As per the subject really
On my old FW (not Sophos) I used to allow access to pages internally (to our network) by checking the remote host http variable. This would give the users external (in the case of an external IP) or the internal (192.168.0.x) of an internal user. So I could lock out pages to external users
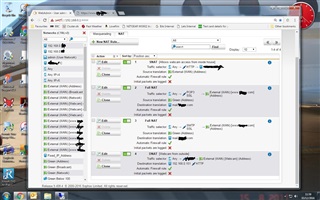
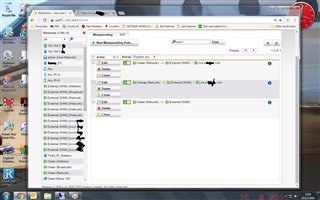
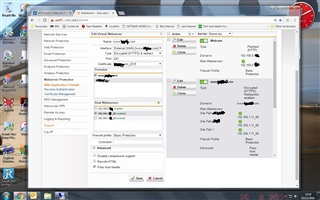
With Sophos UTM9 installed the remote_host is always shown as the DMZ IP address - 192.168.1.1. Therefore my apparantly secure pages are now visible externally
Is there a way to make this work as it used to? I can't see that NATing will help me in anyway
This thread was automatically locked due to age.