For query assistance, please see the following Best Practices guide
With XDR we have access to the OSQuery supported tables and the ability to write our own SQL queries that can include variables. One of the tables available is a YARA table. This allows you to supply a signature file and path and the underlying engine in OSQuery will perform a search for files that match the signature. Very old skool malware hunting I know, but folks find it useful for emerging threats where vendors may not have updated their proprietary malware protection engines yet.
To learn more about YARA rules check out the 'readthedocs' https://yara.readthedocs.io/en/stable/ and here https://virustotal.github.io/yara/
Threat intelligence forums provide YARA rules to define the Indicator of Compromise they have associated to malicious activity. One popular public location for YARA rules is in a GIT repo.
https://github.com/Yara-Rules/rules
The current version of OSQuery included with XDR is 4.6 for Mac and LINUX and 4.7 for Windows This fall we are going to upgrade to OSQuery version 4.9 where a new YARA rules engine will be supported on windows, so I started thinking about how to write a YARA scanning engine that would take a YARA rule and perform the scan. To my surprise the YARA table is available and appears to work fine in version 4.7.
I wanted to build a few tools that could leverage the support for OSQuery and the public repository of rules. Below are the new queries I wrote. For folks looking to use this I strongly encourage you use your own hosting site for your YARA rules and examine any rule before you run it so you understand what it is looking for. A 'hit' with a YARA rule is not a confirmation of malware it is only confirmation that whatever the rule was found a match and the ability to accurately classify malware will only be as good as the rule.
Search for A Yara rule:
This query will download the Index file of current yara rules from ttps://github.com/Yara-Rules/rules and then search for any rules that match the variable. We automatically add the wildcards '%' to the string for a broader match capability. The results are the Yara rule URL and the signature YARA file itself. This is a live query so it is running on the device you selected and it takes a while to execute. It has to download a few KB of data that it converts to a virtual table that it then searches. If it finds any matches it has to go back to the website to pull the actual file down for the results we will show.
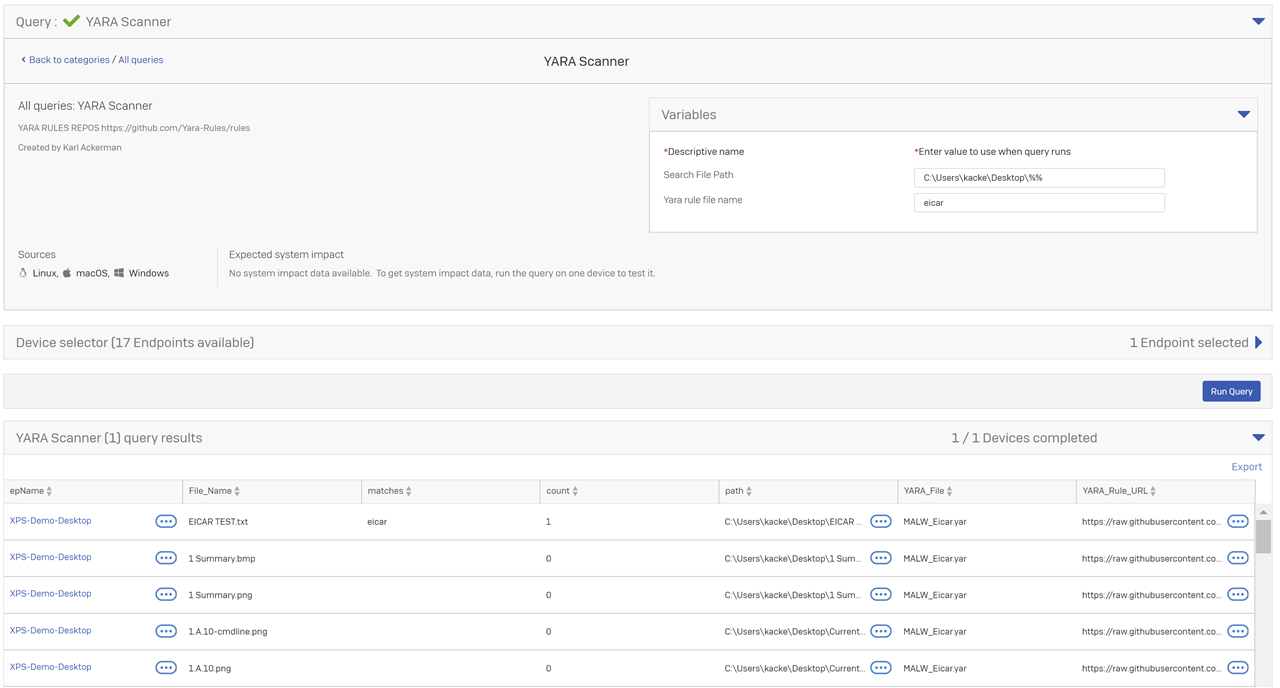
Perform a SCAN using an online YARA File.
