Important note about SSL VPN compatibility for 20.0 MR1 with EoL SFOS versions and UTM9 OS. Learn more in the release notes.
Important note about SSL VPN compatibility for 20.0 MR1 with EoL SFOS versions and UTM9 OS. Learn more in the release notes.
Disclaimer: This information is provided as-is for the benefit of the Community. Please contact Sophos Professional Services if you require assistance with your specific environment.
This Recommended Read reviews recent changes made in SFOS v19 related to SSL VPN IPv4.
SFOS v19 improves supported SSLVPN concurrent tunnels by 4-5x.
As a result, there’s a change in the configuration of SSL VPN IPv4 lease range. SFOS v19 uses IP subnet value; however, earlier versions used IP range and subnet.
Migration will convert the IP range and subnet config from old versions to subnet values in v19.
SSLVPN Global config: 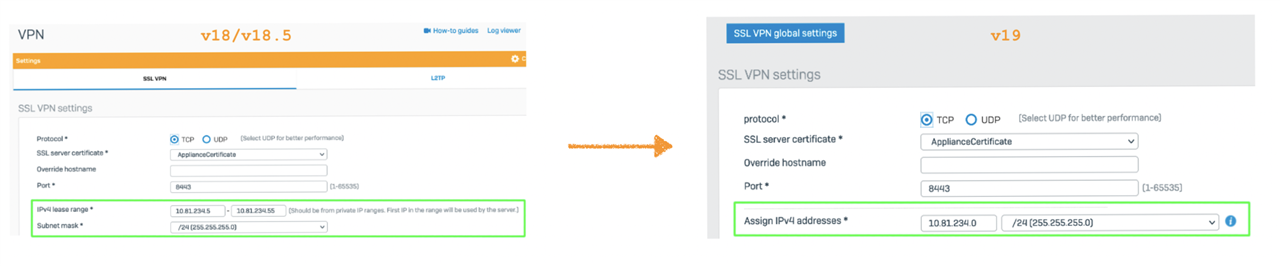
Admin has to update IP lease range from IP address to subnet once after migration to avoid errors like "You must enter a network IP address." on global settings update.
On upgrading to SFOS v19, some users may notice that SSL VPN is connecting, but resources aren’t accessible over SSLVPN for the following conditions:
As v19 changes the limited IPv4 lease range to the larger subnet, users with IP addresses outside the limited range will be restricted by Firewall rules to access the resources.
Update the IP host object of limited range to include the new IP range (subnet).
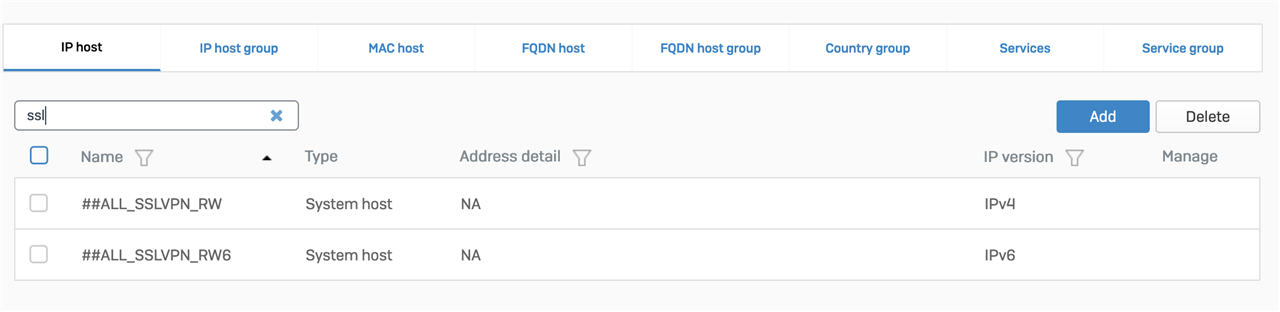
Alternatively, you can use the system host available for SSLVPN IPv4 lease ##ALL_SSLVPN_RW.
