I have set up a SSL VPN connection in SOHPOS Firewall v20 Build 222.
I can access local services and machines no problems there, but I cant get internet access.
When I ping external sources no packages comes through, however domain names are resolved:
ping www.kde.org: PING tyran.kde.org (85.10.198.55) 56(84) bytes of data. ^C --- tyran.kde.org ping statistics --- 42 packets transmitted, 0 received, 100% packet loss, time 41959ms
This is my settings:
The SSL VPN Global settings
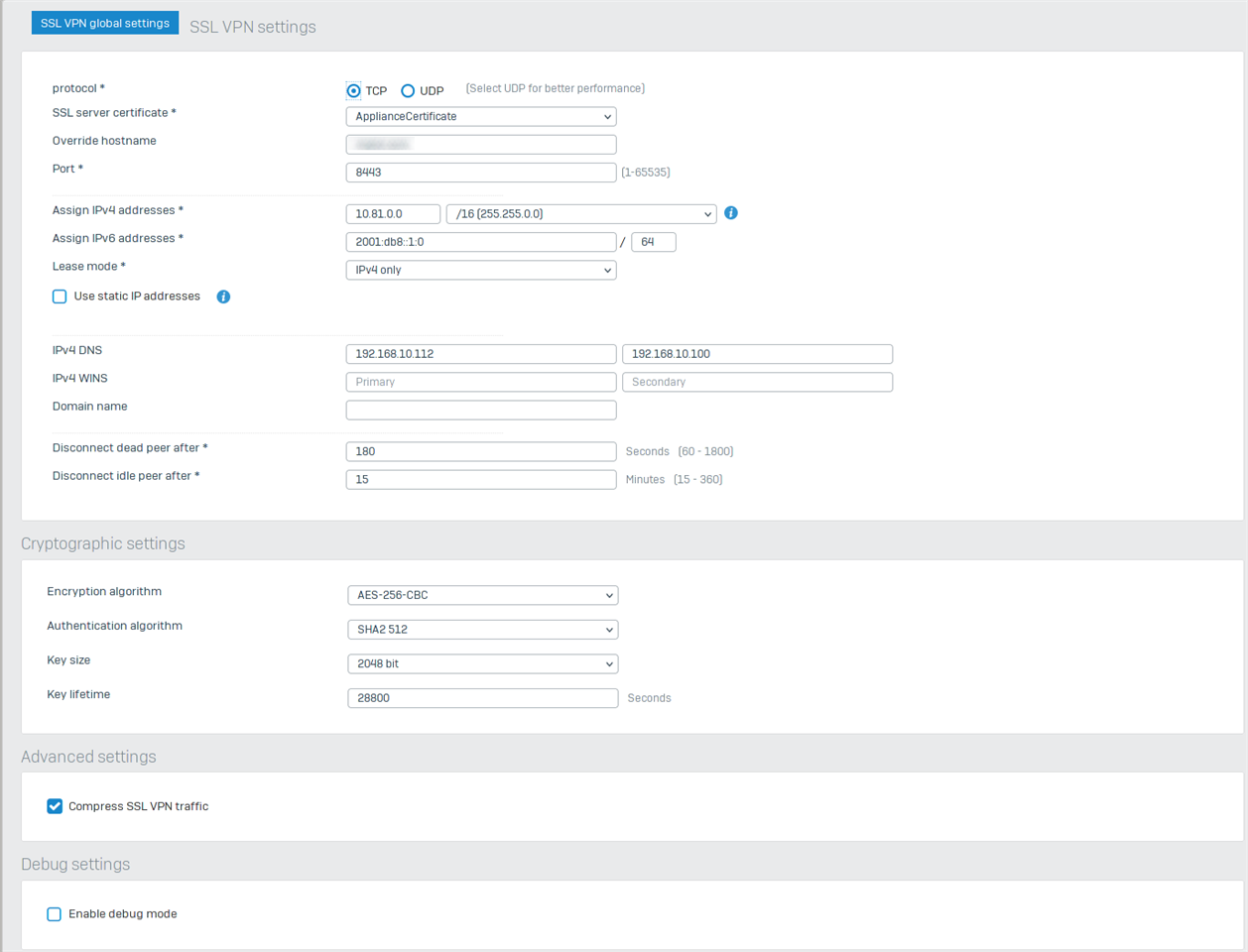
Mostly kept as is but added Override hostname (Same as DDNS) witch resolves to my IP
The IPv4 DNS Servers are both in my network one of them is the DNS on the Firewall
My user login settings:
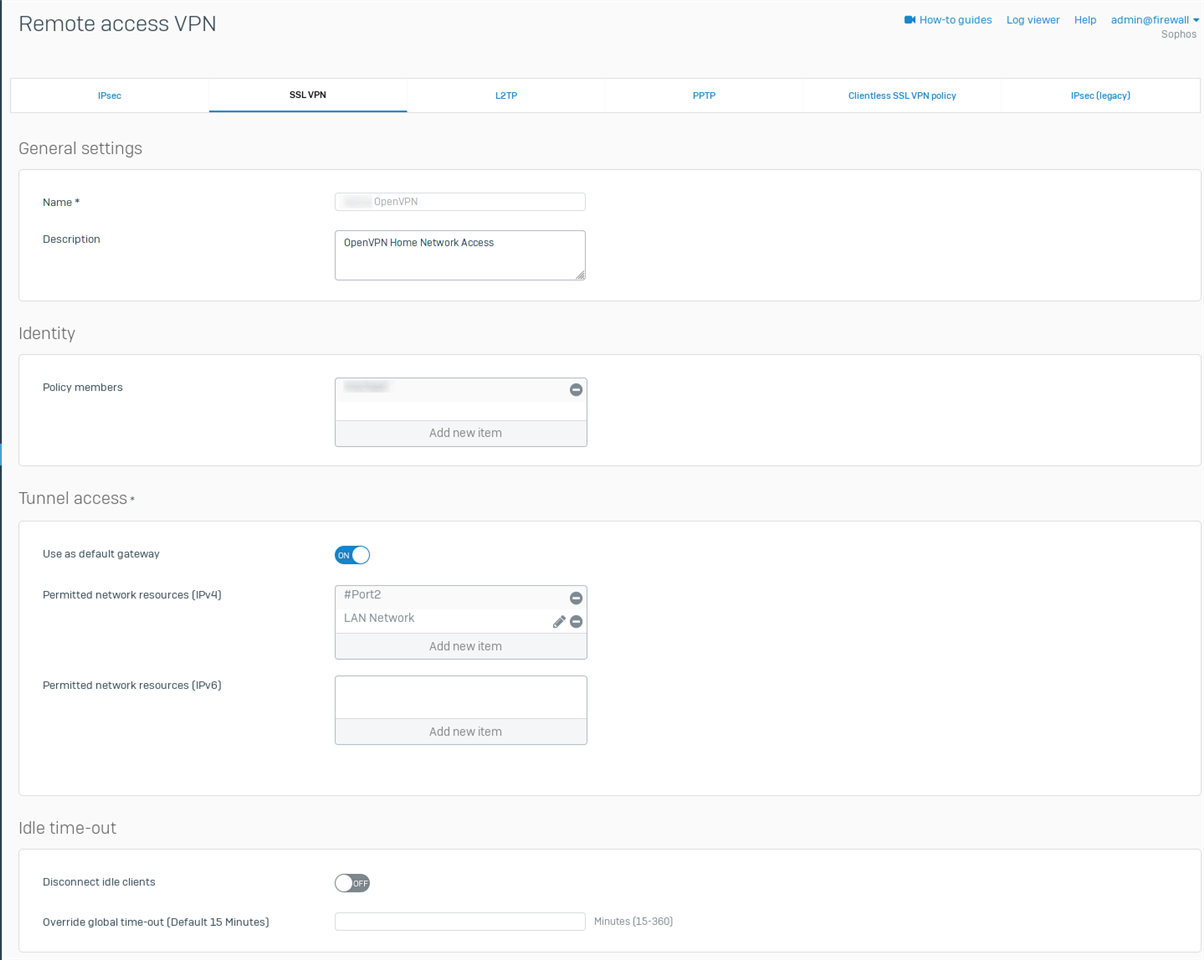
Using tunnel as default gateway on or off makes no difference.
The LAN Network contains local ip range 192.168.10.0/24
I tried adding #Port2 just to have tried every possibilities I could think off. It is now removed since it had no effect.
