Disclaimer: This information is provided as-is for the benefit of the Community. Please contact Sophos Professional Services if you require assistance with your specific environment.
Table of Contents
Overview
This Recommended Reads instructs on how to configure authentication of multi-UPN.
UPN
In Microsoft Active Directory, a User Principal Name (UPN) is a username and domain in an email address format. In a UPN, the username is followed by a separator "at sign" (@) followed by the active directory's internet domain.
For more reference, kindly see https://soph.so/2u4ivo
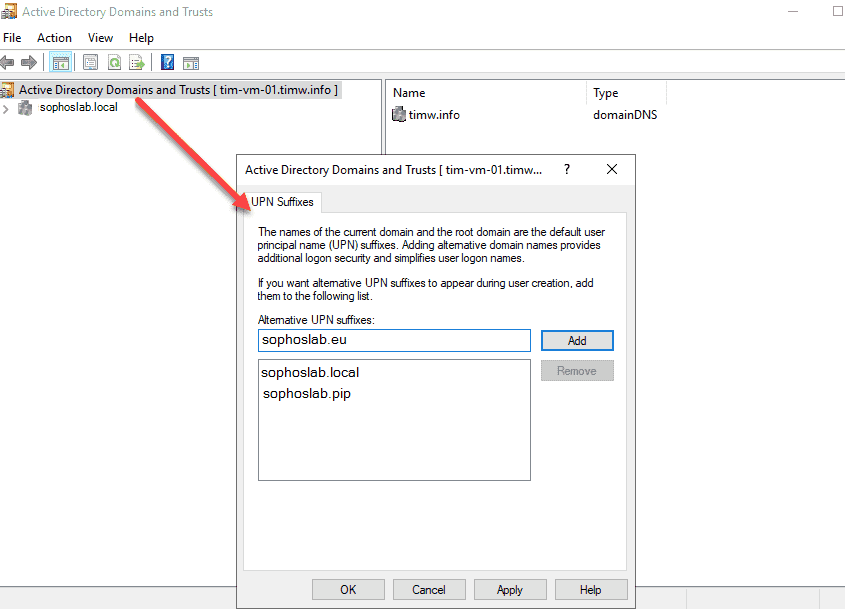
UPN suffixes form part of Active Directory (AD) login names. For example, if your login name is administrator@sophoslab.local, the part of the name to the right of the ampersand is known as the UPN suffix (so, in this case, sophoslab.local).
Editor’s Note: If you need a quick primer on what UPN is from a Microsoft perspective, an article about UPN on the Windows Developer Network elaborates: learn.microsoft.com/.../a-userprincipalname
Advertisement
“This attribute contains the UPN, an Internet-style login name for a user based on the Internet standard RFC 822. The UPN is shorter than the distinguished name and easier to remember. By convention, this will map to the user email name. The value set for this attribute equals the length of the user’s ID and the domain name.”
Configuration
When you configure a new user account in AD, you’re given the option to select a UPN suffix, which, by default, will be the DNS name for your AD domain. There are situations where selecting UPN suffixes can be useful. If your AD domain name is sophoslab.local, it might be more convenient to assign users a UPN suffix of sophoslab.eu. To make additional UPN suffixes available, add them to AD.
Active Directory
Many customers have UPNs, especially when using hybrid solutions for O365, Azure, or organizational needs.
