Hi,
we try to transfer our UTM-Customer with old AP-Models to Sophos Central Wireless with AP6.
The Customer uses Certificate based Authentication in combination with Windows Server 2019 Network Policy Service and Active Directory integrated Certificate Service.
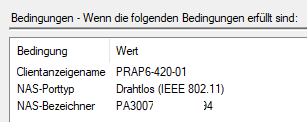
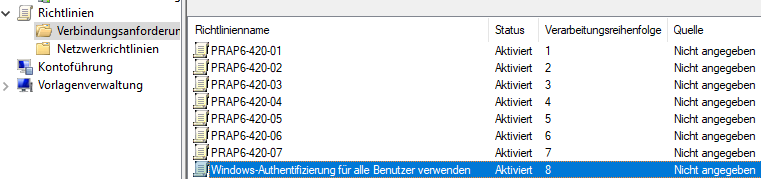
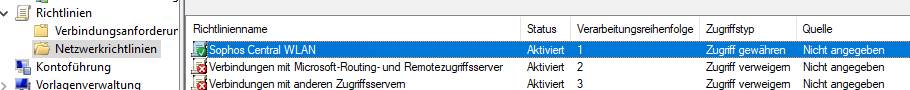
We set up the new Access Point in Addition to the old ones and configured the network requirements (like VLAN and Interfaces) and named the New SSIDs with Test-WifiName. This is working for all WPA2 Personal Networks. For the internal WPA2 Enterprise Network, the Certificate authentication is not working.
I can see the request in the Logfile but no Entry in Event Viewer if the reuest was granted or denied. In the Logfile the existing Request- and Network-Policies are processed for the Connection. But it seems like the Certificate is not transfered to Radius.
The Client settings coming by GPO wich is copied and cahnged to new SSID-Name.
Somebody with the same environment or issue?
Thanks
Added TAGs
[edited by: Erick Jan at 1:22 PM (GMT -7) on 24 Sep 2024]