Hi,
I moved to Version 21.0 GA (Home Edition) recently.
I noticed that in control panel, no events in the log or counters are logged that X-Ops is doing anything: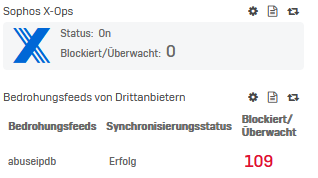
A configured third party threat list (abuseipdb.com) is working properly and blocks and reports in the logs.
X-Ops (formerly ATP) was enabled the whole time, even before upgrading from 20.0 MR2 to 21.0 GA, and my Home License includes it. Signatures are also updated regularily.
Edited TAGs
[edited by: Erick Jan at 12:08 AM (GMT -7) on 24 Oct 2024]

