Hello!
I'd like to ask for your help, I've been using this great firewall for several years, but now I'm stuck.
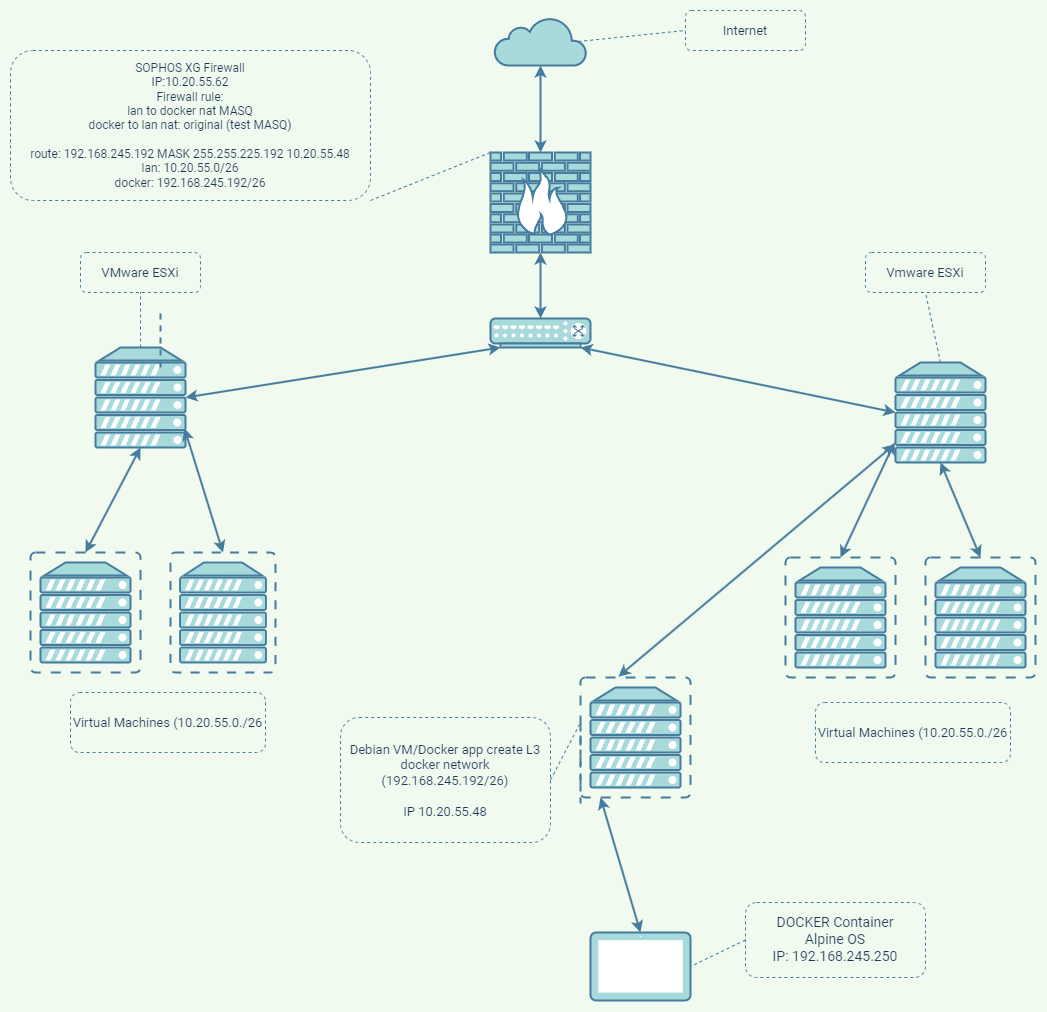
I have a small network at home in which I installed a docker host for testing purposes.
I have found the best way to allow the docker containers to access the home network is to configure the docker network to create an L3 network.
The LAN-->LAN firewall rule is created, the routing table is created, but from the docker container I can only ping the firewall IP address, no other hosts from the home network.
The return path works fine so I can reach containers from any host at home.
Another interesting thing is that when I ping one of the hosts in my home network from the container, the reply back is stuck, so the host's reply is thrown away by the firewall. But if I ping the same container from the same host, the response arrives fine, the firewall when pinging any host from the container it writes ICMP packets with invalid ICMP type/code.
Please help.
This thread was automatically locked due to age.