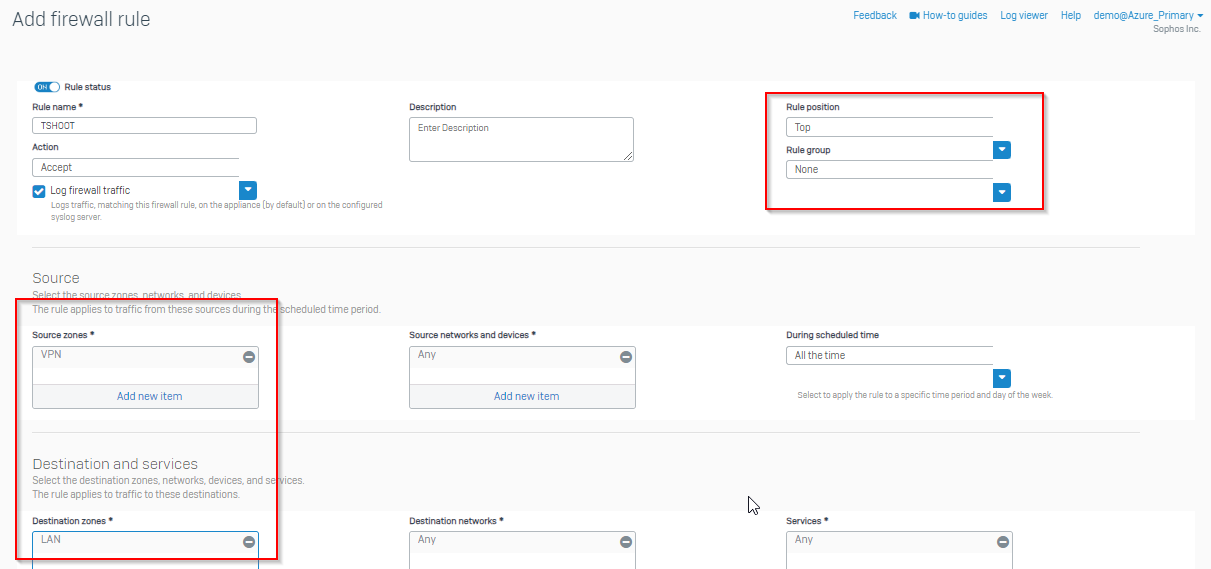
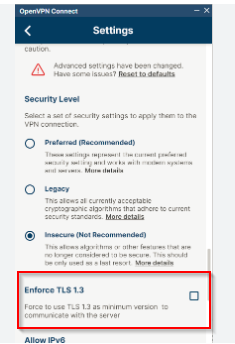
Hello,
We have the OpenVPN client running on various Android phones that connects to an XGS 116w (SFOS 19.5.3 MR-3-Build652). The whole thing worked without any problems until a few days ago. Since then, some - not all - devices can successfully open a VPN connection, but no packets seem to be sent into the tunnel.
I have already reinstalled OpenVPN and reloaded and imported the connection profile. Without success.
If I load the same profile on an iOS, it works without any problems.
Does anyone have any idea what the problem could be?
The OpenVPN logs show the following:
----- OpenVPN Start ----- [Jan. 29, 2024, 10:33:33] EVENT: CORE_THREAD_ACTIVE [Jan. 29, 2024, 10:33:33] OpenVPN core 3.8.4connectX(3.git::c424d46c:RelWithDebInfo) android arm64 64-bit PT_PROXY [Jan. 29, 2024, 10:33:33] Frame=512/2112/512 mssfix-ctrl=1250 [Jan. 29, 2024, 10:33:33] NOTE: This configuration contains options that were not used: [Jan. 29, 2024, 10:33:33] Unsupported option (ignored) [Jan. 29, 2024, 10:33:33] 3 [explicit-exit-notify] [Jan. 29, 2024, 10:33:33] 4 [resolv-retry] [infinite] [Jan. 29, 2024, 10:33:33] 6 [persist-key] [Jan. 29, 2024, 10:33:33] 7 [persist-tun] [Jan. 29, 2024, 10:33:33] 15 [route-delay] [4] [Jan. 29, 2024, 10:33:33] EVENT: RESOLVE [Jan. 29, 2024, 10:33:33] Contacting 1.2.3.4:8448 via UDP [Jan. 29, 2024, 10:33:33] Connecting to [vpn.domain.de]:8448 (1.2.3.4) via UDP [Jan. 29, 2024, 10:33:33] EVENT: WAIT [Jan. 29, 2024, 10:33:33] EVENT: CONNECTING [Jan. 29, 2024, 10:33:33] Tunnel Options:V4,dev-type tun,link-mtu 1570,tun-mtu 1500,proto UDPv4,comp-lzo,cipher AES-256-CBC,auth SHA256,keysize 256,key-method 2,tls-client [Jan. 29, 2024, 10:33:33] Creds: Username/Password [Jan. 29, 2024, 10:33:33] Sending Peer Info: IV_VER=3.8.4connectX IV_PLAT=android IV_NCP=2 IV_TCPNL=1 IV_PROTO=990 IV_MTU=1600 IV_CIPHERS=AES-128-CBC:AES-192-CBC:AES-256-CBC:AES-128-GCM:AES-192-GCM:AES-256-GCM:CHACHA20-POLY1305 IV_LZO=1 IV_LZO_SWAP=1 IV_LZ4=1 IV_LZ4v2=1 IV_COMP_STUB=1 IV_COMP_STUBv2=1 IV_GUI_VER=net.openvpn.connect.android_3.4.0-9755 IV_SSO=webauth,openurl,crtext [Jan. 29, 2024, 10:33:33] VERIFY OK: depth=3, /C=GB/ST=Greater Manchester/L=Salford/O=Comodo CA Limited/CN=AAA Certificate Services, signature: RSA-SHA1 [Jan. 29, 2024, 10:33:33] VERIFY OK: depth=2, /C=US/ST=New Jersey/L=Jersey City/O=The USERTRUST Network/CN=USERTrust RSA Certification Authority, signature: RSA-SHA384 [Jan. 29, 2024, 10:33:33] VERIFY OK: depth=1, /C=GB/ST=Greater Manchester/L=Salford/O=Sectigo