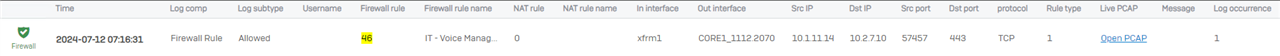
We have currently have two locations, each with a XG330 v19.5.4 MR4 and an EPL fiber connection between them that has a S2S IPSec tunnel setup and a static route on both ends pointing to the other. Each FW is setup with the local DC for user authentication (same domain). Currently there are several FW rules we would like to switch to being user-based vs device-based (FQDN) or network-based (IP/NETWORK) as we rollout "hotdesk" setups (whoever can login wherever they want to sit that day). From what I am seeing both locations are working as anticipated/desired with local traffic/users (they all show up with a client type of Heartbeat as they are all setup with Sophos Endpoint Protection). Our issue is coming when we have a user at location A that is trying to access a resource at location B. The user authentication is not passed through so the FW rules at location B block the access. The same is for users at location B wanting to access resources at location A. I'm pretty sure there is a proper way to address this, but I am not entirely sure which solution to pursue. Any advise or guidance would be greatly appreciated.
Thank you,
James
This thread was automatically locked due to age.