Hello everyone,
New to XG line, trying to block only the specific "URL group" for every user while only authenticated user group ("managers") that can login and access blacklisted websites listed in the group.
Issue is that:
a) every website is blocked for non-authenticated users not just our blacklisted few in the URL group.
b) when user authenticates then they are allowed to view ONLY blacklisted websites and nothing else.
---- our top firewall rule ---
Rule
Apply "Allow All" app filter, "Block Blacklisted Websites" web filter, for any user, when in "LAN" zone, and coming from any network
Source & schedule
LAN
Source networks and devices : Any
During scheduled time : All the time
Destination & services
WAN
Destination networks : Any
Services : Any
Identity
Any
---
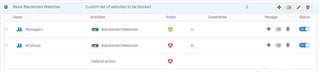
-- our web policy Block Blacklisted Websites --
What is the best approach here?
Thanks you!
This thread was automatically locked due to age.