Hello there,
I am trying to connect to the VPN using the command line "sccli". When there no One Time Password, it works without a problem. But when OTP is active, I can't seem to get it done. I came across this post that says to use {PASSWORD}{TIMEOTP} together as the password field, but no luck there. It really seems that the OTP is not being sent.
This is my output:
C:\Users\Administrator>"C:\Program Files (x86)\Sophos\Connect\sccli" enable -V -n "IPSec_Tunnel" -u "myusername" -p "mypassword123456"
Connection 'IPSec_Tunnel' will be enabled
Username 'myusername' will be used
Password 'mypassword0123456' will be used
Sending JSON to the server:
{
"enable": {
"name": "IPSec_Tunnel",
"pass": "mypassword123456",
"user": "myusername"
},
"waitfor": 10000
}
Received JSON from the server:
{
"cbid": 3,
"code": 0,
"connections_uid": 10,
"status": {
"args": [],
"id": 0
}
}
The connection has been enabled
C:\Users\Administrator>"C:\Program Files (x86)\Sophos\Connect\sccli" list -d
Connections:
IPSec_Tunnel
Display Name: IPSec_Tunnel
Gateway: [REDACTED]
VPN Type: ipsec
Auto-Connect: not available
IKE version: 1
Last connect time: Sat Jan 20 06:40:07 2024
Last connect result: 0
Latency: unknown
Favicon: not present
User authentication type: XAuth
IKE authentication type: certificates
VPN state: disconnected
Auth state: need one-time password
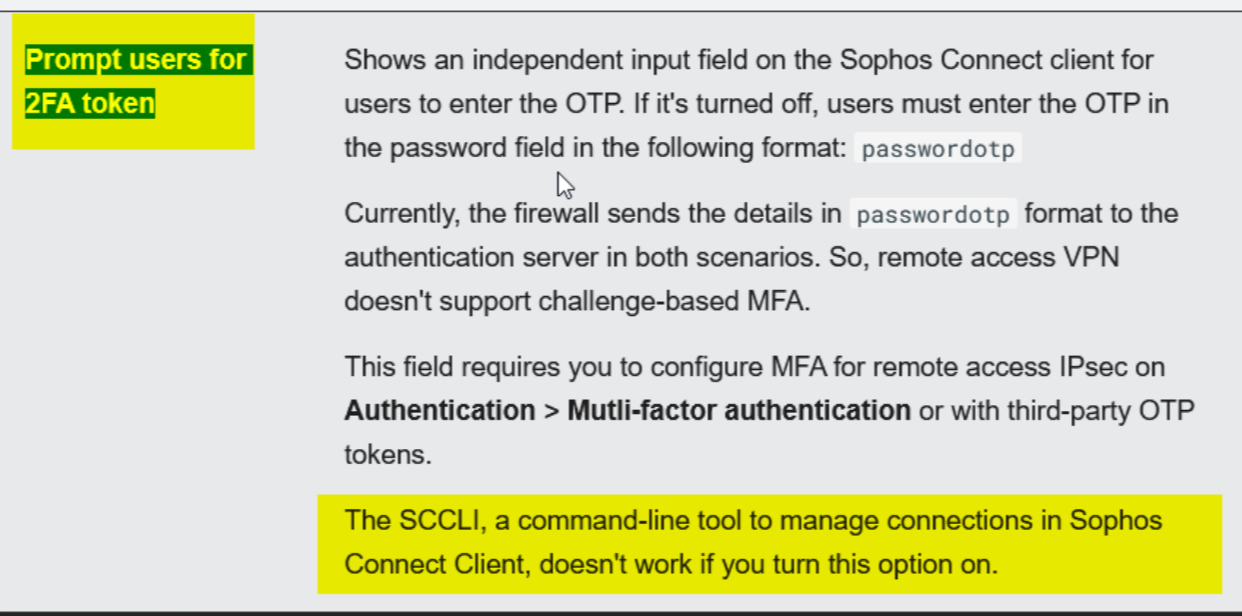
Feature request: there should be an easy option like -o 123456 to make things clearer.
Is there a proven way to do it? I could imagine the "_" creating a problem, but other than that it only seems the sccli does not work with OTP.
Any help is appreciated.
Cheers
This thread was automatically locked due to age.