Disclaimer: This information is provided as-is for the benefit of the Community. Please contact Sophos Professional Services if you require assistance with your specific environment.
This Recommended Read goes over the most common SSL VPN issues and how to solve them.
Table of Contents
- Verify the user’s portal accessibility
- Verify the Port used for SSL VPN
- Confirm you don’t have a DNAT rule with service ANY
- Confirm the default certificate information is filled in and ensure there are NO special characters in the certificate name or any other fields.
- If your Firewall is behind another NAT device (Router) (Sophos Firewall doesn’t have a Public IP).
- Confirm the time and time zone in the Sophos Firewall is correct
- Common log errors:
- The tunnel is connected but users are unable to access remote resources.
- Troubleshooting 0 byte SSL VPN file
- Additional links and info:
-
Verify the user’s portal accessibility
Make sure that the SSL VPN service is selected for the WAN interface under Administration > Device Access.
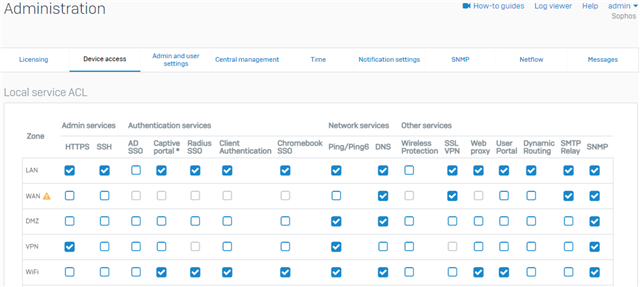
-
Verify the Port used for SSL VPN
Configure >> VPN >> Show VPN settings >> SSL VPN
The default port, 8443 is used for SSL VPN connections
For Version 19.
Configure>>Remote Access VPN>>SSL>>SSL VPN Global Settings
Configure>>Site-to-Site VPN>>SSL>>SSL VPN Global Settings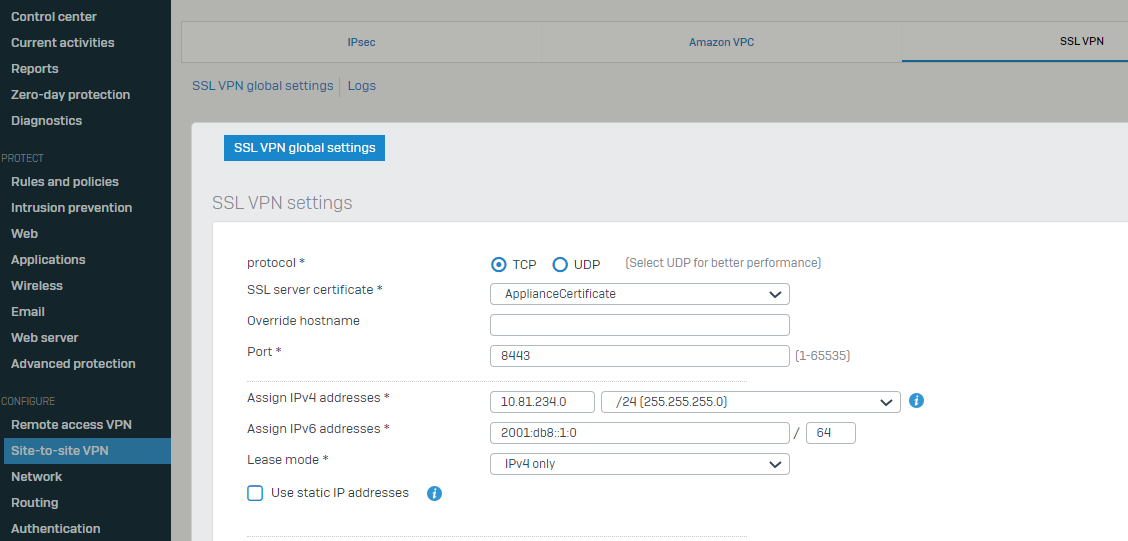
Note: The configured port must be open on inbound connections to the firewall and outbound from the client’s network.
