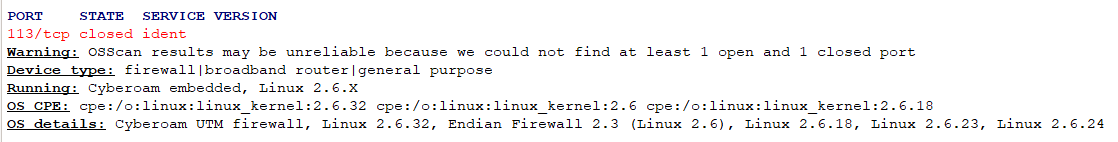
Sooo when scanning the system i've noticed 113 is the only port showing as closed / reject. Since the other ports are Drop I've created a rule to drop 113 from all connections but SFOS isn't honoring the rule. Why? Why would they decided to reject only 113?
This thread was automatically locked due to age.