Limited/CN=Sectigo RSA Domain Validation Secure Server CA, signature: RSA-SHA384 [Jan. 29, 2024, 10:33:33] VERIFY OK: depth=0, /CN=*.domain.de, signature: RSA-SHA256 [Jan. 29, 2024, 10:33:33] SSL Handshake: peer certificate: CN=*.domain.de, 2048 bit RSA, cipher: TLS_AES_256_GCM_SHA384 TLSv1.3 Kx=any Au=any Enc=AESGCM(256) Mac=AEAD [Jan. 29, 2024, 10:33:33] Session is ACTIVE [Jan. 29, 2024, 10:33:33] Sending PUSH_REQUEST to server... [Jan. 29, 2024, 10:33:33] EVENT: WARN info='TLS: received certificate signed with SHA1. Please inform your admin to upgrade to a stronger algorithm. Support for SHA1 signatures will be dropped in the future' [Jan. 29, 2024, 10:33:33] EVENT: GET_CONFIG [Jan. 29, 2024, 10:33:34] Sending PUSH_REQUEST to server... [Jan. 29, 2024, 10:33:34] OPTIONS: 0 [route-gateway] [10.81.234.1] 1 [sndbuf] [0] 2 [rcvbuf] [0] 3 [ping] [45] 4 [ping-restart] [180] 5 [route] [192.168.1.0] [255.255.254.0] 6 [route] [192.168.7.0] [255.255.255.0] 7 [topology] [subnet] 8 [route] [remote_host] [255.255.255.255] [net_gateway] 9 [inactive] [3600] [30720] 10 [dhcp-option] [DNS] [192.168.120.1] 11 [dhcp-option] [DNS] [9.9.9.9] 12 [dhcp-option] [DOMAIN] [customer.net] 13 [ifconfig] [10.81.234.2] [255.255.255.0] 14 [peer-id] [0] 15 [cipher] [AES-256-GCM] 16 [block-ipv6] 17 [block-ipv4] [Jan. 29, 2024, 10:33:34] PROTOCOL OPTIONS: cipher: AES-256-GCM digest: NONE key-derivation: OpenVPN PRF compress: ANY peer ID: 0 [Jan. 29, 2024, 10:33:34] EVENT: ASSIGN_IP [Jan. 29, 2024, 10:33:34] exception parsing IPv4 route: [route] [remote_host] [255.255.255.255] [net_gateway] : addr_pair_mask_parse_error: AddrMaskPair parse error 'route': remote_host/255.255.255.255 : ip_exception: error parsing route IP address 'remote_host' : Invalid argument [Jan. 29, 2024, 10:33:34] Connected via tun [Jan. 29, 2024, 10:33:34] LZO-ASYM init swap=0 asym=1 [Jan. 29, 2024, 10:33:34] Comp-stub init swap=1 [Jan. 29, 2024, 10:33:34] EVENT: CONNECTED info='support@vpn.domain.de:8448 (1.2.3.4) via /UDP on tun/10.81.234.2/ gw=[10.81.234.1/] mtu=(default)' trans=TO_CONNECTED [Jan. 29, 2024, 10:33:34] EVENT: COMPRESSION_ENABLED info='Asymmetric compression enabled. Server may send compressed data. This may be a potential security issue.' trans=TO_DISCONNECTED [Jan. 29, 2024, 10:34:59] EVENT: CANCELLED [Jan. 29, 2024, 10:34:59] EVENT: DISCONNECTED [Jan. 29, 2024, 10:34:59] Tunnel bytes per CPU second: 0 [Jan. 29, 2024, 10:34:59] ----- OpenVPN Stop ----- [Jan. 29, 2024, 10:34:59] EVENT: CORE_THREAD_DONE
Thanks
This thread was automatically locked due to age.