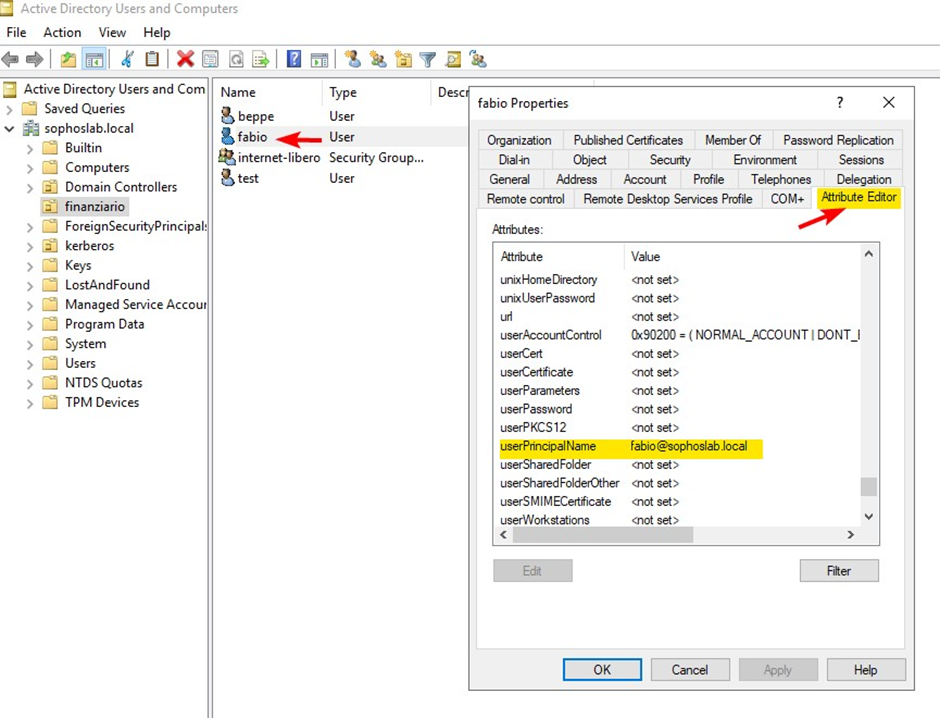
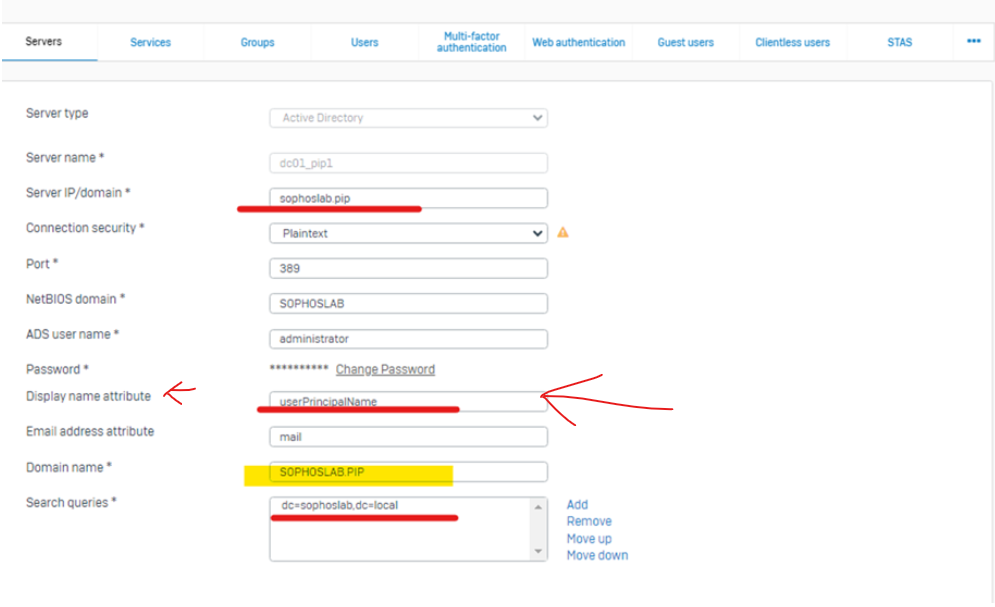
I have learned how to support UPN or multi UPN configuration with local Host / DNS registrations on the Firewall directly. I have configured that successfully on the firewall. Sophos Firewall: Authentication Multi UPN configuration
But as written in my comments in that Recommended Read, we're having difficulties, as we currently have a SamAccountName (SAM) in our AD like
username (which is username\domain)
Now with migration to O365 we need UPN authentication
name.surname@domain.com
This does not work for firewall authentication. It only works when the SAM is identical the UPN-Part before the @
So we must have: SAM=name.surname and UPN=name.surname@domain.com only then it works.
We need the original SAM so we don't mess up with other internal system logins but we need the additional UPN for O365.
We don't want the users to use different logins for Firewall and Windows / O365.
The current situation is a showstopper. GiuseppeI as author of the article, is it possible that can you help here?
Edited TAGs
[edited by: Erick Jan at 3:32 AM (GMT -8) on 9 Dec 2024]