I am completely stumped by this. I am sure its something obvious that I am overlooking.
Lan Port 1 - 192.168.1.254/24
MGMT port 5 - 172.16.0.254/24
I already had a rule saying mgmt subnet source 172.16.0.0 could access lan subnet destination 192.168.1.0. That worked fine, the mgmt server (172.16.0.1) can RDP etc to the LAN server (192.168.1.250).
but then the server engineer said could I allow access from mgmt server to the LAN server ilo (192.168.1.251). First off I couldnt work out why this wasnt just working with the above rule.
So set up a separate rule above the other one just for mgmt server to lan server ilo but when I ping or try access it it doesnt work. I can see the out counter slightly increasing on the rule.
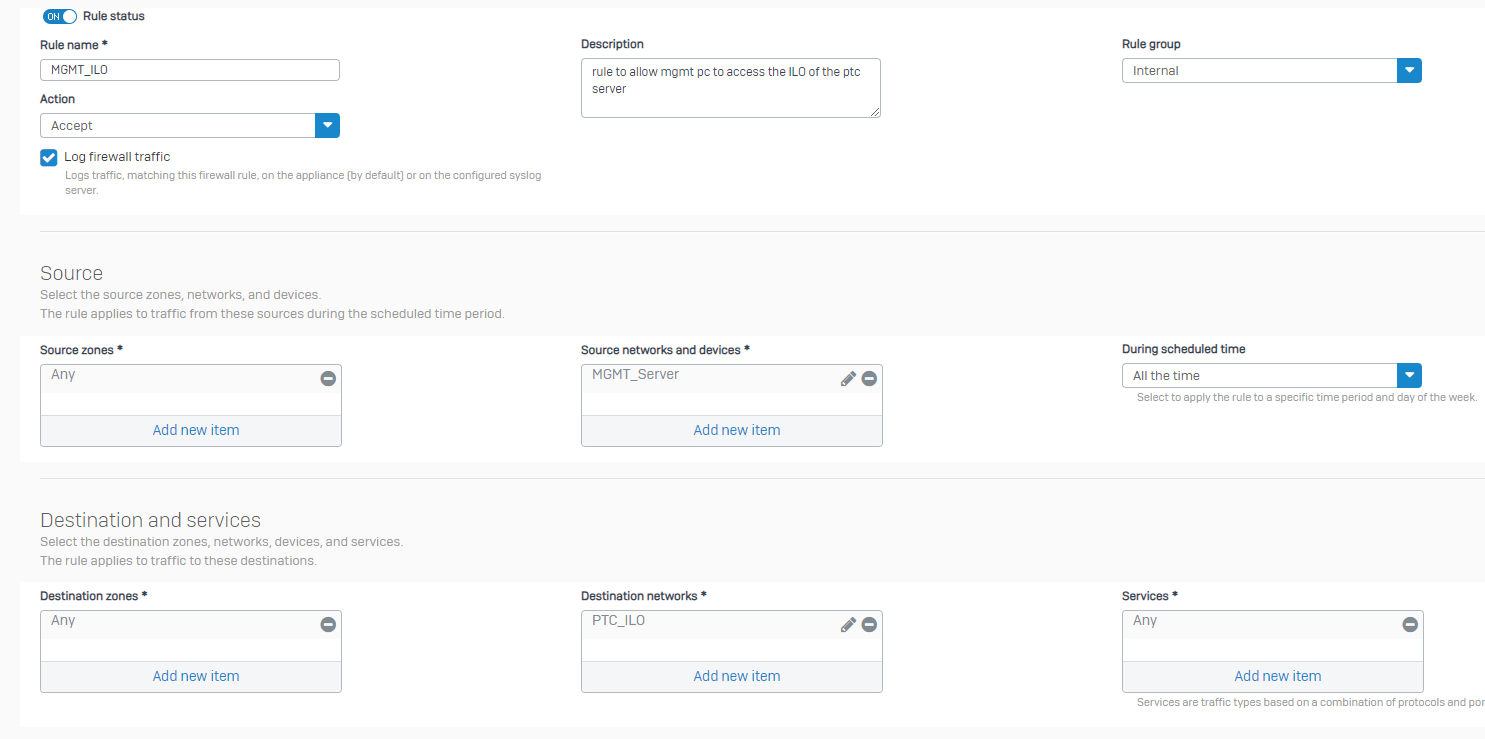
In the firewall logs I can see the rule being hit and being allowed.
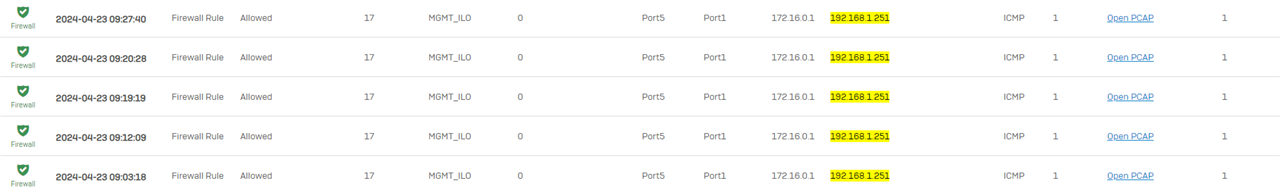
What am I missing? I know the ilo is working fine as it is reachable from the lan network server so ive got past it being a physical (cable, connection) issue.
This thread was automatically locked due to age.