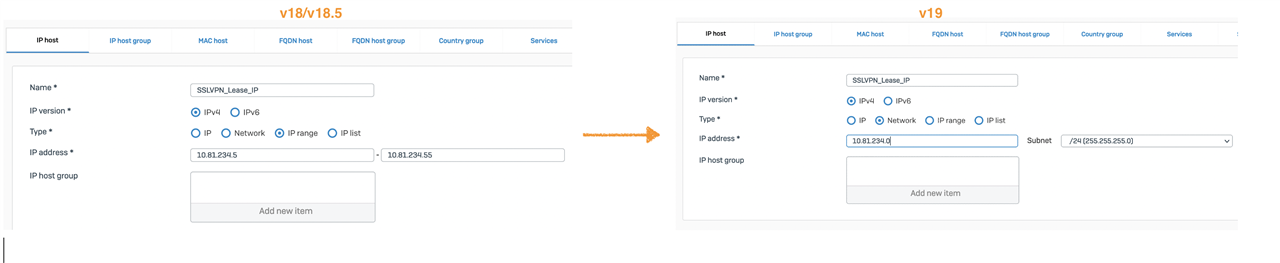
More details on Configure IPsec remote access VPN with Sophos Connect client
how can changing DHCP scope from range to mask only improve SSL VPN performance??
Migration will convert the IP range and subnet config from old versions to subnet value in v19.
you write, it will migrate based range AND subnet
what will happen to a V18 DHCP Server with lets say 192.168.1.5-192.168.1.10 Mask 255.255.255.224 (/27)
in v19
it could be 192.168.1.0/28
or 192.168.1.0/27
Why is this not mentioned in Release notes?? https://docs.sophos.com/releasenotes/index.html?productGroupID=nsg&productID=xg&versionID=19.0
It's not mentioned that Range has been removed. There is only written that something has been added.
Why is it that /24 is the smallest network that this supports now? I actually need to insure that my clients do not exceed the /27 on assignment as they are accessing a network that restricts us to that /27.
Just to provide more context around why we brought this changes in, from v19 to improve scale and performance we have made SSLVPN multi-instance up to 8 depends upon no of CPUs. With this changes each instance will create “tun” interface and it will require individual subnet to handle traffic distribution and routing internally. To avoid the user input complexity we do slicing of subnet internally from the configured IP value.
In case if you have 192.168.0.0/27 configured in v18.5 and migrates to 8 instance config in v19, it won’t have much usable hosts as below:
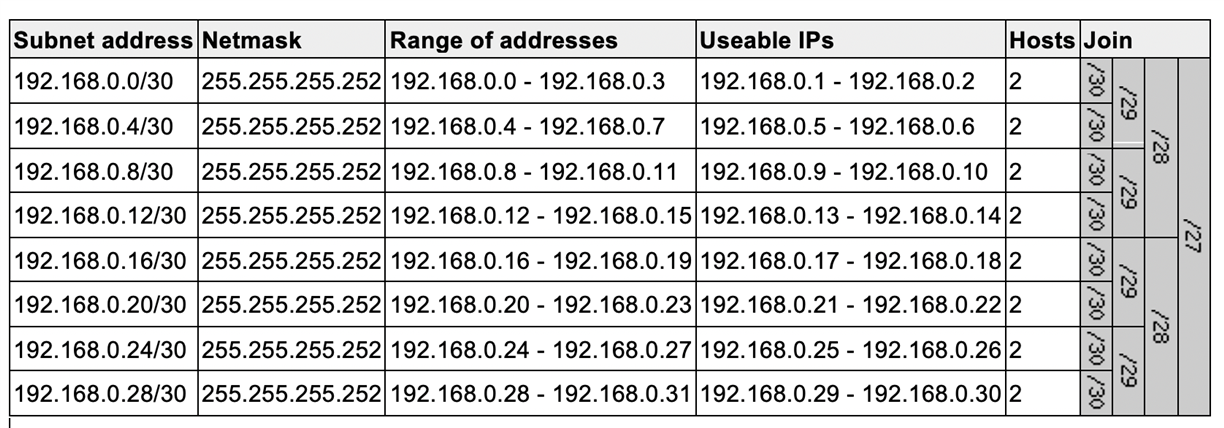
Hope this helps.
so in this scenario you'll lose up to 50% of the available IPs, and when you count them in the DHCP leases on XG, you'll find yourself with 16 IPs leased while you configured a range with 32 IPs.
