transparent mode traffic will hit the Block All policy, so they get a block page. However exceptions are still applied, therefore they will still be able to do things like get to microsoft.com (for windows updates). You can watch the Web Filter log for connections that are using that firewall rule and determine if you want to allow/block them via exception.
If I recall there are some other possible setups that block transparent HTTP/HTTPS more completely but are more complex. And that customers found that some updaters and things just do not support direct mode so they found that supporting a little bit of transparent mode was nice to have.
It is suggested that if you are doing this you may want to use WPAD/PAC to deploy the proxy settings. That way any browser configured for proxy "automatically detect settings" picks it up. That will also catch a few non browsers as well.
I'm not the OP, but I'm also unable to get this working.
I created what I think is your "Rule 1" here:
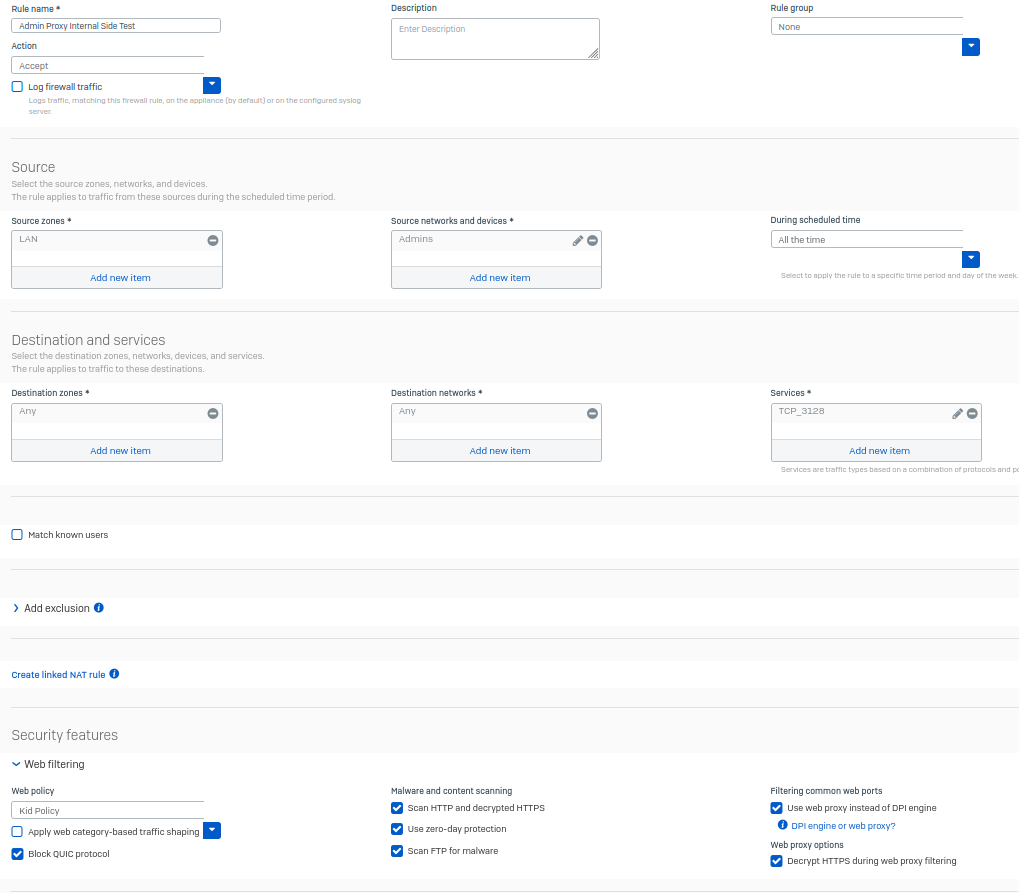
I created what I think is your "Rule 2" here, place beneath "Rule 1":
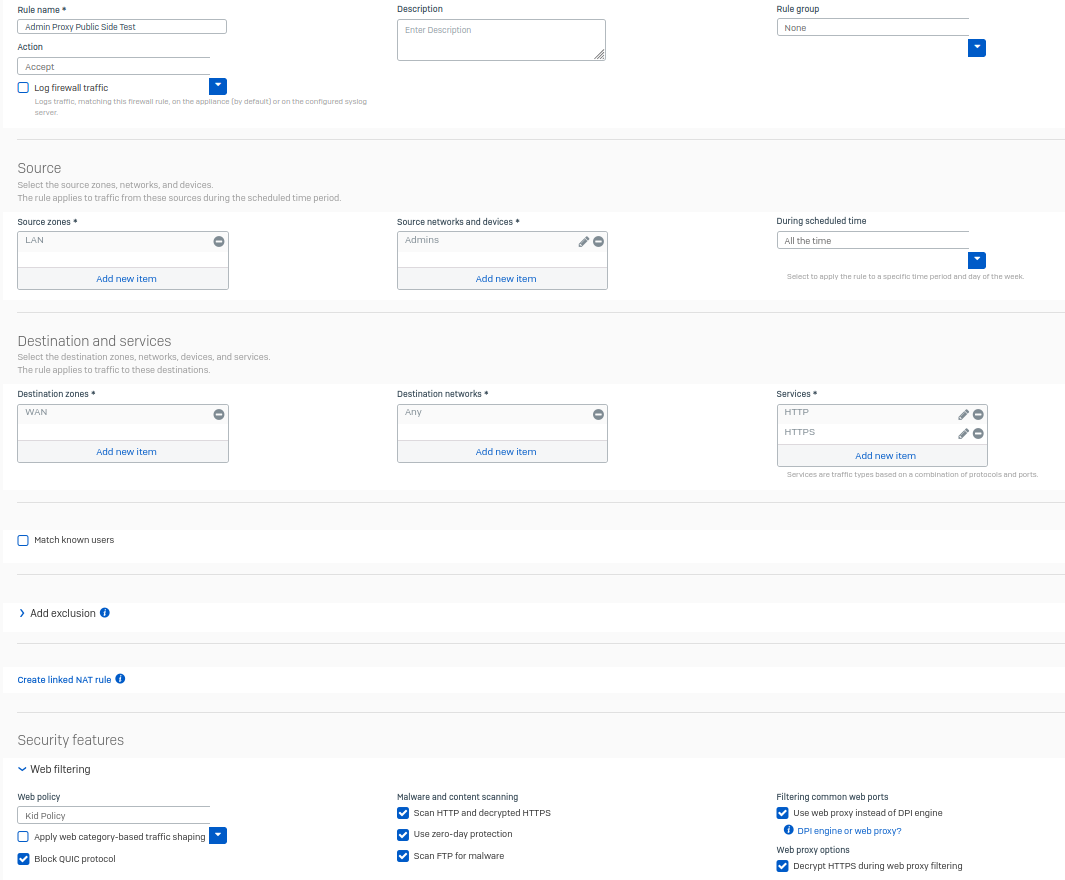
Then I updated Firefox to use the proxy at 10.10.80.41 (internal SOPHOS IP), with a port of 3128... and the only websites I can see are SOPHOS's. Everything else gives me:
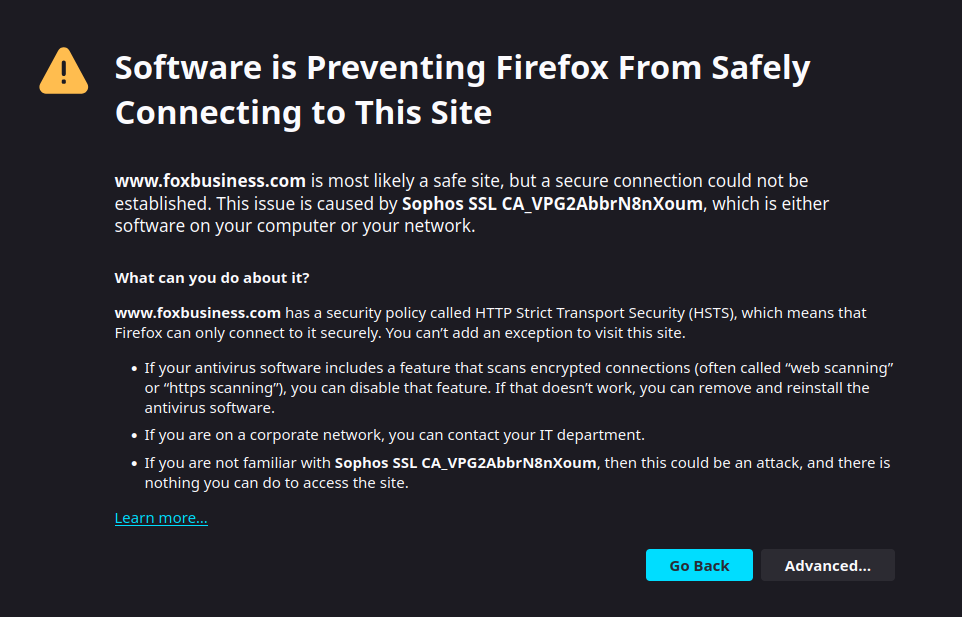
Ultimately I'm trying to configure SOPHOS as a legacy Web Proxy so that I can enforce SafeSearch/Google/YouTube restrictions, which as I understand it require this proxy configuration.
Did you push the Certificate from SFOS to the clients?
Ultimately, you will have to enroll the certs, otherwise we cannot intercept this.