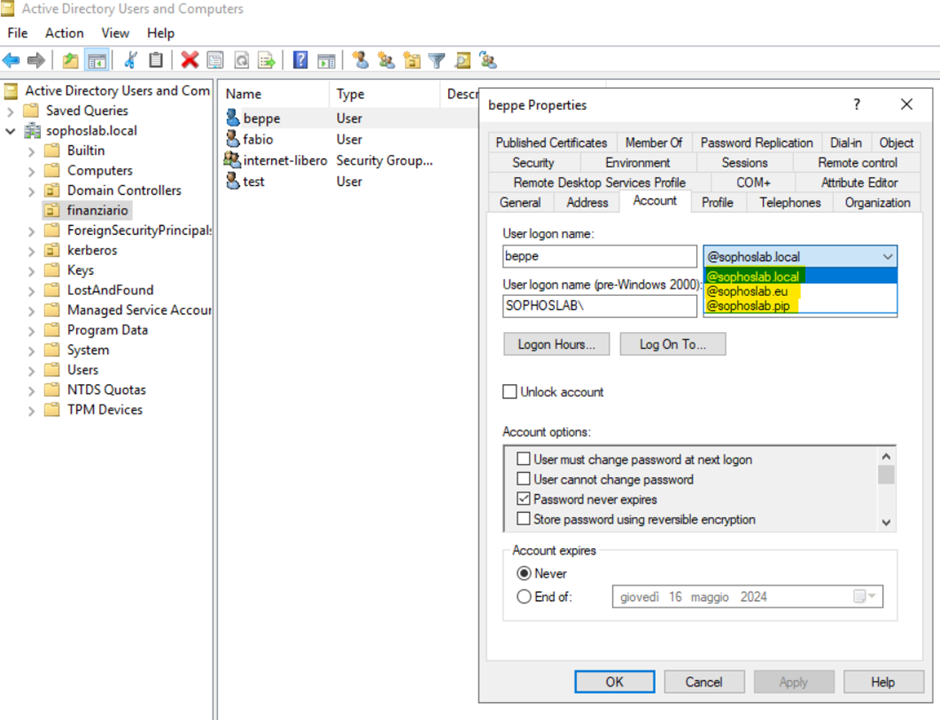
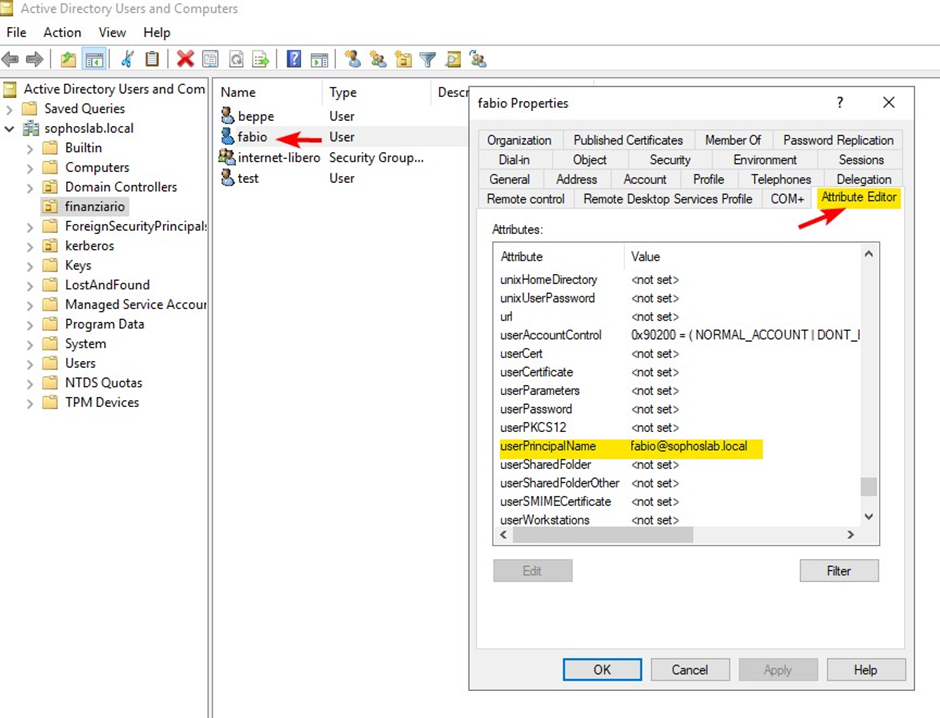
Open Active Directory. In the user properties, select Account and follow the screenshot for more details.
Sophos Firewall
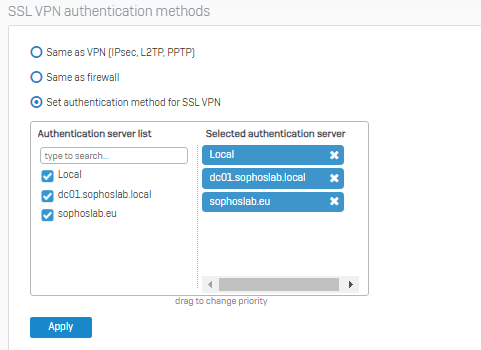
Go to Network>DNS and enter the names and IPs as the same in the Domain Controller.
