Update: 4/3/2020 - This test tool is no longer available. More info to come.
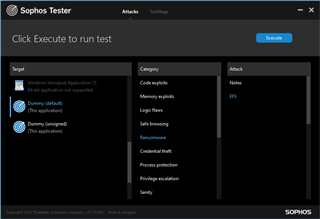
EFS Guard
Dummy (Unsigned) ⇒ Ransomware ⇒ EFS
Note: it is important to choose the unsigned version of "Dummy", as the signed version is allowed to encrypt files.
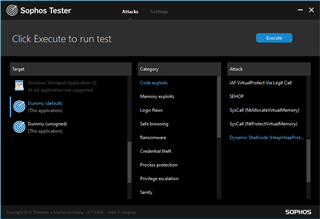
Dynamic Shellcode Protection
Dummy ⇒ Code exploits ⇒ Dynamic Shellcode (HeapHeapProtection)
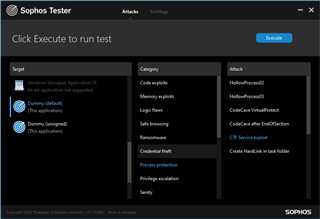
CTF Guard
Dummy ⇒ Process protection ⇒ CTF Service exploit
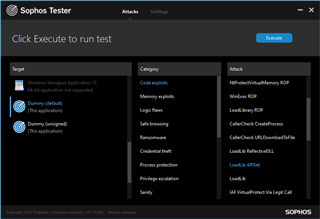
ApiSetGuard
Dummy ⇒ Code exploits ⇒ LoadLib APISet