We're seeing a lot of failed authentication attempts on the VPN portal, and we don't need users to access it once the VPN is setup and working. However, when I close down the "VPN Portal" from the WAN zone, no-one can connect to the SSLVPN. As soon as I re-enable this, everything starts working again.
My understanding was that the only thing that needs to be open is "SSL VPN" on the WAN zone.
I've done this before, so perhaps a bug in new firmware? We're on SFOS 20.0.2 MR-2-Build378 and I've tested and confirmed that this problem exists on multiple XGS devices on that firmware version.
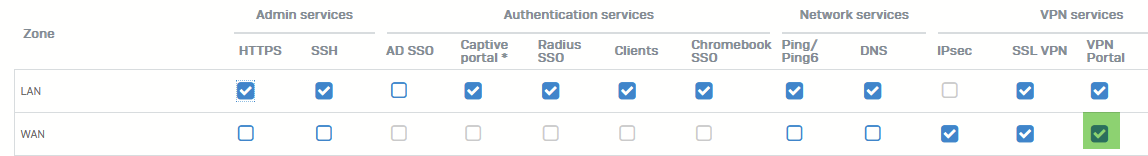
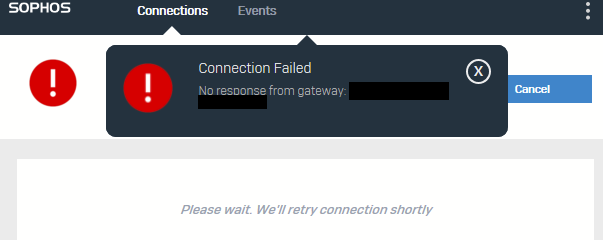
Also, the Sophos documentation is out of date. It still says you need to enable the User Portal - which you definitely don't.
Added TAGs
[edited by: Erick Jan at 9:53 AM (GMT -7) on 5 Sep 2024]