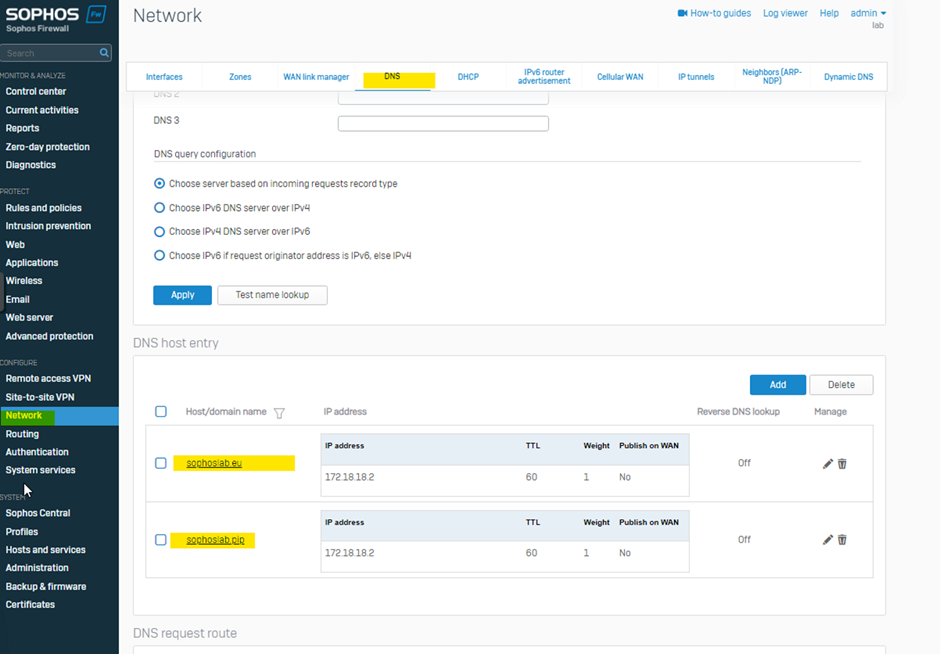
Then go to Authentication>Servers
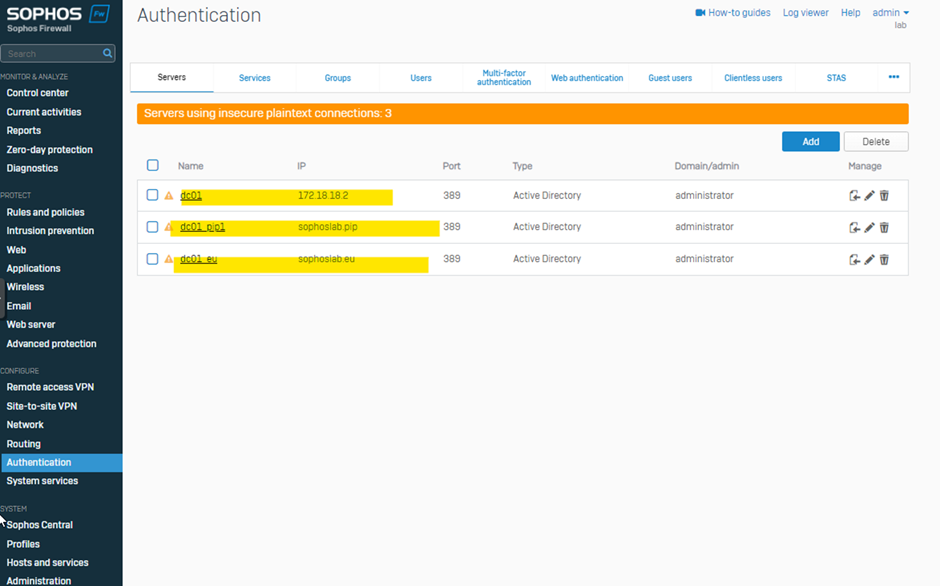
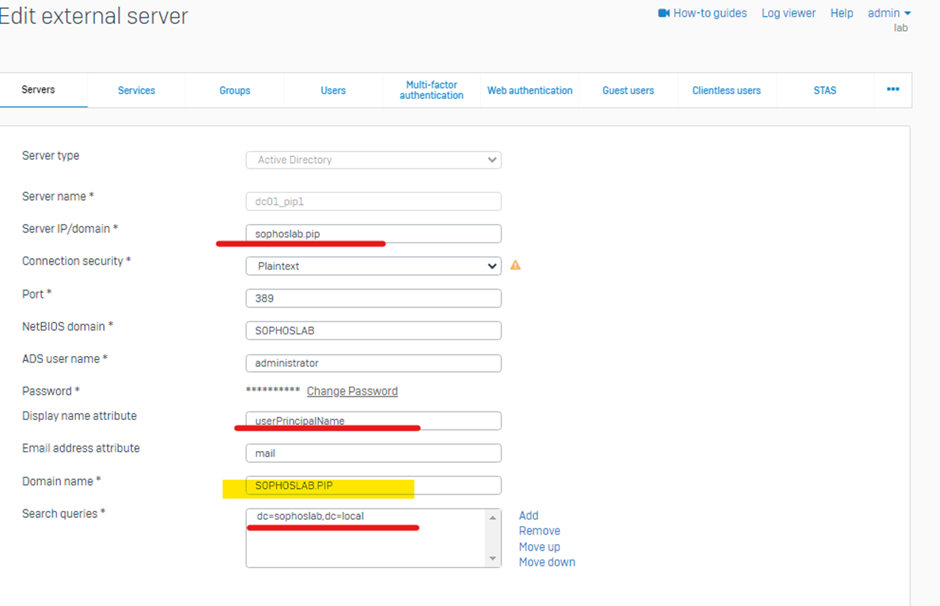
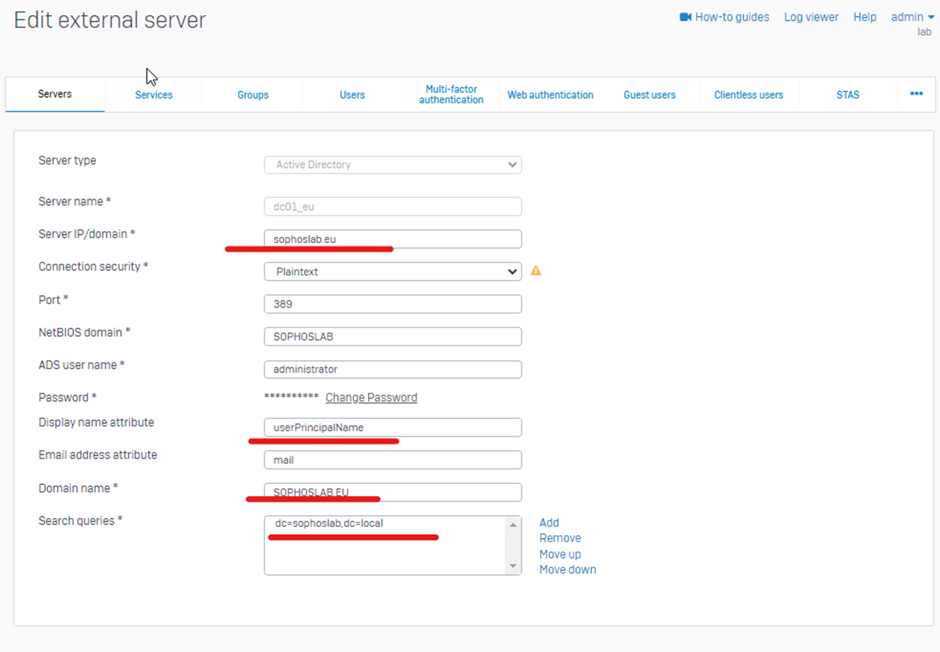
This way, users are authenticated even if they belong to different UPNs but belong to the same Domain Server
Added TAG
[edited by: Erick Jan at 7:25 AM (GMT -7) on 17 Oct 2024]