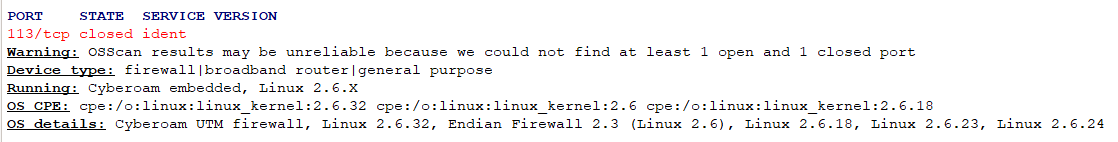
Sooo when scanning the system i've noticed 113 is the only port showing as closed / reject. Since the other ports are Drop I've created a rule to drop 113 from all connections but SFOS isn't honoring the rule. Why? Why would they decided to reject only 113?
This thread was automatically locked due to age.

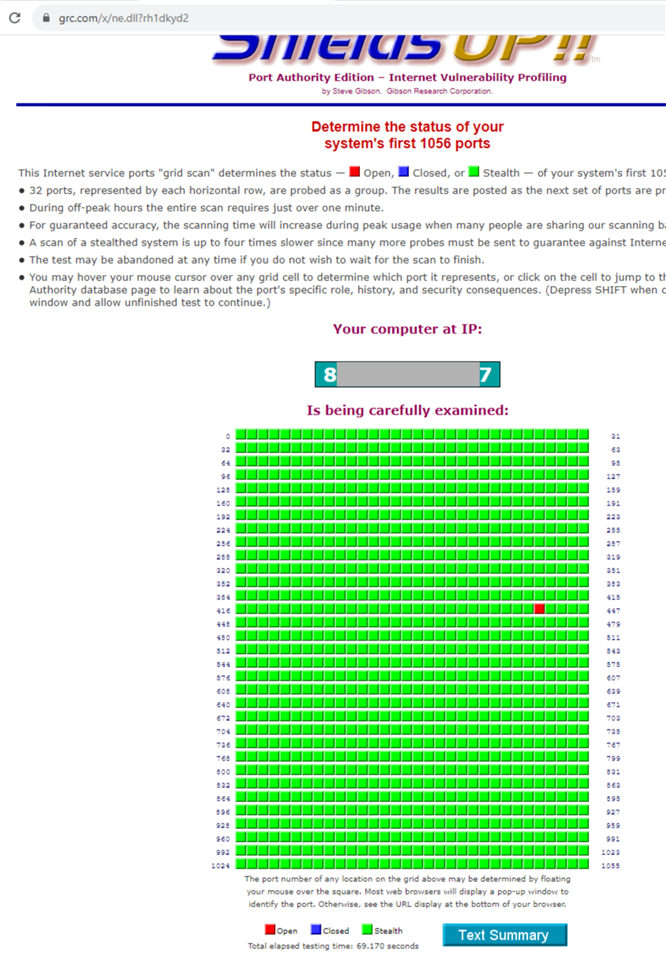



 Step One: Verify that our scan currently show port 113 stealthed. (You may wish to use one of the other remote port tests which will be faster than an entire 1056-port grid scan.)
Step One: Verify that our scan currently show port 113 stealthed. (You may wish to use one of the other remote port tests which will be faster than an entire 1056-port grid scan.) Step Two: Open a secondary web browser window to initiate a connection to the probing IP. (Users of Microsoft Internet Explorer can press Ctrl-N to "clone" their current browser window.)
Step Two: Open a secondary web browser window to initiate a connection to the probing IP. (Users of Microsoft Internet Explorer can press Ctrl-N to "clone" their current browser window.) Step Three: In the secondary web browser window, click this URL or enter this address:
Step Three: In the secondary web browser window, click this URL or enter this address:
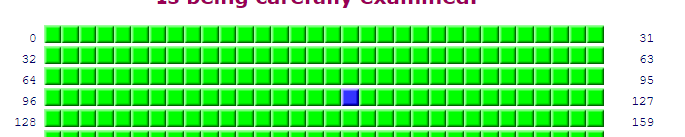
 Step Four: Finally, refresh the port probe window or repeat the scan to check your system's current port status. You should find that port 113 is no longer "stealth" to the probing IP address because you are attempting to connect to it and it has been determined to be "friendly".
Step Four: Finally, refresh the port probe window or repeat the scan to check your system's current port status. You should find that port 113 is no longer "stealth" to the probing IP address because you are attempting to connect to it and it has been determined to be "friendly". Step Five: If you're curious, stop and close the secondary web browser window and periodically refresh your port probe window to see how long the "friendly" status persists before Zone Alarm returns the probing IP to unknown status and port 113 to full stealth.
Step Five: If you're curious, stop and close the secondary web browser window and periodically refresh your port probe window to see how long the "friendly" status persists before Zone Alarm returns the probing IP to unknown status and port 113 to full stealth.
