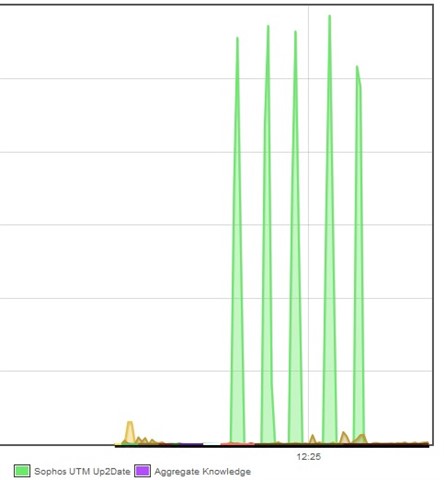
Recently (2-3 days) I've noticed regular periodic spikes of Up2Date traffic. Checking the flow monitor, I see a 5-6MB/s spike tagged Sophos UTM Upd2Date every 25 seconds. The total (in Top Clients by Application) was 142GB just yesterday.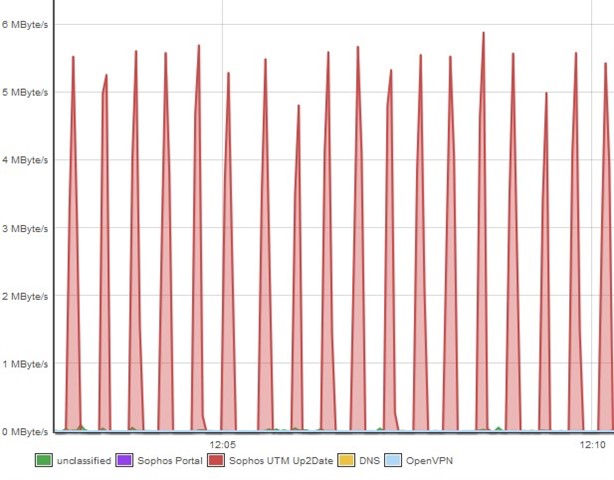
There's nothing unusual in the Up2Date log. Checks every 15 minutes with the occasional new pattern successfully installed. Nothing in the IPS log either except regular DNS Amplification Attacks every few minutes, but those have been happening for months.
I can't really see any way to debug this from within the firewall. Do I have to put a monitor on the outside interface and run a packet capture?
Thanks as always for suggestions,
Paul