We've just released SG UTM version 9.710. As usual, the release will be rolled out in phases:
- In phase 1 you can download the update package from our download server. Click the link and navigate to the folder UTM / v9 / up2date.
- Up2date package - 9.709 to 9.710 : https://download.astaro.com/UTM/v9/up2date/u2d-sys-9.709003-710001.tgz.gpg
- md5sum is e32b61bf168cf06181ca79ba325abb16 : https://download.astaro.com/UTM/v9/up2date/u2d-sys-9.709003-710001.tgz.gpg.md5
- During phase 2 we will make it available via our Up2Date servers in several stages.
- In phase 3 we will make it available via our Up2Date servers to all remaining installations.
This update removes the end-of-life SSLVPN client. It is no longer available to download from the User Portal. For more information see this end-of-life notice and this vulnerability disclosure.
With the standalone IPSec client also reaching end-of-sale on 30 March 2022, we have refreshed the remote access page of the User Portal to better support Sophos Connect. Sophos Connect is the recommended alternative to the old SSLVPN and IPSec clients. Download links on the User Portal now direct users to the Sophos Connect section on our downloads page. Configuration links have been updated to provide certificate packages and settings that can be imported by Sophos Connect to get users up and running quickly.
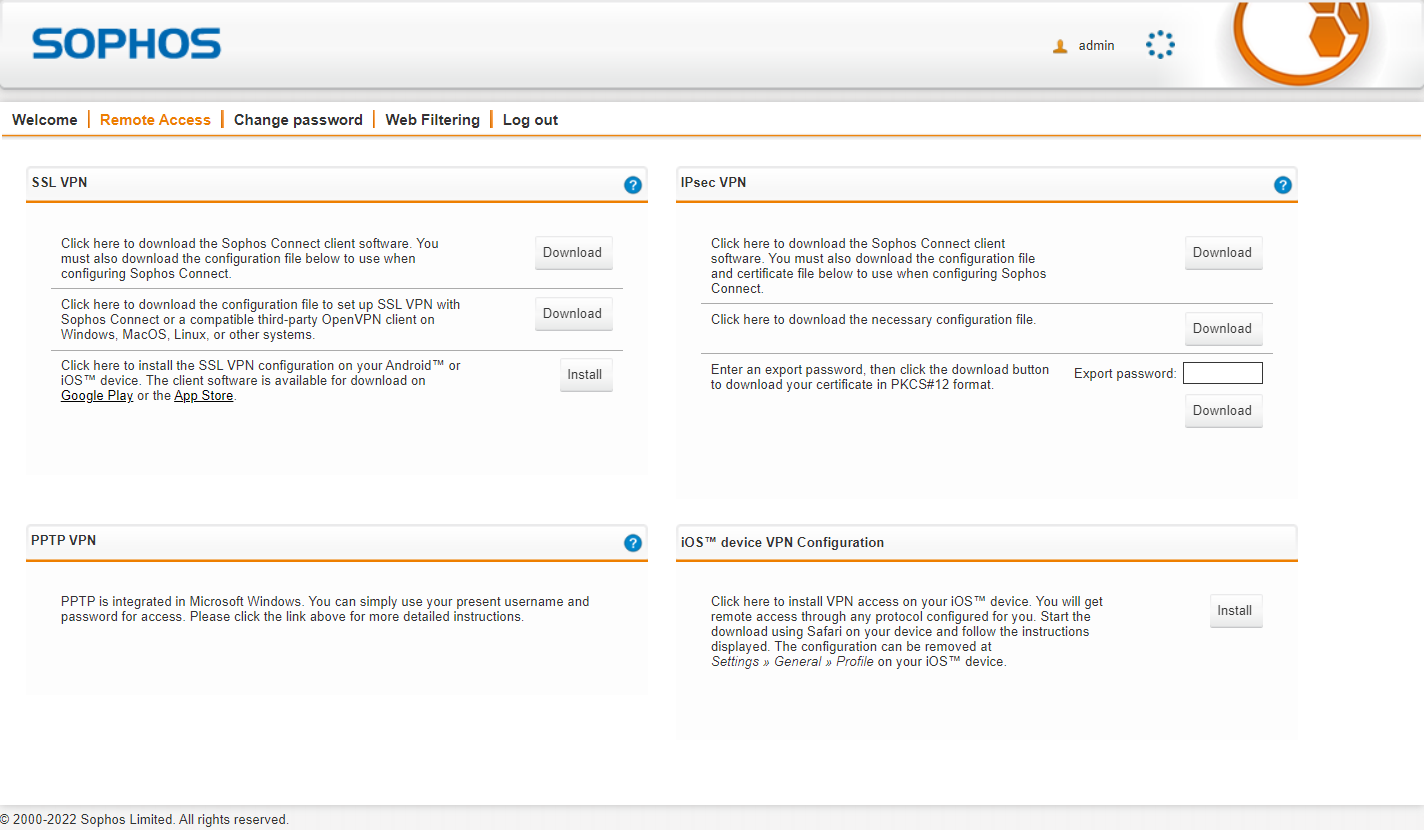
Sophos Connect client should be able to work with any IPSec or SSLVPN configuration you already have set up. Here are some additional links to help understand how it works.
- Sophos UTM: Install and configure Sophos Connect for remote access SSL VPN
- Sophos UTM: Install and configure Sophos Connect for remote access IPsec
Other news
- Maintenance release
- Security release
Remarks
- System will be rebooted
- Configuration will be upgraded
Issues Resolved
- NUTM-12592 [Basesystem] Use Only Secure Ciphers for UTM SSH Server
- NUTM-12784 [Basesystem] Patch BIND vulnerabilities (CVE-2021-25214, CVE-2021-25215, CVE-2021-25219)
- NUTM-13101 [Basesystem] Patch Strongswan Vulnerability (CVE-2021-41991)
- NUTM-13119 [Basesystem] Patch Binutils Vulnerability (CVE-2021-3487)
- NUTM-13144 [Basesystem] Remove SSLVPN client downloader from UTM
- NUTM-13192 [Basesystem] Use Secure Key Exchange Algorithms for SSH
- NUTM-13203 [Basesystem] snmpd high memory for snmpwalk v3
- NUTM-12615 [Configuration Management] Root password hash exposed via confd*.log (CVE-2022-0652)
- NUTM-13013 [Email] Upgrade Exim to v4.95
- NUTM-13200 [Email] OAEP RSA padding mode still uses SHA-1 in S/MIME
- NUTM-13267 [Email] SQLi in the Mail Manager (CVE-2022-0386)
- NUTM-13071 [Logging] IPFIX reporting transferred data on wrong direction
- NUTM-12885 [Network] IPS exceptions issue
- NUTM-12987 [RED] Issue with RED tunnel on BO after disconnecting PPPoE
- NUTM-12936 [Web] Add configuration for overriding warn page to proceed link protocol (Standard Mode SSO)
