Disclaimer: This information is provided as-is for the benefit of the Community. Please contact Sophos Professional Services if you require assistance with your specific environment.
Table of Contents
Overview
This Recommended Read reviews recent changes made in SFOS v19 related to SSL VPN IPv4.
What is the change in SFOS v19 related to the SSL VPN IPv4 lease?
SFOS v19 improves supported SSLVPN concurrent tunnels by 4-5x.
As a result, there’s a change in the configuration of SSL VPN IPv4 lease range. SFOS v19 uses IP subnet value; however, earlier versions used IP range and subnet.
Migration will convert the IP range and subnet config from old versions to subnet values in v19.
SSLVPN Global config: 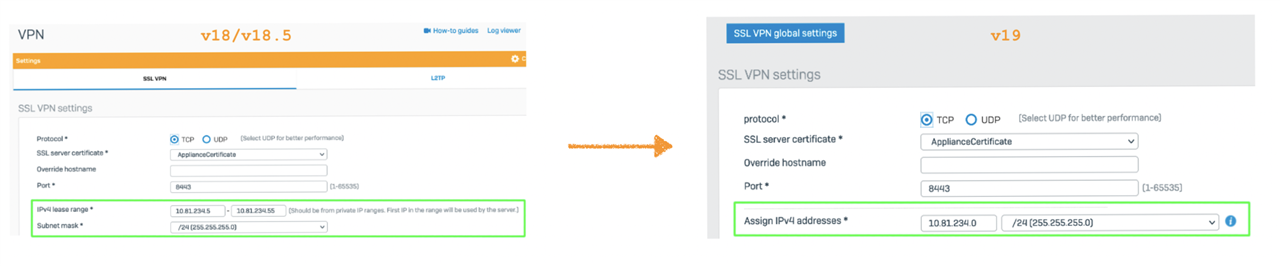
Admin has to update IP lease range from IP address to subnet once after migration to avoid errors like "You must enter a network IP address." on global settings update.
Does the change impact me? What issue may I face?
On upgrading to SFOS v19, some users may notice that SSL VPN is connecting, but resources aren’t accessible over SSLVPN for the following conditions:
- If you’re using SSL VPN before the v19 version and
- If you have allowed access of SSLVPN users using IP host object of limited range (same as SSLVPN global settings) in the firewall rule.
As v19 changes the limited IPv4 lease range to the larger subnet, users with IP addresses outside the limited range will be restricted by Firewall rules to access the resources.
How do we resolve this issue?
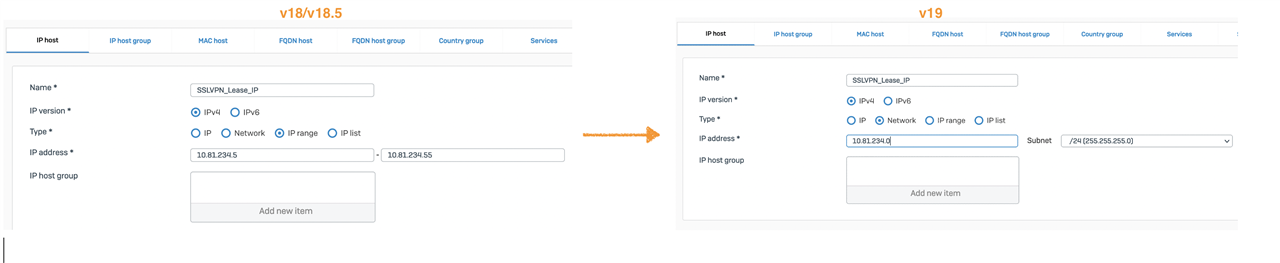
Update the IP host object of limited range to include the new IP range (subnet).
Alternatively, you can use the system host available for SSLVPN IPv4 lease ##ALL_SSLVPN_RW.
More details on Configure IPsec remote access VPN with Sophos Connect client
Updated links to latest
[edited by: Raphael Alganes at 2:23 PM (GMT -8) on 19 Nov 2024]