Note: With special thanks to AK, mward19, Maxim-Sophos, and JoeLevy
This post provides information about Sophos XDR. It has three main sections:
- Data Sources
- Data Enrichment and Pivoting
- Integrations and API’s
Table of Contents
Data Sources
The Sophos Data Lake includes information from Sophos and non-Sophos data sources. While performing a threat-hunt, security analysts are not limited to the Sophos Data Lake. There are various data enrichment and pivoting options available to them, including pivoting to an endpoint or server to see real-time state and up to 90 days of historical data for a level of detail that a data lake alone could never offer.
Sophos Data Sources
- Endpoint (Sophos Intercept X Advanced with XDR)
- Server (Sophos Intercept X Advanced for Server with XDR)
- Firewall (Sophos Firewall)
- Email (Sophos Email Advanced)
- Mobile (Sophos Mobile Advanced, Sophos Intercept X for Mobile)
- Cloud (Sophos Cloud Optix)
Non-Sophos Data Sources
- Amazon AWS
- Microsoft Azure
- Microsoft 365 / Office 365 user and app audit activity (Coming soon)
- Third party firewall (Coming soon)
- Okta (Coming soon)
Endpoint (Sophos Intercept X Advanced with XDR)
Intercept X Advanced with XDR enables access to detailed Windows and macOS information in on-premises, cloud and virtual environments for endpoint devices.
|
Data Access |
Sophos Data Lake On Device: real-time state and up to 90 days of rich historical data |
|
Schema |
|
|
Example use cases |
|
Server (Sophos Intercept X Advanced for Server with XDR)
Intercept X Advanced for Server with XDR enables access to detailed Windows and Linux information in on-premises, cloud and virtual environments for servers and cloud workloads (AWS, Azure, GCP and Oracle).
|
Data Access |
Sophos Data Lake On Device: real-time state and up to 90 days of rich historical data |
|
Schema |
|
|
Example use cases |
|
Firewall (Sophos Firewall)
Sophos Firewall enables access to rich network data in on-premises, cloud and virtual deployments.
|
Data Access |
Sophos Data Lake |
|
Schema |
|
|
Example use cases |
|
Email (Sophos Email Advanced)
Sophos Email Advanced delivers rich email data from Office 365 deployments.
|
Data Access |
Sophos Data Lake |
|
Schema |
|
|
Example use cases |
|
Mobile (Sophos Mobile) – Coming Soon
Sophos Mobile Advanced delivers rich mobile configuration and usage data across Andoid, iOS, and ChromeBooks.
|
Data Access |
Sophos Data Lake |
|
Schema |
To be published |
|
Example use cases |
|
Cloud (Sophos Cloud Optix)
Cloud Optix Advanced provides access to key data from cloud deployments including workloads, security groups, containers, serverless functions and more across AWS, Azure, GCP and Oracle deployments.
|
Data Access |
Sophos Data Lake |
|
Schema |
|
|
Example use cases |
|
Data Enrichment and Pivoting
Security analysts can use telemetry and data from various resources to further understand a detection.
In Sophos XDR there is a concept of a Pivot. A pivot lets you select a significant piece of data (for example: a hash, IP address, device name, path, etc.) in a detection and use it as the basis for further investigation.
Pivots can be accessed by clicking on the ellipsis next to a particular item. Depending on the data type, a set of possible options will be displayed.
- Queries: You can run a query based on the data selected. Live Discover queries look at data on your devices both real-time state and up to 90 days of rich historical data. Data Lake queries look at the data that has been upload to the Sophos Data Lake.
- Enrichments: These open third-party services like VirusTotal or IP Abuse DB to look up information about a potential threat.
- Actions: These offer further detection or remediation. For example, you can scan a device, or start Sophos Live Response to access and investigate a device.
In the example shown below, clicking the icon beside the IP address lets you run queries based on that IP address or look up third-party information about risks associated with it.
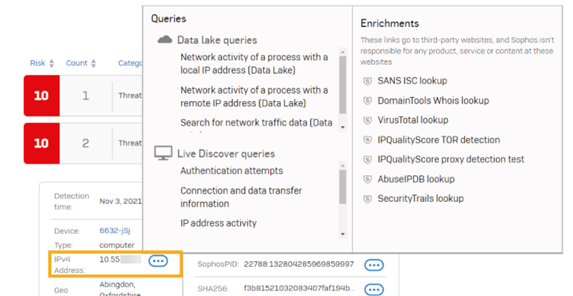
Sophos provides a number of default pivots and data enrichments for various data types. Security analysts can create their own pivots and enrichments, whether that is searching the Sophos Data Lake, or an external resource. Sophos XDR will learn from the behavior of the security analyst and present the pivots/enrichments used most frequently used as the first options.
Web Services
Enrichments are user programable. Any web service is potentially an enrichment, and security analysts can access internet-based repositories for additional data like YARA rule repositories, compliance rules, threat actor information etc.
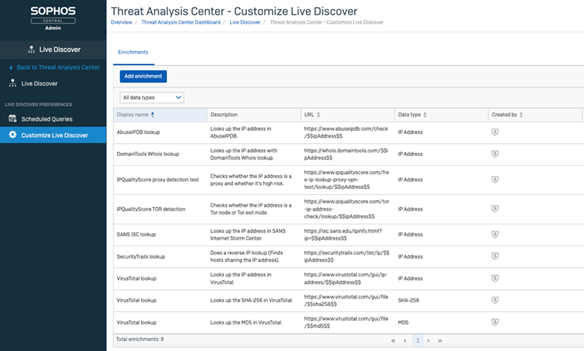
Additional reading
- Custom pivot options
- YARA Scanning rules with Sophos XDR
- Performing Suspect Power Shell Detection with a YARA Rule
Curl
Direct enrichment as part of Detection/Investigation can add context from any online resource accessible with curl.
A curl request can access internet hosted data for additional documents, rules or other data. The YARA scanning example from above connects out to the GIT project https://virustotal.github.io/yara/ to index the list of available YARA rules and to pull the current YARA rule down to the endpoint for execution.
Example Data Enrichments and Pivots
The following data enrichments and pivots are provided by Sophos
- VirusTotal
- SANS
- IP lookup
- Domain classifications
- Geo location for Device and IP address information
Integrations and APIs
Integrations
Sophos Central is an open platform with an ever-expanding set of integration and API Partners. For the latest list, please refer to Sophos.com.
APIs
Sophos Central has exposed APIs to automate security and management workflows. Information on getting started, how the APIs work, and API document can be found on the Sophos Developer website.
The Sophos Community is a location where Sophos, Sophos Partners and Customers share valuable information.
Customers can use SIEM and data management solutions to ingest data via the SIEM Integration API.
SophosLabs Intelix allows anyone to leverage the technology behind SophosLabs through a suite of RESTful APIs.
Recommended reading

