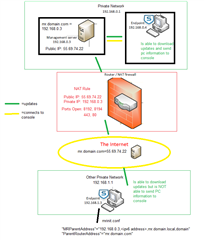
Hi guys,
I've been doing a ton of research and am still at a lost on how to proceed. We currently have Sophos Enterprise Console and endpoints only show up when they are connected to the network either directly or on VPN. We are having issues because a lot of our users work from home and do not contact the console until they reconnect to the VPN (if at all). We also have some servers that cannot connect to the VPN.
How do we get endpoints to contact the console when not connected to the network? I've read about message relay but still don't completely understand that. Can someone dummy it down for me, if that's the only way?
Thanks!
This thread was automatically locked due to age.