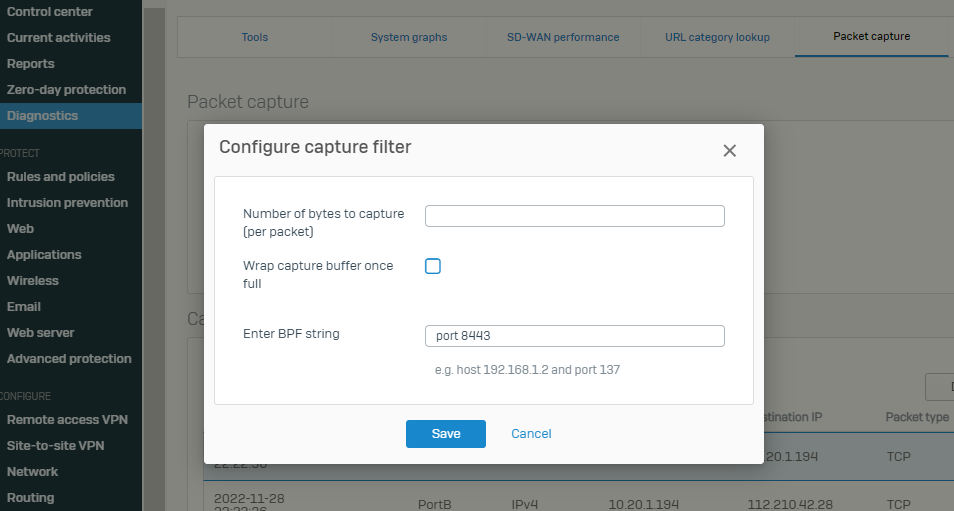
To confirm if the Sophos Firewall is receiving traffic on port 8443. Use the Packet Capture on the GUI, please go to Monitor & Analyze >> Diagnostics >> Packet Capture >> Configure
Alternatively, you can also use the CLI. Log in to the command-line interface (CLI) and select 4: Device Console. Run the command bel...ow and ask the user to try to connect.
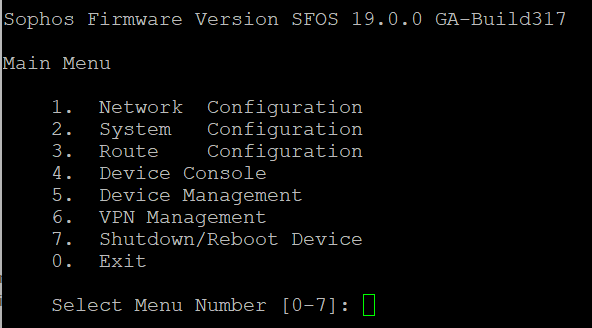
Console> tcpdump “port 8443”
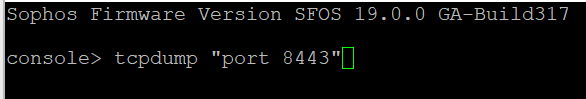
If you don't see traffic arriving at the port, and your Sophos Firewall is the border router, your ISP is blocking this port.
If your Sophos Firewall doesn't have a Public IP on the WAN port, check that your ISP has the port open and that your upstream router has a DNAT rule on the selected SSL VPN to send to the Sophos Firewall, if you don't see traffic arriving, either your ISP is blocking the port or your Upstream device
Note: It is better to change the SSL VPN port to use 443 as this port is usually open in most networks, if you decide to do this, keep in mind that the User Portal and any other service shouldn’t be using the same port unless you have an additional WAN interface.
-
Confirm you don’t have a DNAT rule with service ANY
If you have a DNAT rule with service ANY or with the same port used for SSL VPN, the XG won’t intercept the SSL Connection and instead would pass it down to the server selected in the DNAT/Business rule. This will cause users not to be able to connect to the SSL VPN.
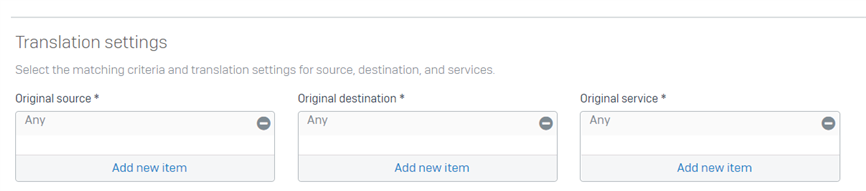
If you have a rule with Service as ANY change this to use the correct port/service.
-
Confirm the default certificate information is filled in and ensure there are NO special characters in the certificate name or any other fields.