The returned data above includes the URL for the raw rule file and with that you can PIVOT to the next query that will take that URL and an admin supplied path to perform the scan.
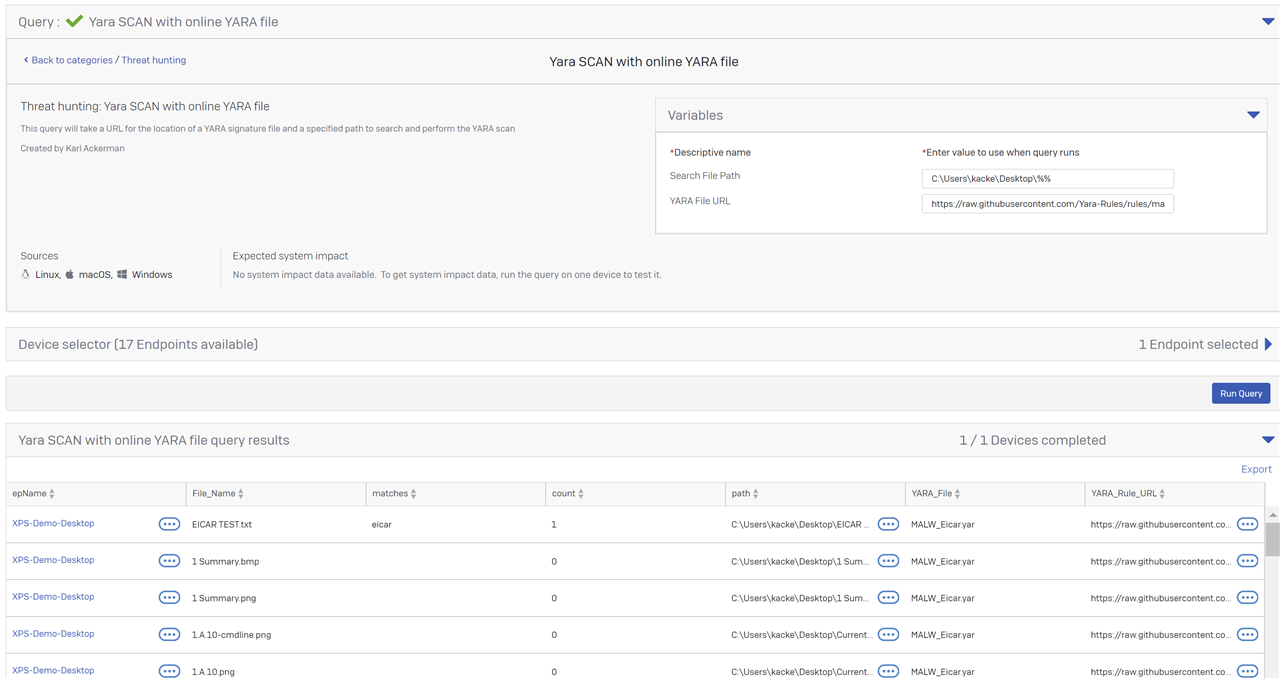
This one is MUCh faster as you already know the location of the YARA signature file you want to run.
SEARCH (for 'malware' + PIVOT on 'eicar' + RUN THE SCAN 'for the target directory and sub directories''
Now run the Scan for the specified path.
Source Code:
For the last bit of work I wanted a scanner that could run a rule by name on a path without having to first search for the rule. This one takes the approximate name of a rule, searches the index of currently published rules and finds any matches. For each matching YARA Signature it will run that on the specified path. This way you can run multiple YARA rules on a file or directory and sub directories. DO NOTE that the watchdog might kill the query if it starts to consume too much memory or CPU. You can use wildcards so you can ask the system to scan with all 480 yara rules across the entire drive, but the watchdog will surely be unhappy and kill the query to ensure the end user experience is acceptable.

SEE ALSO the recommended reading on how to use a query for classification on powershell scripts. :
Have fun, I am off to write a MITRE TTP Scanner for NIX (Linux and MAC OS)
