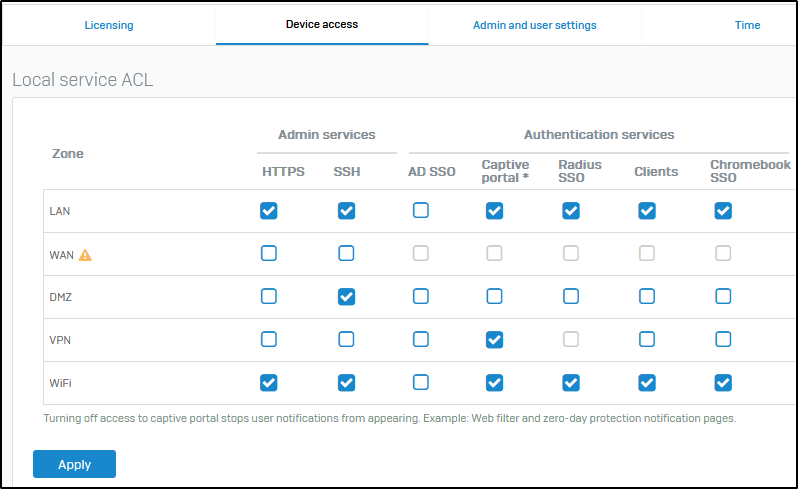
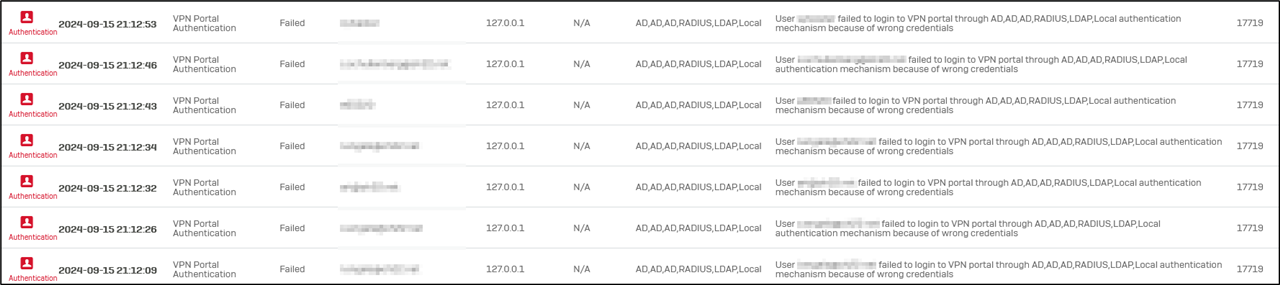
Hello,
We've seen a message on the Sophos Firewall WEB-UI leading us to this article:
"Multiple failed login (brute force) attempts for WAN-facing portals on Sophos Firewall"
https://support.sophos.com/support/s/article/KBA-000009932?language=en_US
We checked and indeed we see those (presumably) brute force attempts. The article now suggests to create an ACL exception rule to block the IPs or origin countries of the attackers. But it also states the following:
"Note: If the VPN portal and SSL VPN service share the same port and SSL VPN is enabled on WAN, the source IP for the failed login (brute force) attempt is shown as 127.0.0.1 in the log viewer."
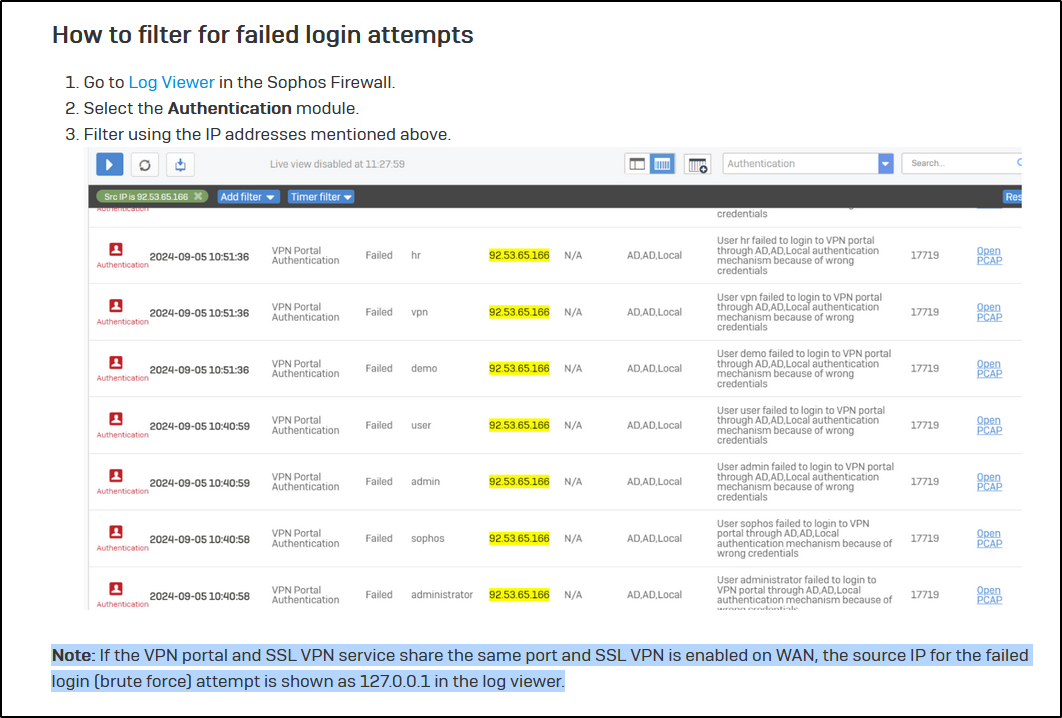
And that is exactly what's happening to us - the only thing we are seeing is 127.0.0.1.
Now my question is: How can we find out the correct IP and/or origin country of the attackers? The article is not giving any clue about how to do this.
Any help is much appreciated. Thanks!
Edited TAGs
[edited by: Erick Jan at 2:37 PM (GMT -7) on 17 Sep 2024]