Sound's like a nightmare to debug.
where is that doc change you were mentioning above? I could not find it in the interactive release notes today.
We are talking about "smallest" Network. If you are concern about the range, you can pump this value up to higher values without no problem. And DHCP works not like that in SSLVPN. Essentially SSLVPN works with Pools, you can see here. Not with DHCP Lease Ranges. See Documentation of OpenVPN.
__________________________________________________________________________________________________________________
After updating to version 19, VPN users are not able to resolve internal host names. Do we need to make any configuration changes?
I know work around is updating DNS server under Global VPN setting to our Onsite DNS server but before upgrading to version 19, DNS server for vpn users was IP of SSL VPN Server and it stopped resolving hostnames after update.
can you check if SSLVPN server IP is used on tun interface or not in CLI by running "ifconfig"? and which IP was used for SSLVPN server in your setup??
Prior to Version 19, first IP of the Range was used as IP of VPN Server, so it was 192.168.5.5. And no, after update, there is no server IP used on tun Interface.
Is there a way in GUI, where we can setup SSLVPN Server IP?
No that option is not available on UI.
But as mentioned above we have moved to subnet from IP range, first IP of the subnet will be assigned as SSLVPN server IP. Now we have multiple instances and hence I will not suggest to use it as DNS IP.
So I just ran into this issue where I had a SSLVPN range defined as the same range I had in the SSLVPN settings and had issue with user not being able to access LAN resournces, all due to the change...I have adjust my VPN rule. But the question I have to ask is it is stated here that the 'first IP of the subnet will be assigned as SSLVPN server IP.' I am assuming this to mean the SSLVPN DHCP server. If so, on my connection I am seeing it as the LAST IP (.254). Am I missing something?
Hi Lonnie,
In case of SSLVPN there is no separate DHCP server, openVPN manages the IP lease (dhcp) functionality. When we say "first iP of the subnet will be assign to SSLVPN server" it is used to bind on "tun" interface.
From v19 we have introduced multiple instance and hence each instance will create separate "tun" interface and sliced subnet from global config.
e.g. For two SSLVPN instance setup, subnet will be splitting into 2 and each one will be used for individual server.

You can look for more details in the conf file.
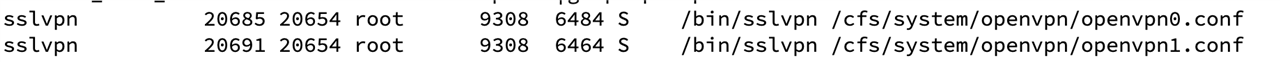
Hence in this case First IP of both subnet will be used on "tun" interface respectively.
