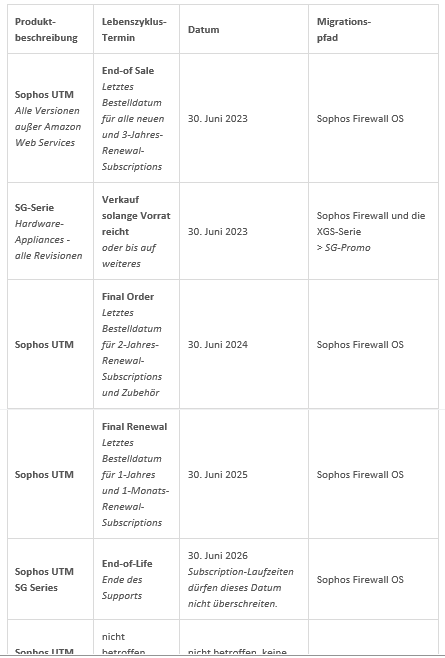
Finally, Sophos announced the EOL of UTM. Interestingly, the EOL does not apply to Sophos UTM AWS....
This thread was automatically locked due to age.
Still a hard pill to swallow... The decision to phase out a superior product in favor of developing this Cyberoam EXPLITIVE DELETED!
I think my first attempt to replace the UTM will be with Opnsense but I still have a lot of research to do. XG will be a last resort for me, if at all.
For those that utilized the UTM's SMTP proxy, what's available as a replacement? I haven't come across anything that's free or very low cost for home use. I hate the idea of throwing an email server on the edge even if it does have some spam and anti-virus capabilities.
--------------------------------------------------------------------
Sophos UTM 9.719-3 - Home User
Virtual machine on Dell Optiplex 3070
i3-9100 @ 3.60 GHz, 16 GB RAM
--------------------------------------------------------------------
Ironically that's what I spend the last week doing, although I never used utm's smtp proxy.
The webhost I use has a datacenter in NY that was recently shut down for 3-4 days due to a fire. While there are other options, I decided to try self hosting. My fiber connection gives me a pseudo static ip - last changed a few months ago after being the same for over 5 years.
I'm running something called mailcow which appears to be a reasonable AIO package for email including spam control. Another one I tried was mailinabox but that required more advance knowledge to configure. The cow product was deemed more attractive
As for opnsense, i'm passing on that. It's UI just doesn't make sense to me (much like xg's). Also pfsense has recently made improvements so I can connect it directly to the ethernet coming off the fiber media converter without any complication. This could be done in the past too but required additional software to authenticate the connection.
Good luck with what ever you choose.
I'm still going back and forth on pfSense vs OPNsense. I'm leaning towards OPNsense because it supports Zenarmor out of the box.
Are you active on the netgate forum? How about you Amodin ?
--------------------------------------------------------------------
Sophos UTM 9.719-3 - Home User
Virtual machine on Dell Optiplex 3070
i3-9100 @ 3.60 GHz, 16 GB RAM
--------------------------------------------------------------------
I was active on netgate forum in the att bypass thread. Their whole implementation of 802.1x has been a bane of many customers who want/demand to run their own equipment without dealing with the spyware gateway.
Back in june worked with one of their devs to assist in testing patches to wpa_supplicant to allow for listening on vlan0 tagged traffic. That's part of the appear I suppose. Response from franco, the guy from opnsense just unwelcoming - https://forum.opnsense.org/index.php?topic=34403.0 .
Jeff I got a new post notification but can't find your mesage.
```
That right there tells me major frustrations are in our future. We have been so spoiled by Sophos UTM's ease of use and extraordinary feature set. I would have thought you could connect directly to the ONT with any firewall as I've always done with a Sophos box.
I'm still researching. I keep going back and forth on pfSense vs OpnSense; still not sure which one to go with. Trying to avoid getting elbows deep in one only to find that I need to switch to the other and start all over. I was leaning towards Opnsense because of the Zenarmor integration out of the box and I saw a video tutorial on NAXSI WAF integration . Seems people are having problems with Zenarmor on pfSense.
Are you using the CE or Plus version? I'm concerned that they may pull the rug out from under Plus users at some point and start charging.
```
The ONT/gateway/802.1x BS is strictly caused by att and no other. There's lots of threads on it on dslr, but the gist I gather is it has to do with legacy auth with dsl clients connecting. And of course keeping support KISS. I'm happy to say I was able to root my gateway, pull its certs and stick it back in the box it came from back in 2019. With UTM, a third party supplied the needed wpa_supplicant binary which I still use to this day to handle auth on reboots. In pfsense (and opnsense https://www.dslreports.com/forum/r33687955-OPNSENSE-vlan0-supporting-wpa-supplicant-binary) no additional tools are needed.
Now if I wanted to use XG, I have to have some convoluted work around to just get an IP, either by putting an openwrt vm in front of it, or some other way of handling eapol auth. Either way, its a none issue as xg won't be running here in its current form.
I've been playing with the plus version, but the latest CE 2.70 is (almost) in parity with the plus, or was a few weeks ago. I doubt netgate will charge home users, but who knows.
Truth be told, I probably won't be making the switch until this fall/winter given my network setup is somewhat complex and I really don't want to deal with it right now.
Jeff I got a new post notification but can't find your mesage.
```
That right there tells me major frustrations are in our future. We have been so spoiled by Sophos UTM's ease of use and extraordinary feature set. I would have thought you could connect directly to the ONT with any firewall as I've always done with a Sophos box.
I'm still researching. I keep going back and forth on pfSense vs OpnSense; still not sure which one to go with. Trying to avoid getting elbows deep in one only to find that I need to switch to the other and start all over. I was leaning towards Opnsense because of the Zenarmor integration out of the box and I saw a video tutorial on NAXSI WAF integration . Seems people are having problems with Zenarmor on pfSense.
Are you using the CE or Plus version? I'm concerned that they may pull the rug out from under Plus users at some point and start charging.
```
The ONT/gateway/802.1x BS is strictly caused by att and no other. There's lots of threads on it on dslr, but the gist I gather is it has to do with legacy auth with dsl clients connecting. And of course keeping support KISS. I'm happy to say I was able to root my gateway, pull its certs and stick it back in the box it came from back in 2019. With UTM, a third party supplied the needed wpa_supplicant binary which I still use to this day to handle auth on reboots. In pfsense (and opnsense https://www.dslreports.com/forum/r33687955-OPNSENSE-vlan0-supporting-wpa-supplicant-binary) no additional tools are needed.
Now if I wanted to use XG, I have to have some convoluted work around to just get an IP, either by putting an openwrt vm in front of it, or some other way of handling eapol auth. Either way, its a none issue as xg won't be running here in its current form.
I've been playing with the plus version, but the latest CE 2.70 is (almost) in parity with the plus, or was a few weeks ago. I doubt netgate will charge home users, but who knows.
Truth be told, I probably won't be making the switch until this fall/winter given my network setup is somewhat complex and I really don't want to deal with it right now.