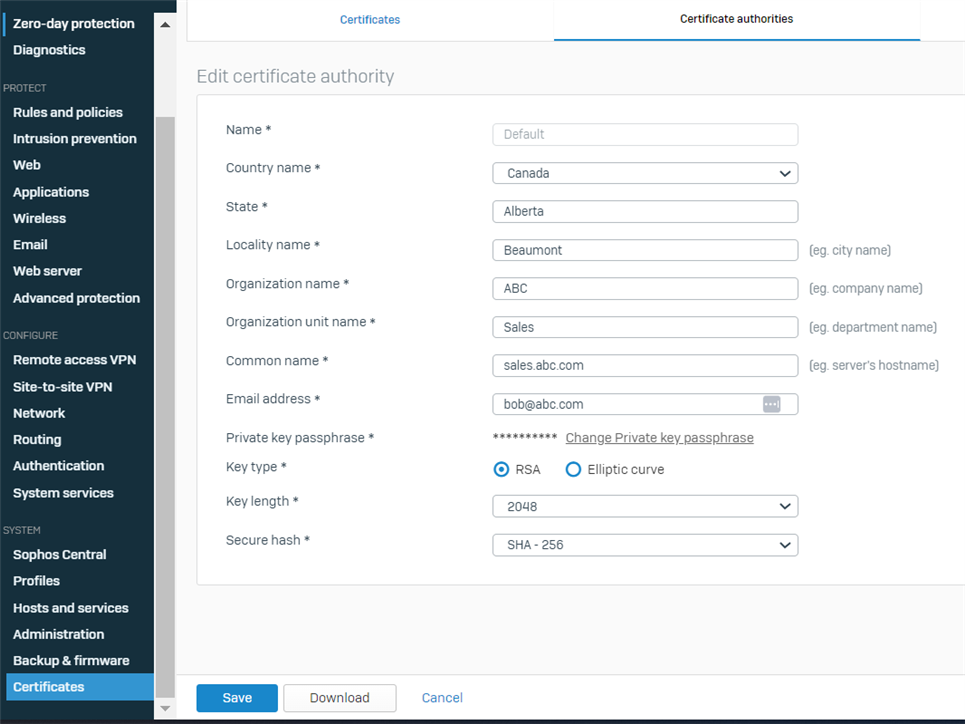
Once you have done the steps above, ask the user to re-download the configuration from the user portal.
-
If your Firewall is behind another NAT device (Router) (Sophos Firewall doesn’t have a Public IP).
Make sure that under Configure >> VPN >> Show VPN settings >> SSL VPN >> Override hostname, you add the Public IP of the upstream device or DynDNS FQDN.
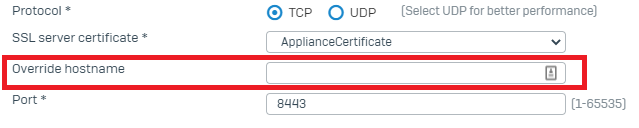
For Version 19
Configure>>Remote Access VPN>>SSL>>SSL VPN Global Settings
Configure>>Site-to-Site VPN>>SSL>>SSL VPN Global Settings...
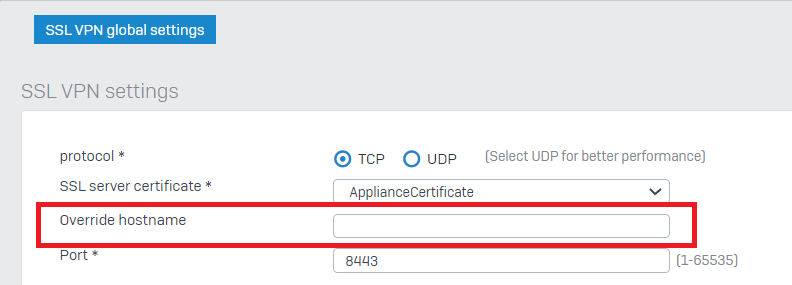
Note: If you have more than a WAN interface in your XG, you specify the Public IP of the WAN interface that you want the SSL VPN to connect to or a publicly resolvable hostname.
If the Sophos Firewall hostname can't be resolved by internet users, (resolvable on the Internet), you need to specify a public IP under "Override hostname"
The Sophos Firewall hostname is configured via System > Administration > Admin and user settings.
-
Confirm the time and time zone in the Sophos Firewall is correct
Please go to System >> Administration >> Time
Confirm that the Time Zone is correct if you set the time manually double-check there is no time skew and not off for more than 2 minutes. In any case, we recommend the use of a Pre-defined NTP Server.
