[Update: found workaround]]
I changed the script that it will produce a batch file with curl and execute this. result is that the endpoints are removed as wished.
[Edited due adding full script]]
Dear Community,
I run in an issue I do not understand.
I wrote a powershell script which should delete endpoints in a specific group.
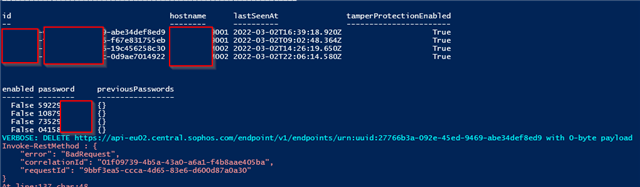
Enabling/disabling tamper works (non-destructive script testing), but when I execute the delete, it always fails with
Invoke-RestMethod : { "error": "BadRequest", "correlationId": "d8889e3a-5914-4d68-bb5a-2765467c17d7", "requestId": "c78db0c0-6bf7-40e5-968b-510cd7cb1d6f"}At line:3 char:13+ $response = Invoke-RestMethod 'api-eu02.central.sophos.com/en ...+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ + CategoryInfo : InvalidOperation: (System.Net.HttpWebRequest:HttpWebRequest) [Invoke-RestMethod], WebException + FullyQualifiedErrorId : WebCmdletWebResponseException,Microsoft.PowerShell.Commands.InvokeRestMethodCommand
The used command:
Invoke-RestMethod 'api-eu02.central.sophos.com/.../xxxxxx-xxx-45ed-9469-abe34def8ed9' -Method 'DELETE' -Headers $Headers
Anyone any idea?
the api token role is superadmin, so this should not be an issue.
[script]
I would love to hear your thoughts.
Regards,
Arno
Update
[edited by: Arno van der Veen - IT's Secured at 7:38 PM (GMT -8) on 5 Mar 2022]