I have TLS inspection setup on my main network running through a Sophos XG (20.0.2 MR-2) and am trying to setup Google Passkeys for G-Mail.
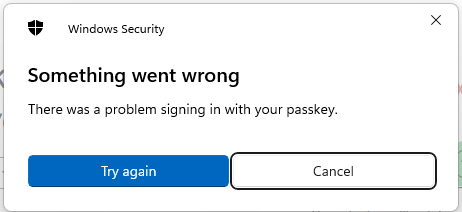
The passkeys were setup using a different network connection, and they do work on another network. If I go through the G-Mail logon process it gets to the point of displaying the QR code which I scan on a mobile phone, at which point the browser give a "Something went wrong" error and G-Mail asks if I want to try again.
If I turn TLS inspection off the logon process works using passkeys.
To get Passkey authentication working I suspect that I need to exclude one of the Google URLs from TLS inspection, but don't know which one. I don't want to exclude all Google services, including Gmail itself, from TLS - just the Passkey authentication process.
Has anyone got this working with TLS enabled?
Added TAGs
[edited by: Raphael Alganes at 9:52 AM (GMT -7) on 16 Oct 2024]