Hi,
first of all shouldn't this be documented by Sophos? How can one predict the ldap Attribute and Value?
Anyway,
I did what you suggested but still not getting it done.
Where Values, I suppose I leave it like that, not replacing with my credentials, right?
Is there something I can check on my freeipa server? Syslog not showing anything when I click on "test" on Sophos.
I think is time for Sophos to make a Document about how to connect Freeipa to Sophos hence there is already for AD and openldap is rubbish.
Thank you.
Never heard of your product. Does it have market share among potential paying customers for UTM?
Read my LDAP post in the WiKi. To make LDAP work, you have to know your available attributes, your directory structure, and LDAP syntax. The first comes from your LDAP vendor, the second from you, the third from the standards bidies or the web. You need to use your problem as your learning opoortunity.
There ARE critical holes in the documentation, which I and others have tried to address as we have learned the product. Everyone needs to read most everything in the wiki, to deploy the product securely, because of what is not in the manual. Additional resources are pinned to the top of most forum sections. So keep reading
But at the dane time, show gratitude that home users have access to such a powerful priduct for free.
Geiasou and welcome to the UTM Community!
You must [Save] a server definition first, and then you can [Test] it. I recommend that you use a unique user for the 'Bind DN' so that changing the admin password doesn't create issues for the UTM configuration.
Cheers - Bob
Geiasou and welcome to the UTM Community!
You must [Save] a server definition first, and then you can [Test] it. I recommend that you use a unique user for the 'Bind DN' so that changing the admin password doesn't create issues for the UTM configuration.
Cheers - Bob
Hi Bob,
I see you 've done some research (Geiasou) ;)
Are you administrating this site?
Well I would appreciate some exact directions and screenshots, for me and for the future generations :p
F.i.: Server Definition you mean: Definitions and users/network definitions/new network definition.
Choose: type: host
DNS settings-->Hostname: sub.example.com
save
Then go to network definitions/authentication services/servers/new authentication server
Choose the network definition you created before and fill in the Bind DN like this "uid=admin,cn=users,cn=accounts,dc=your_domain,dc=com"
Then it should work: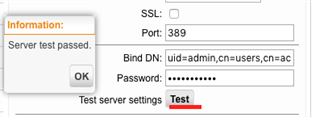
In my case I was previously trying to get it to work installing freeipa-server on Ubuntu 18 and this was a no go... I installed it on Fedora and it seems to be working.
However test does not work with 636 port and SSL activated. But I 'm happy for the moment and will dig deeper.
I 've no Idea how to set up users and groups in Sophos for LDAP but I just wanted to answer this one and will keep trying.
Cheers.
In fact, I had friends in university from Greece, but, yeah, languages, dialects and accents are a hobby.
No, just a Moderator, not an Administrator.
Saving authentication server definitions before testing is another one of those tricks that isn't documented. I hadn't noticed that the SSL option was added, but all of my clients use internal servers or connect to them via encrypted tunnels (RED/IPsec/SSL VPN). You might try creating a new server definition instead of changing from 389 to SSL 636 in an existing definition - did that work?
See #6 in Rulz for guidance on when users should be synced from the authentication server to the UTM. Configuring HTTP/S proxy access with AD SSO also applies to LDAP in most places. I think Douglas has a thread somewhere that delves more deeply into LDAP.
Cheers - Bob
Hi Bob,
then I guess we have the same hobby...
So, I created a "sophos" group and a "sophosuser" in freeipa.
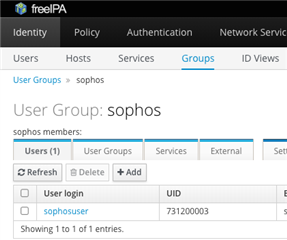
This user authenticates successfully under /authentication services/server/user authentication test
But when I try to log in to the firewall WebAdmin with this user I can't log in.
I have the feeling that I am missing something big here, so big that I can't see it :)
This is how ldap group in the firewall looks like: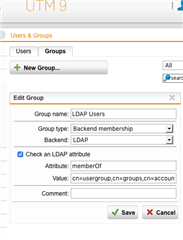
Should I create another group in the firewall? If yes, then how would that look like? The already existing "local" users would they be double then?
Thanx