Hello, I work on 2 Sophos XG on 2 different sites. They communicate with each other using a Site-to-Site IPSec VPN.
- Site A : Sophos-XGS 33100 (SFOS 19.5.3)
- Site B : Sophos-XG 330 (SFOS 19.5.3)
3 subnets of Sophos A are configured to be able to communicate through the VPN.
- Network A : Management
- Network B : Backup
- Network C
Each subnet has a dedicated VLAN and a virtual interface used as a gateway.
The auto-generated packets by the Sophos of site A destined for site B are automatically sent through the gateway of Network B (Backup). I am trying to know how to select the interface on which the packets auto-generated by the Sophos of the site A will be sent to the site B.
Original need
I wanted to connect the Sophos firewall on site A to an LDAP server located on site B. So I added the connection information to my LDAP server in "Authentication > Servers". When I did a connection test, the “Packet capture” diagnostics tool displayed the IP of the gateway of network B “Backup” as the source IP of the dedicated auto-generated packets.

However, I wanted the IP to be the one of the management networks (or another dedicated to it). I couldn't find any settings on the "AD server" part.
Temporary solution
I realized that the choice of gateway used for sending auto-generated packets is not random. This is actually the gateway for the first subnet allowed in my site-to-site VPN configuration. By changing the name of my network A “Management”, the placing in alphabetical order moves it to the first position.
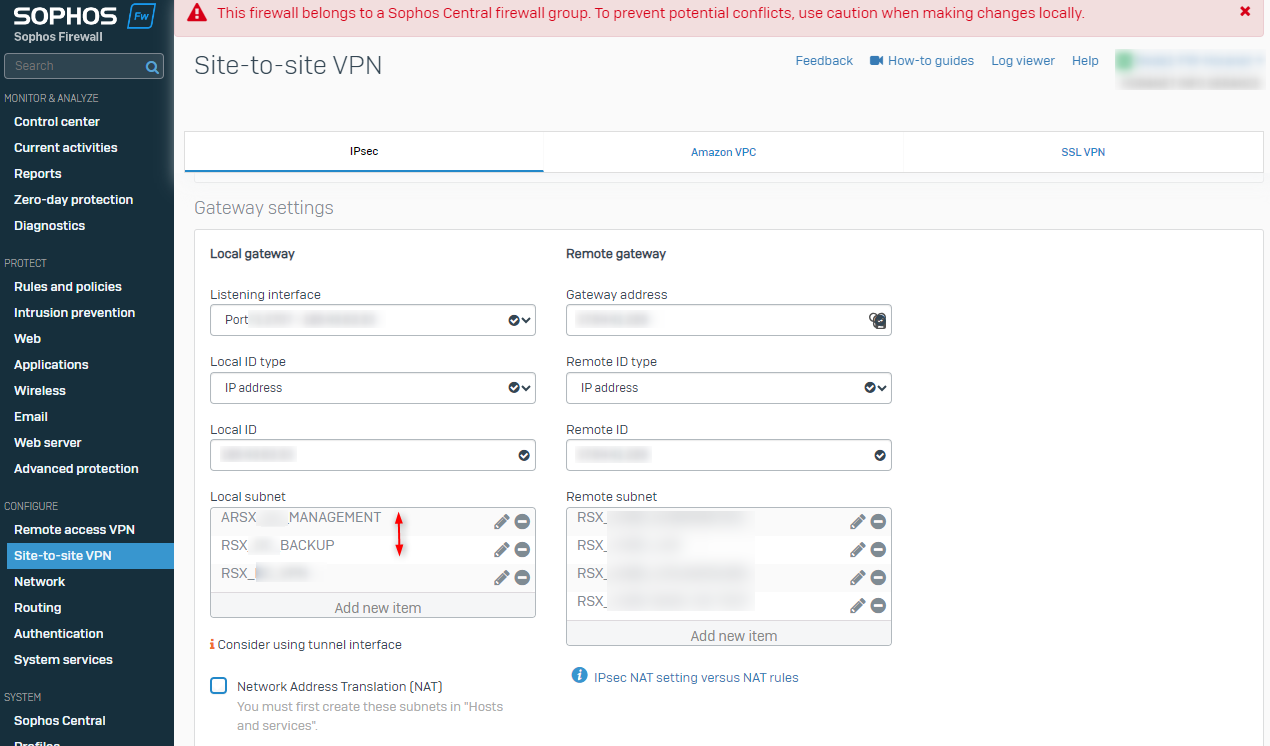
After applying the changes, the source IP of my packets was indeed the one of my management network.

It works well but I don't find it very clean and intuitive. In addition, my networks and their names may change in the future.
Desired solution
I want to be able to clearly define which gateway to use. I studied a few options such as configuring an IPSec route, but I'm not sure that it’s what I need...
Would anyone be able to answer my needs or give me a lead please?
This thread was automatically locked due to age.


