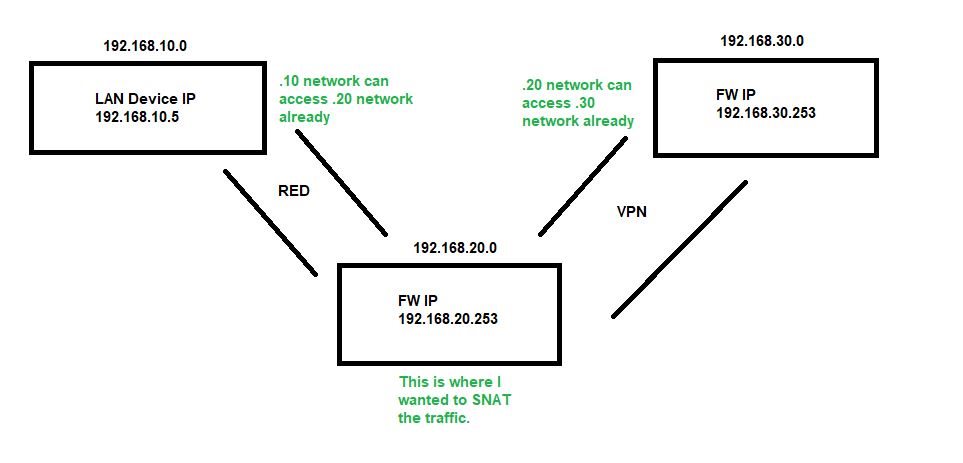
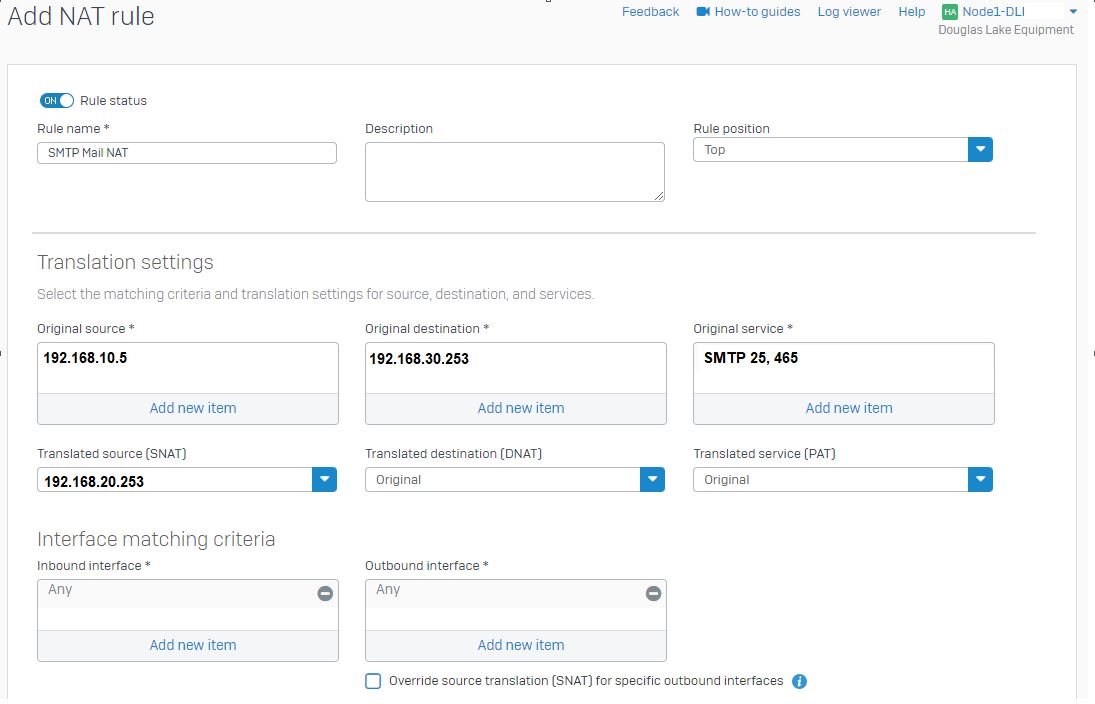
Just a question here. I have a red device in a small office(lets call it 192.168.10.0). That red device is connected to an xgs firewall(firewall 1, 192.168.20.0), and this firewall has a vpn connection to firewall 2(192.168.30.0). The vpn only passes traffic between the 192.168.20.0 and 192.168.30.0 networks. I wanted to allow one ip on the 192.168.10.0 network to talk to one ip on the .30 network. I tried to set up a NAT on firewall 1 to SNAT traffic from the .10 ip and replace the source with the .20 network internal interface. Nothing i did would make this work. Any Ideas?
|RedDevice| ->> xgs firewall 1 ->> VPN ->> xgs firewall 2
This thread was automatically locked due to age.