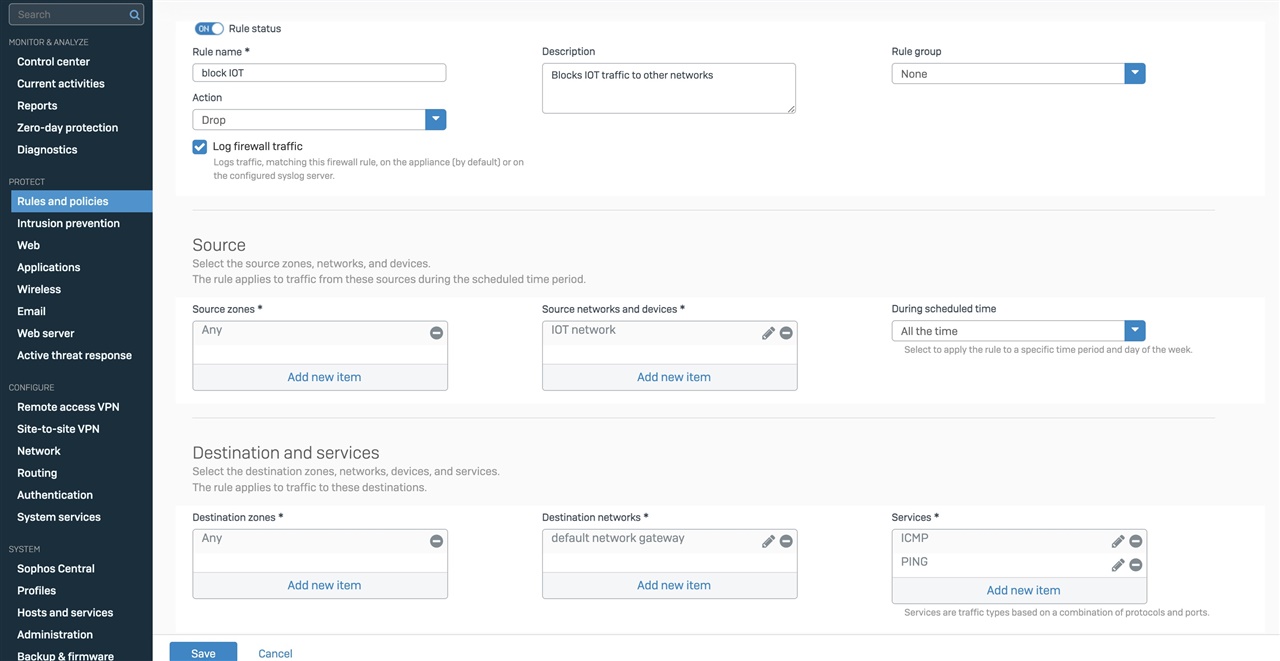
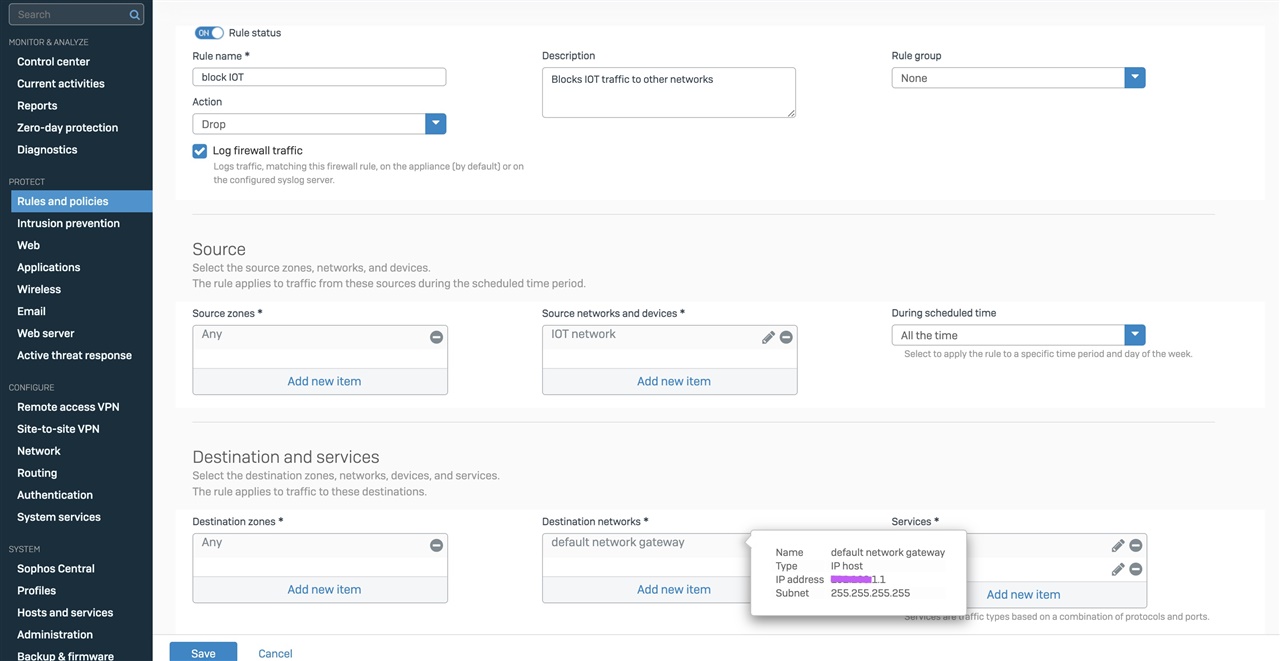
Hi, I am wanting to block the IOT network (xxx.xxx.5.xx/24) from pinging the default gateway of other networks so created a firewall rule to do so however when testing, devices in the IOT network are still able to ping the default gateway of other networks. I have also used the policy tester to test this and it is not picking up the firewall rule.
I have tried putting the firewall rule at the very top to make sure that it would pick it up.
I have attached images of the firewall policy created. Any help would be much appreciated.
This thread was automatically locked due to age.