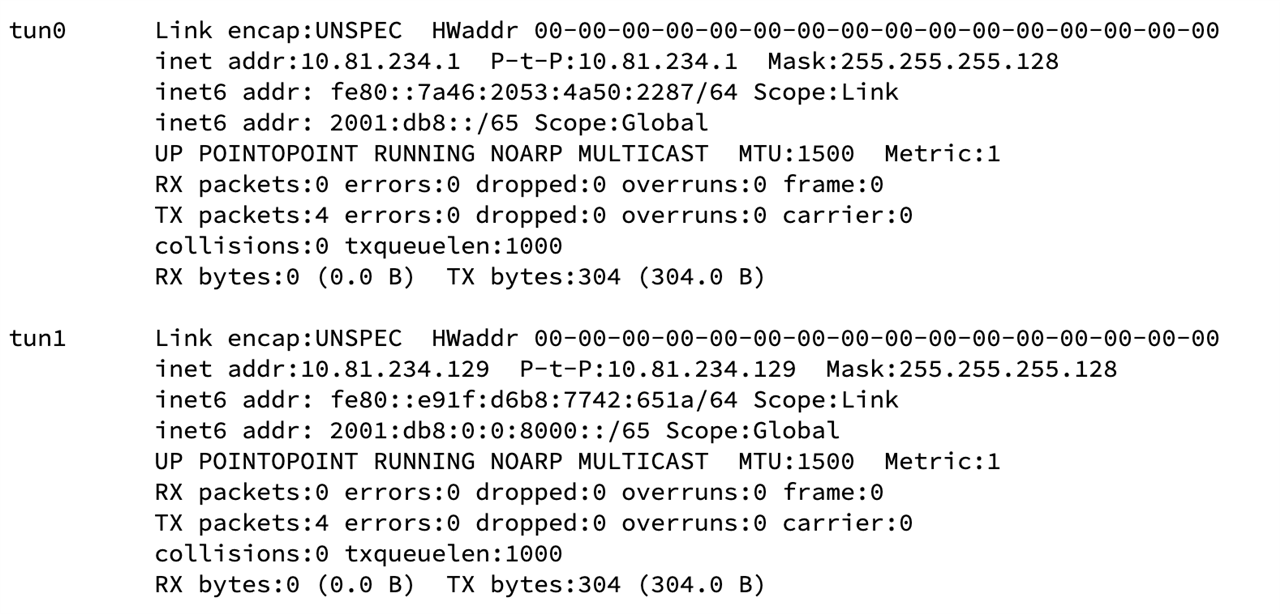
Hope this clarifies your query.
Hi Alok,
I appreciate and understand (somewhat) your explanation. My apologies for thinking 'First IP of the subnet' meant DHCP server. So I understand that now. I have change the VPN FW rules on my all XGs to use ##ALL_SSLVPN_RW instead of my original IP range which mimiced the v18 SSLVPN assignment range. That way when I upgrade the other XGs, there should be no issue. All good at this point. I am assuming that the ##ALL_SSLVPN_RW range will not let it assign the DHCP address as an endpoint IP.
On last question. Are we going to see this same change in L2TP settings in the future, as it was set up similar to SSLVPN with explicit from & to IP range. In v19 it remains as it did in v18.
Very much appreciated.
Lonnie
This change in SSLVPN had to introduce as we were not able to scale beyond the certain limit with single server architecture and hence we moved to a multi-instance approach to scale up SSLVPN capacity in terms of concurrent tunnel support as well throughput.
We are not planning to make any enhancement to L2TP/PPTP services at the moment so that will stay as is.
Hi Alok, so what's the Solution here for DNS?
When I set DNS to default gateway of SSL VPN, it doesn't resolve hostname as it was prior to upgrade?
We just have one Instance, so setting default gateway of SSL VPN shouldn't be a problem, but it doesn't work.
Hi Gurtej,
when you say default gateway are you setting "tun0" interface IP as DNS server?
e.g. 192.168.5.1 if its (192.168.5.x/24 subnet)
-Alok
Hi Alok,
Yes, you are right. We are setting "tun0" interface IP as DNS Server. e.g. 192.168.5.1 if its (192.168.5.x/24 subnet)
I had this exact situation - where after the V19 upgrade, there were sporadic issues where Sophos Connect (using SSL VPN) would connect but not route traffic properly. The root cause was definitely due to the client endpoint range being converted IMPROPERLY from a range to a CIDR.
