Hi,
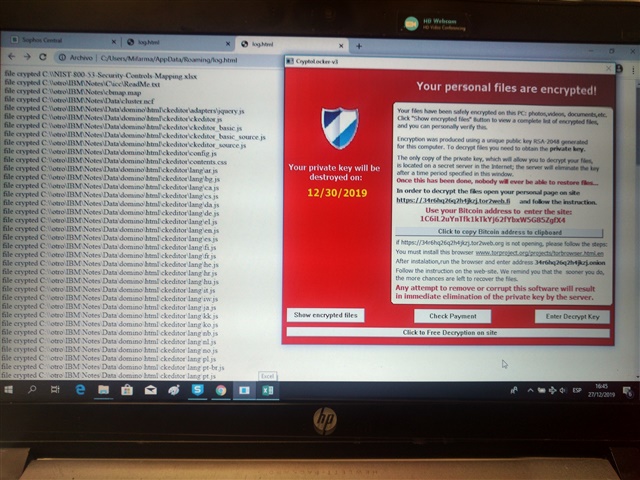
I would like to know if only Intercept X is enough to protect a computer from Cryptolocker v3 and Sucylocker ransomware.
If isnt enough, will Central InterceptX Advanced be the solution to fully protect the computer from ransomware?
Thanks.
This thread was automatically locked due to age.