__________________________________________________________________________________________________________________
Because you are doing HTTPS decryption you need to have the sophos CA installed.
Because this changes the way websites are signed (such as foxbusiness), websites that are configured with HSTS will complain. The website told the browser "Dont ever let the certificate change".
Take a look at the FAQ.
Sophos Firewall: HTTPS Decrypt and Scan FAQ
Offhand I do not know how to clear HSTS for the entire browser, I presume sales/support knows. Google results tend to focus on how to clear for single websites.
Thanks all. Ultimately I don't think I really care about decrypting HTTPS... perhaps I confused matters with that screenshot. I'm simply trying to enforce SafeSearch/Google/Yahoo restrictions using the built-in options. In my current transparent proxy mode, those options won't work --> "This option can be enforced by the web proxy only.". I seem to be overlooking something when trying to configure this.
If you wish to safe search etc, you will to install the CA otherwise you can't decode the https connections.
Ian
XGS118 - v21.5.0
XG115 converted to software licence v21.5.0
If a post solves your question please use the 'Verify Answer' button.
Sorry Ian that is wrong.
Sophos Firewall can enforce safesearch restrictions on bing. youtube, and google without HTTPS decryption, using a cname.
Yahoo requires HTTPS. Image filters require HTTPS.
support.google.com/.../186669
Yeah, I've read about this a few times in my searches... maybe that's the route to go, even though I wanted to apply this for some but not all users. Thank you for your time!