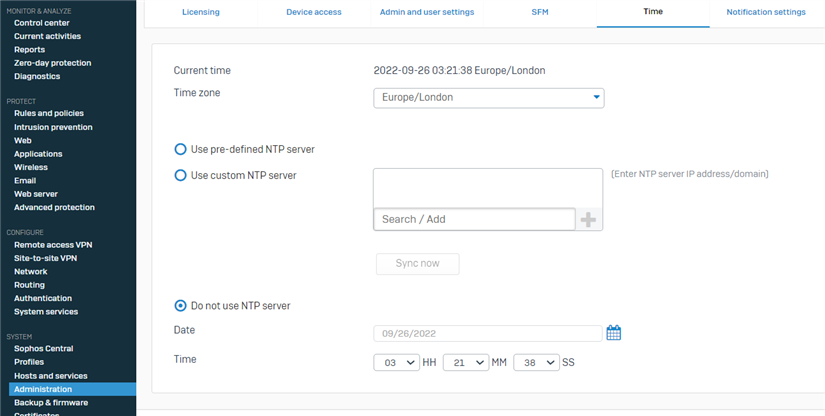
Note: After a change in the time, a restart is necessary for it to take effect.
-
Common log errors:
VERIFY ERROR: depth=1, error=certificate is not yet valid
Please make sure to update the Default Certificate of the firewall, and ensure there are no special characters in the certificate name or any other fields. Once you update the default certificate, delete the user certificate from the firewall, and download the configuration from the user portal, this process will re-generate the user certificate.
VERIFY ERROR: depth=0 error=format error in certificate’s not
Please make sure to update the Default Certificate of the firewall and ensure there are no special characters in the certificate name or any other fields. Once you update the default certificate, delete the user certificate from the firewall, and download the configuration from the user portal, this process will re-generate the user certificate.
The tunnel is connected but users are unable to access remote resources.
Make sure you have configured the correct VPN to LAN/DMZ Firewall rules
Confirm the range of IPs for the SSL VPN Global Settings matches the Source Network in the Firewall Rule for VPN to internal resources.
Make sure that the subnet where the user is connecting doesn’t overlap with a subnet that they’re trying to access behind the SSL VPN.
If SSL VPN users can't access internal resources via hostname, please ensure the proper DNS server is configured in SSL VPN Global Settings.
TIP: To overcome this potential issue, avoid using the following three networks in your Sophos Firewall: 192.168.0.0/24, 192.168.1.0/24, and 192.168.2.0/24 (which are the subnets used by 99% of home users by default).
Traffic generated from the SSL VPN is assigned to the Tun0 interface, to confirm if traffic within the SSL VPN is arriving at the Sophos Firewall, try running the following command from the Advanced Shell of the Sophos Firewall or the GUI using the Packet Capture.
# tcpdump -eni tun0 host x.x.x.x (x.x.x.x = IP assigned to the SSL VPN client)
Note: When doing initial testing please disable the computer or device destination Firewall. (E.g Windows Firewall)
Check out this Recommended Read on how to NAT the traffic coming from IPsec. It applies the same principle to SSL VPN.
Troubleshooting 0 byte SSL VPN file
If you are running any version below 17.5 MR12 and 18.0 MR1, please upgrade. If the issue persists after upgrading, please look at this Recommended Read.
Sophos Firewall: Troubleshooting 0 Byte SSL VPN File
-
Additional links and info:
KB Articles
Sophos Firewall: How to troubleshoot SSL VPN remote access connectivity and data transfer issues
https://support.sophos.com/support/s/article/KB-000036884?language=en_US
How to configure SSL VPN Remote access
Sophos Firewall: Implementing Sophos Security Heartbeat with SSL VPN remote access
https://support.sophos.com/support/s/article/KB-000038254?language=en_US
Windows User Permissions Required for SSL VPN Client
https://support.sophos.com/support/s/article/KB-000034263?language=en_US
Sophos Firewall: How to configure SSL VPN (remote access) with LDAP authentication
https://support.sophos.com/support/s/article/KB-000038367?language=en_US
Sophos Firewall: How to assign a specific IP to an end user connected via SSL VPN connection
https://support.sophos.com/support/s/article/KB-000038046?language=en_US
Sophos Firewall: How to configure access for SSL VPN remote users over an IPsec VPN
https://support.sophos.com/support/s/article/KB-000038320?language=en_US
Sophos Firewall: Simultaneous Remote Access SSL VPN Connections
https://support.sophos.com/support/s/article/KB-000038204?language=en_US
Revamped - Updated Links to latest, Grammar
[edited by: Raphael Alganes at 11:19 AM (GMT -8) on 20 Nov 2024]
