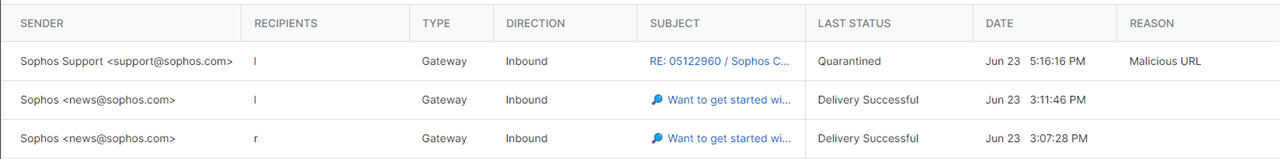
we have received an e-mail using an alias/send as from one of our domains. The e-mail was allowed through and leads to a malicious url. We have enabled the setting in E-mail Security to reject e-mails that impersonate one of our domains:
|
Header anomalies
|
Email that appears to come from your own domain, but originates externally
|
Now it wasn’t rejected but as this sender does not match our spf or dmarc we feel it should have been quarantined next. It didn’t, not as far as I can see in the logs as it only gives delivered successfully.
Sophos Support claims it is a false positive and that I should send it to Sophos Labs. I can’t do anything with such support answers.
Questions: is send as / alias from a non-domain email adress using a send as / alias of one of our e-mail domains not picked up by:
a] header anomalies?
b] spf and dmarc settings?
Regards,
Fred
Added tags
[edited by: Raphael Alganes at 5:59 AM (GMT -7) on 7 Jun 2023]