Hi guys
I can't see the wood for the trees -- so please forgive me this (probably stupid) question:
When using PSK for IPsec without certificates, everything is working properly. It asks for password (or I save my password) click Connect and it works.
However, when using Certificates, there is a timeout and it does not ask for password at all when connecting.
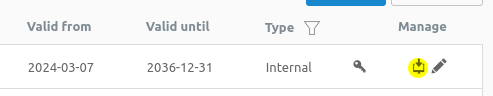
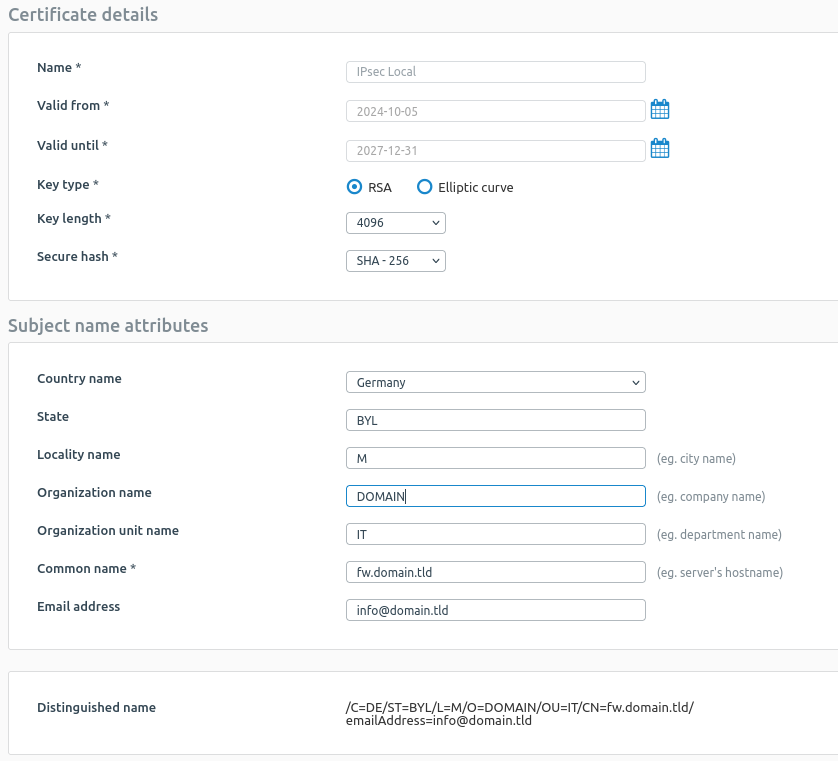
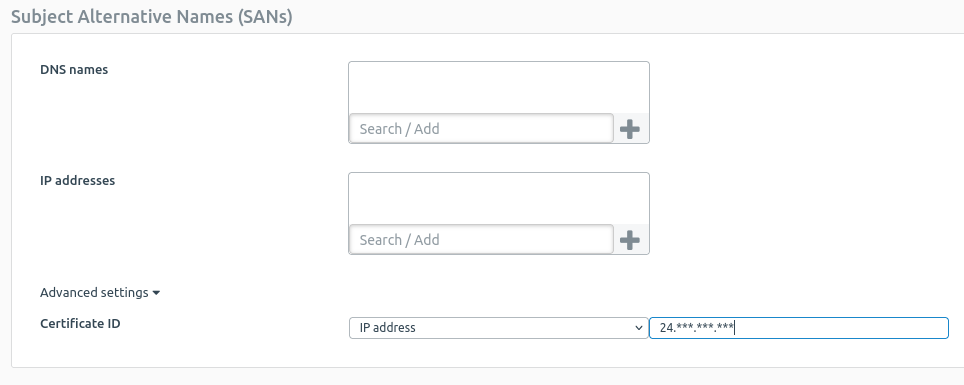
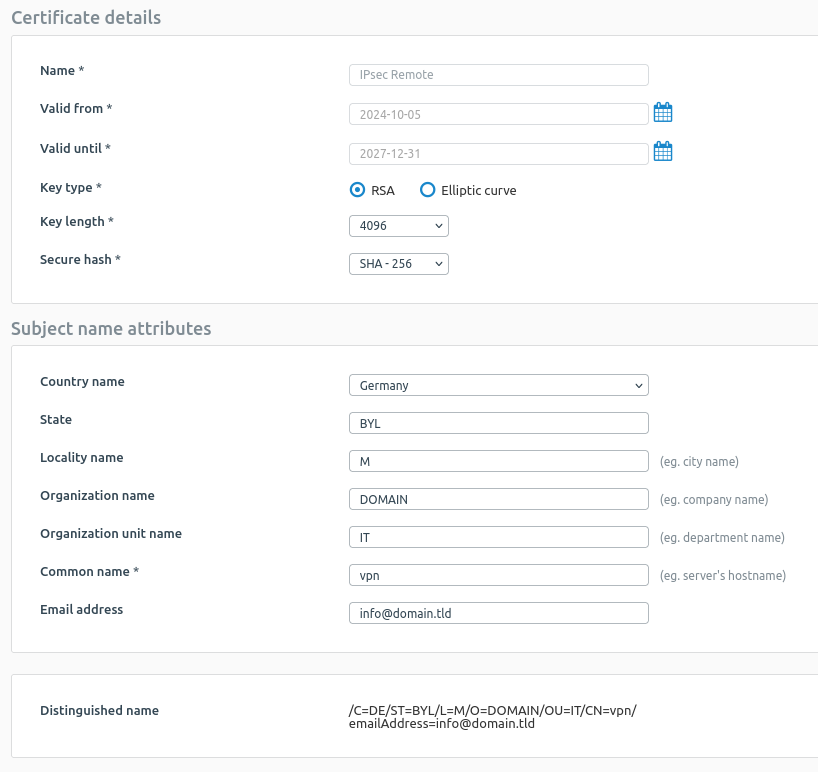
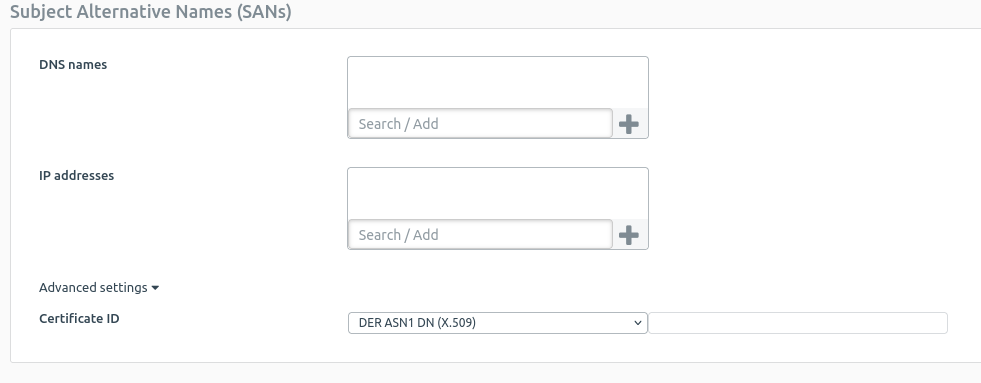
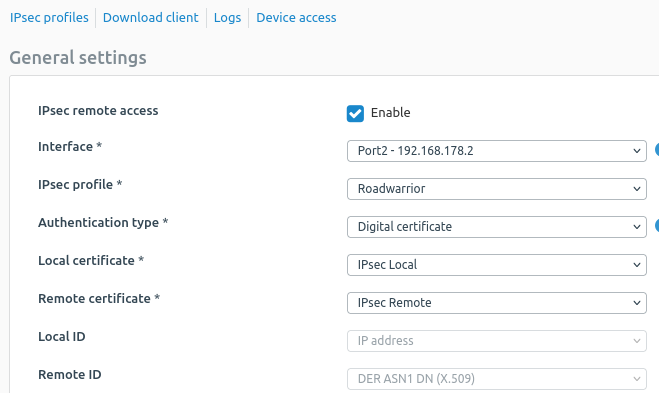
I have generated two locally-signed certificate in the Certificate's menu as explained in the knowledge base articles. The remote certificate using Advanced Settings > Certificate ID > DER ASN1 DN (X.509) and the local certificate using Advanced Settings > Certificate ID > DNS with the FQDN of the firewall.
Then I clicked Export Configuration and created three new files with the public key, private key and CA certificate and generated the required PFX file for iOS.
openssl pkcs12 -cafile ca.pem -inkey private.key -in public.pem -export -out ios.pfx
I imported the Certificate on my iPad, created the VPN profile and tried to connect. It says connecting for almost a minute and then disconnects with the error:
Received IKE message with invalid SPI (AA85045D). Deny Session: Couldn't authenticate the remote gateway. Check the authentication settings on both devices.
But it won't prompt for username / password.
Am I doing it wrong?
And why is IKEv2 still not supported? ugh :/
Edited TAGs
[edited by: Erick Jan at 11:07 PM (GMT -7) on 7 Oct 2024]