Disclaimer: This information is provided as-is for the benefit of the Community. Please contact Sophos Professional Services if you require assistance with your specific environment.
Table of Contents
This applies to the following Sophos products and versions
Sophos Firewall v19 and above
Overview
This Recommended Read assumes you already have a working IPsec tunnel.
Note: This RR might also help you troubleshoot connectivity issues when the IPSec tunnel is UP, but there are no replies to Pings or other types of connectivity.
When testing connectivity or due to some specific policies, we want traffic coming from the other end of the tunnel to be seen by our LAN devices as if the connection is coming from the Sophos Firewall itself.
By default, traffic coming from the IPsec to the devices on the LAN will be seen by them with the original address used on the tunnel, which in some situations will cause some devices using Local Firewalls not to reply to this traffic as Local Firewall by security won't reply to IPs, not in the same Broadcast domain (Network range). Or, in some scenarios, for security reasons, you don't want your LAN to see traffic from a different subnet.
In these cases, it’s an excellent idea to MASQUERADE the incoming IPsec traffic to the LAN as if it were coming from the Sophos Firewall local interface.
What to do
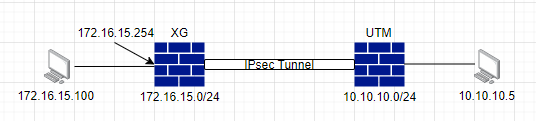
In our scenario, we’re receiving pings from 10.10.10.0/24 subnet, coming from the IPSec tunnel, destined for a computer on the LAN zone with IP 172.16.15.100
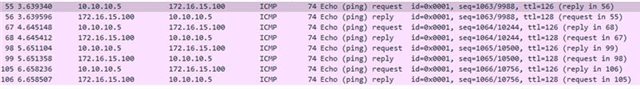
Our computer is responding because we have disabled the local Firewall of the computer, but maybe we don't want to do that, or it isn’t an option to turn off the Local Firewall.
What we can do at the Sophos Firewall level to resolve this is to MASQUERADE this traffic so the end device sees it as if the traffic was coming from the Sophos Firewall Interface where the device is connected to.
Our Sophos Firewall has an IP of 172.16.15.254 and the Computer 172.16.15.100, so we’ll configure the Sophos Firewall so that the traffic arriving at the Computer is MASQUERADE as 172.16.15.254.
How-To
1. Go to Rules and policies >> NAT Rules Add NAT rule >> Enter a name >> and configure the NAT rule as follows:
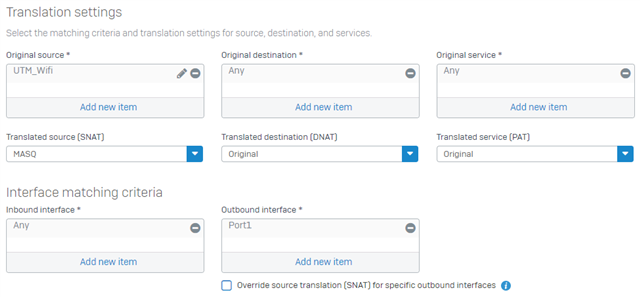
Translation settings
Original Source = Network configured as Remote Subnets in the IPsec configuration
Original Destination = ANY
Original Service = ANY
Translated source (SNAT) = MASQ
Translated destination (DNAT) = Original
Translated service (PAT) = Original
Interface matching criteria
Inbound interface = ANY
Outbound interface = Port1
Related Information:
Sophos Firewall: How to set a Site-to-Site IPsec VPN connection using a preshared key
Monitor traffic using Packet Capture Utility in the Sophos Firewall GUI
Regards,
Edited Title
[edited by: emmosophos at 10:38 PM (GMT -8) on 19 Dec 2024]
