Hi to All Sophos Gurus,
Good day.
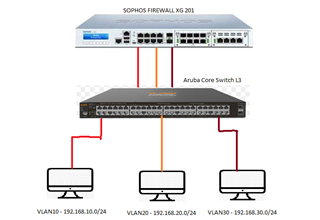
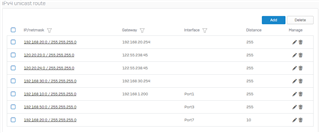
I have been fixing my vlan routing in my Sophos XG 210 Firewall. I created different gateways for each VLANs. Below are the details.
VLAN10 :
IP = 192.168.10.0/24
DG = 192.168.10.254
ISP1
VLAN20 :
IP = 192.168.20.0/24
DG = 192.168.20.254
ISP2
VLAN30 (Wireless) :
IP = 192.168.30.0/24
DG = 192.168.30.254
ISP3
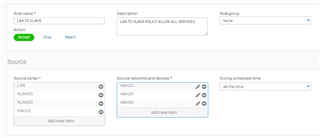
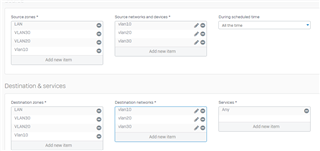
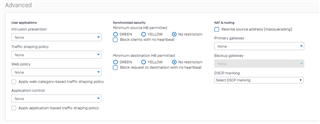
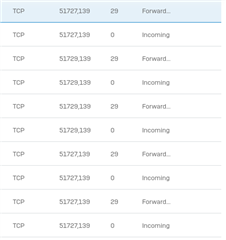
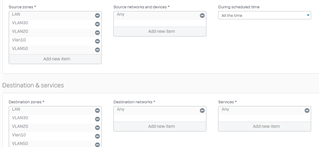
I have all my servers on VLAN10. I wanted to share my fileservers in VLAN10 to all other VLANs. I already created a firewall rule in my SOPHOS. The problem I cannot access my fileservers. Did I do something wrong. Someone might be able to help me. Below is a screenshot of my network diagram and firewall policies LAN to LAN.
Network Diagram
Firewall VLAN to VLAN Policy.
If anyone can give me an idea it would be great!
Thanks
Rodney
This thread was automatically locked due to age.