have two local networks on Sophos firewall, one is 192.168.0.0/24 which is on LAN_P5(physical interface) and other is 10.35.11.0/24 which is on port 5.11(VLAN).
I made an IPSec tunnel with a Mikrotik router, which has a LAN network 192.168.1.0/24.
All policies are the same for both sophos LANs and also there are policies for both LANs on Mikrotik.
The problem:
From Mikrotik I can ping any host on network 10.35.11.0/24, but on network 192.168.0.0/24 I can only ping Sophos address 192.168.0.1, all other addresses are not responding.
If I ping from the Sophos side using ping -a 192.168.0.1 192.168.0.0/24 (any host on this network) the ping is answered.
Here are packet captures from Sophos to ping examples to both Sophos network hosts from Mikrotik.
Ping from 192.168.1.1 (Mikrotik router on other end of ipsec tunnel) to 10.35.11.2

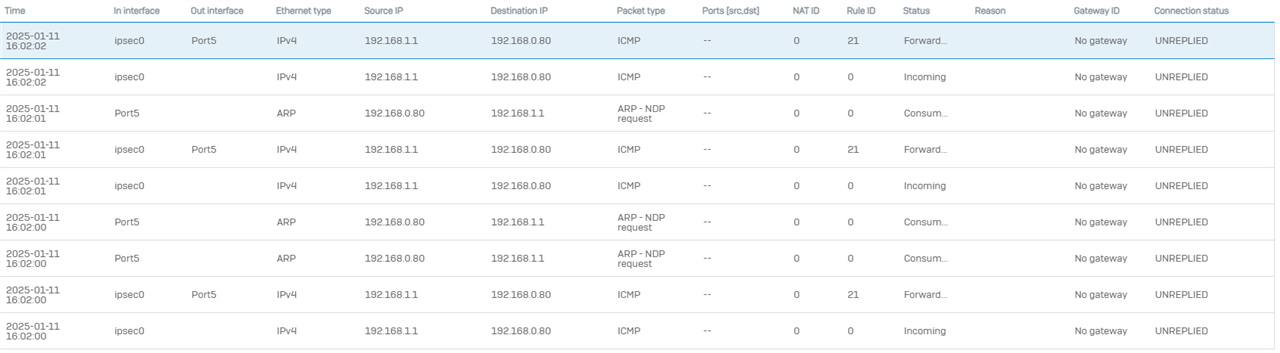
Ping from 192.168.1.1 (Mikrotik router on other end of ipsec tunnel) to 192.168.0.80
Route precedence is set to vpn static sdwan
Tried also setting IPSec route - system ipsec_route add net 192.168.0.0/255.255.255.0 tunnelname IPSec_tunnel
I have no more ideas what to test.
Added TAGs
[edited by: Erick Jan at 7:50 AM (GMT -8) on 15 Jan 2025]