Automatic generated Firewall rule:
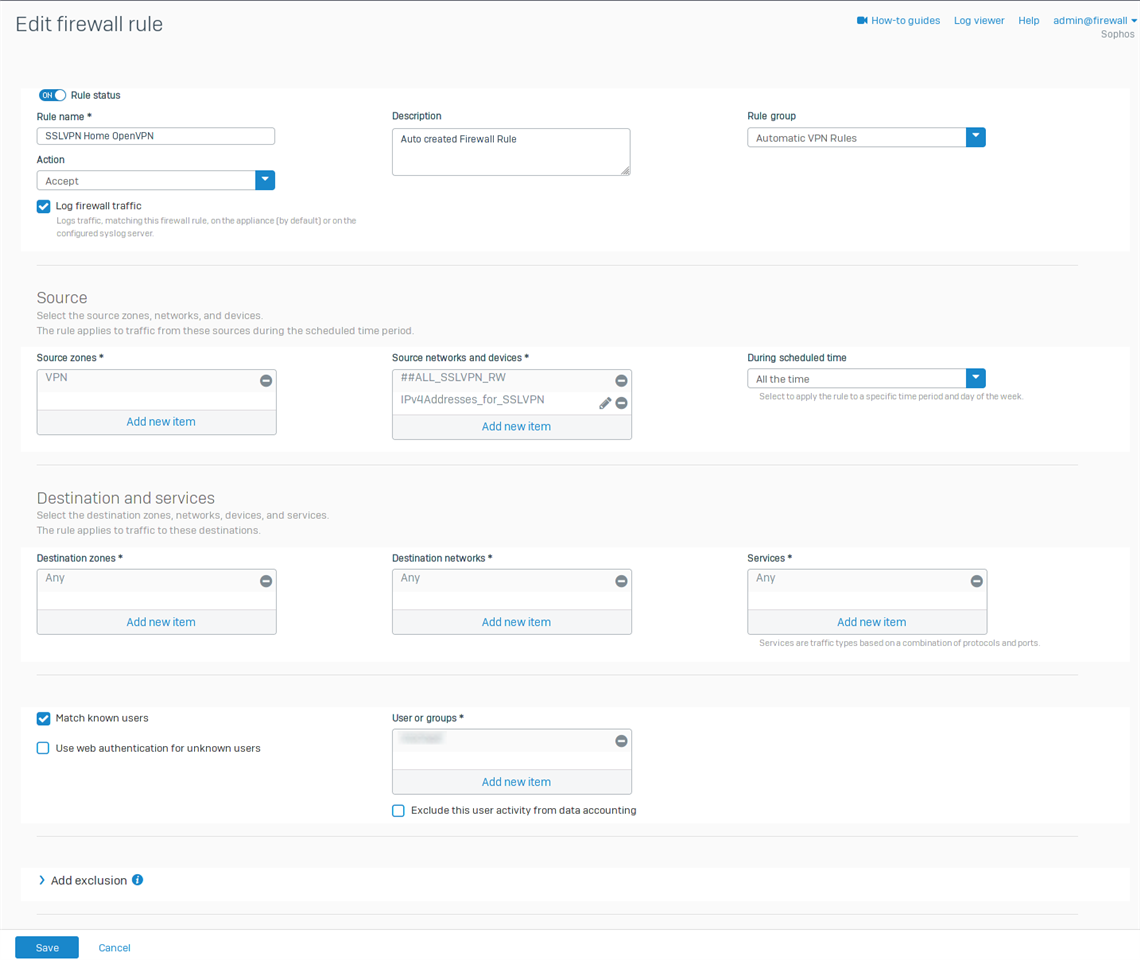
Only change her is I tried adding ##ALL_SSLVPN_RW to source network.
No VPN firewall Security features is enabled.
SSL VPN Authentication method:
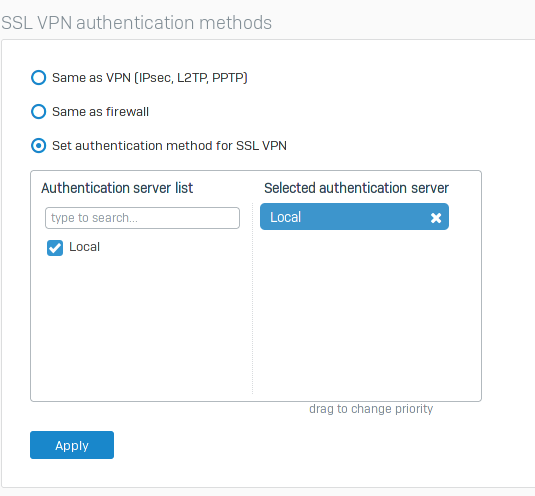
Default kept here.
Clients:
I’m using OpenVPN Client 3.4.2 on my mobile devices and NetworkManager (KDE5) on my Laptop
Some changes had to be maid to the .ovpn file downloaded to get it to import in NetworkManager
The following line needed to be commented out:
route remote_host 255.255.255.255 net_gateway
The default LAN to WAN Firewall rule is left at default except
Block QUIC protocol ha been activated and all Malware and Conetnt scanning is activated.
So Source, Destination and Services is set to Any
I have tried different setting all over without any changes. I’m out of ideas on how to get this to work.
The traffic has to be blocked somewhere, I just cant see what.
This thread was automatically locked due to age.