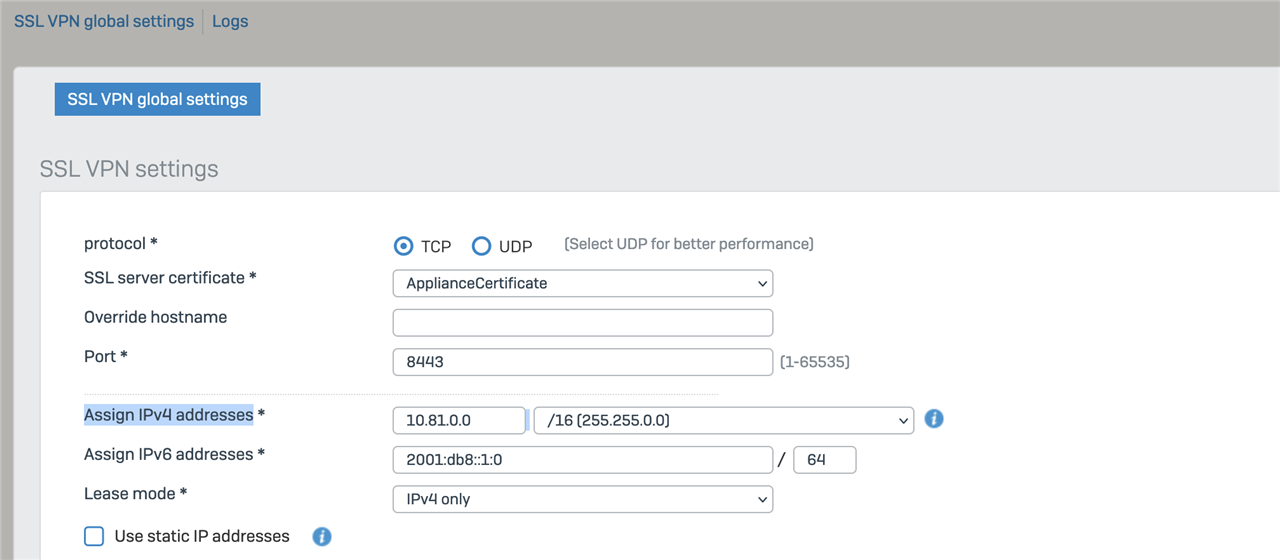
Definitely ensure that post V19 upgrade you change the SSL VPN ip address pool from a range to a network... CONFIGURE > Remote access VPN, then click the SSL VPN tab, then click the "SSL VPN global settings" link in the upper left. In the "Assign IPv4 addresses" section, be sure the address space is showing in proper CIDR network notation. For me post upgrade, it showed 10.81.234.20/24. I had to change it to 10.81.234.0/24. After which, users needed to manually disconnect/reconnect, and then the problem was completely resolved. Also be sure any firewall rules you have reference the whole network and not a range - that was also a problem for me to correct.
I think this is something that could have been handled during the upgrade automatically with a user prompt or something.
Hi Tony,
I had similar issue but mine was resolved by changing the SSLVPN range on the VPN rule.
But I am curious about your statement about having to change the last octet from .20 to .0
Both addresses in a /24 subnet will result in a .1 thru .254 address range with a network address of .0 and broadcast of .255
So I don't see how changing that resolved your issue. Did you also change the SSLVPN range on your VPN rule at the same time and that was possibly the answer?
This suggestion worked for me. In our case, our Assign IPv4 addresses were something.something.something.5 /24 and when I changed it to something.something.something.0 /24 I was able to get past that incessant "You must enter a network IP address" error.
Thank you!
This really should be fixed so that the error message is more meaningful.
But in my case the "System Host" shows Address Details as NA and it doesn't allow to edit it too. So is there another way of editing these records?
Hi Mayuresh, System hosts are non-editable. But when you will update the IP lease range on SSLVPN global configuration page, it will be automatically updated to accommodate same.
It didn't allow us to save any changes to the IP or the lease. Nevermind, I got up with support and the agent enabled remote support and changed something from the background to resolve this.
When you update IP lease range it will automatically update system host value internally, no need to manually update for system hosts.
Thanks for the update.
I agree and understand, however, I showcased this to support team too that if I try changing the value for "Assign IPv4 address" and then click save, it used to throw the error "You must enter a network IP address". Only once the support team made changes from the backend were we able to save the changes.